
- 505 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
About this book
Cloud Data Center Network Architectures and Technologies has been written with the support of Huawei's vast technical knowledge and experience in the data center network (DCN) field, as well as its understanding of customer service requirements. This book describes in detail the architecture design, technical implementation, planning and design, and deployment suggestions for cloud DCNs based on the service challenges DCNs encounter. It starts by describing the overall architecture and technical evolution of DCNs, with the aim of helping readers understand the development of DCNs. It then proceeds to explain the design and implementation of cloud DCNs, including the service model of a single data center (DC), construction of physical and logical networks of DCs, construction of multiple DCNs, and security solutions of DCs. Next, this book dives deep into practices of cloud DCN deployment based on real-world cases to help readers better understand how to build cloud DCNs. Finally, this book introduces DCN openness and some of the hottest forward-looking technologies.
In summary, you can use this book as a reference to help you to build secure, reliable, efficient, and open cloud DCNs. It is intended for technical professionals of enterprises, research institutes, information departments, and DCs, as well as teachers and students of computer network-related majors in colleges and universities.
Authors
Lei Zhang
Mr. Zhang is the Chief Architect of Huawei's DCN solution. He has more than 20 years' experience in network product and solution design, as well as a wealth of expertise in product design and development, network planning and design, and network engineering project implementation. He has led the design and deployment of more than 10 large-scale DCNs for Fortune Global 500 companies worldwide.
Le Chen
Mr. Chen is a Huawei DCN Solution Documentation Engineer with eight years' experience in developing documents related to DCN products and solutions. He has participated in the design and delivery of multiple large-scale enterprise DCNs. Mr. Chen has written many popular technical document series, such as DCN Handbook and BGP Topic.
Tools to learn more effectively

Saving Books

Keyword Search

Annotating Text

Listen to it instead
Information
CHAPTER 1
1.1 Cloud Computing
- On-demand self-service: Users can leverage self-services without any intervention from service providers.
- Broad network access: Users can access a network through various terminals.
- Resource pooling: Physical resources are shared by users, and resources in a pool are region-independent.
- Rapid elasticity: Resources can be quickly claimed or released.
- Measured service: Resource measurement, monitoring, and optimization are automatic.
1.2 Virtualization Technologies Introduced by Cloud Computing
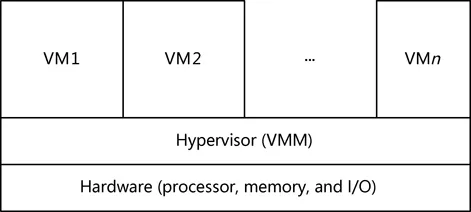
- Hypervisor
VM: runs on physical hardware and focuses on virtual I/O performance optimization. It is typically used for server applications. - Hosted
VM: runs on the OS of a PM and provides more upper-layer functions such as 3D acceleration. It is easy to both install and use, and is typically utilized for desktop applications.
- Full virtualizationAlso known as original virtualization. As shown in Figure 1.2, this model uses a
VM as the hypervisor to coordinate the guest OS and original hardware. The hypervisor obtains and processes virtualization-sensitive privileged instructions so that the guest OS can run without modification. As all privileged instructions are processed by the hypervisor, VMs offer lower performance than PMs. While such performance varies depending on implementation, it is usually sufficient to meet user requirements. With the help of hardware-assisted virtualization, full virtualization gradually overcomes its bottleneck. Typical hardware products include IBM CP/C MS, Oracle VirtualBox, KVM, VMware Workstation, and ESX. 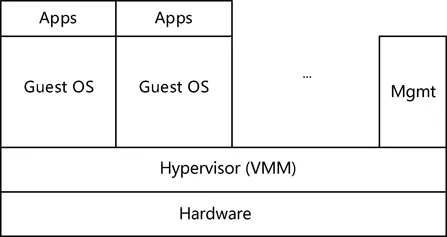 FIGURE 1.2 Full virtualization.
FIGURE 1.2 Full virtualization. - ParavirtualizationAlso known as hyper-virtualization. As shown in Figure 1.3, paravirtualization, similar to full virtualization, uses a hypervisor to implement shared access to underlying hardware. Unlike full virtualization, however, paravirtualization integrates virtualization-related code into the guest
OS so that it can work with the hypervisor to implement virtualization. In this way, the hypervisor does not need to recompile or obtain privileged instructions, and can achieve performance close to that of a PM. The most well-known product of this type is Xen. As Microsoft Hyper-V uses technologies similar to Xen, it can also be classified as paravirtualization. A weakness of paravirtualization is its requirement that a guest OS be modified, and only a limited number of guest OSs are supported, resulting in a poor user experience. 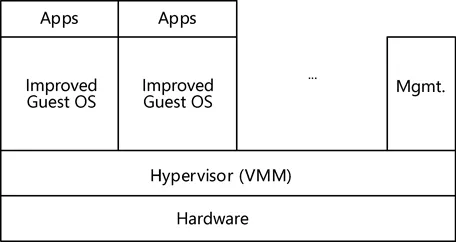 FIGURE 1.3 Paravirtualization.
FIGURE 1.3 Paravirtualization. - Hardware emulationThe most complex virtualization techno...
Table of contents
- Cover
- Half Title
- Series Page
- Title Page
- Copyright Page
- Table of Contents
- Summary
- Acknowledgments
- Authors
- Chapter 1 ▪ Introduction to Cloud DCNs
- Chapter 2 ▪ DCN Challenges
- Chapter 3 ▪ Architecture and Technology Evolution of DCNs
- Chapter 4 ▪ Functional Components and Service Models of Cloud DCNs
- Chapter 5 ▪ Constructing a Physical Network (Underlay Network) on a DCN
- Chapter 6 ▪ Constructing a Logical Network (Overlay Network) in a DC
- Chapter 7 ▪ Constructing a Multi-DC Network
- Chapter 8 ▪ Building E2E Security for Cloud DCNs
- Chapter 9 ▪ Best Practices of Cloud DCN Deployment
- Chapter 10 ▪ Openness of DCN
- Chapter 11 ▪ Cutting-Edge Technologies
- Chapter 12 ▪ Components of the Cloud DCN Solution
- Acronyms and Abbreviations
Frequently asked questions
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app