
Microservices Security in Action
- 616 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
Microservices Security in Action
About this book
"A complete guide to the challenges and solutions in securing microservices architectures." —Massimo Siani, FinDynamic Key Features
Secure microservices infrastructure and code
Monitoring, access control, and microservice-to-microservice communications
Deploy securely using Kubernetes, Docker, and the Istio service mesh.
Hands-on examples and exercises using Java and Spring Boot Purchase of the print book includes a free eBook in PDF, Kindle, and ePub formats from Manning Publications. Microservices Security in Action teaches you how to address microservices-specific security challenges throughout the system. This practical guide includes plentiful hands-on exercises using industry-leading open-source tools and examples using Java and Spring Boot. About The Book
Design and implement security into your microservices from the start. Microservices Security in Action teaches you to assess and address security challenges at every level of a Microservices application, from APIs to infrastructure. You'll find effective solutions to common security problems, including throttling and monitoring, access control at the API gateway, and microservice-to-microservice communication. Detailed Java code samples, exercises, and real-world business use cases ensure you can put what you've learned into action immediately. What You Will Learn Microservice security concepts
Edge services with an API gateway
Deployments with Docker, Kubernetes, and Istio
Security testing at the code level
Communications with HTTP, gRPC, and Kafka This Book Is Written For
For experienced microservices developers with intermediate Java skills. About The Author
Prabath Siriwardena is the vice president of security architecture at WSO2. Nuwan Dias is the director of API architecture at WSO2. They have designed secure systems for many Fortune 500 companies. Table of Contents PART 1 OVERVIEW
1 Microservices security landscape
2 First steps in securing microservices PART 2 EDGE SECURITY
3 Securing north/south traffic with an API gateway
4 Accessing a secured microservice via a single-page application
5 Engaging throttling, monitoring, and access control PART 3 SERVICE-TO-SERVICE COMMUNICATIONS
6 Securing east/west traffic with certificates
7 Securing east/west traffic with JWT
8 Securing east/west traffic over gRPC
9 Securing reactive microservices PART 4 SECURE DEPLOYMENT
10 Conquering container security with Docker
11 Securing microservices on Kubernetes
12 Securing microservices with Istio service mesh PART 5 SECURE DEVELOPMENT
13 Secure coding practices and automation
Tools to learn more effectively

Saving Books

Keyword Search

Annotating Text

Listen to it instead
Information
Part 1. Overview
1 Microservices security landscape
- Why microservices security is challenging
- Principles and key elements of a microservices security design
- Edge security and the role of an API gateway
- Patterns and practices in securing service-to-service communications
1.1 How security works in a monolithic application
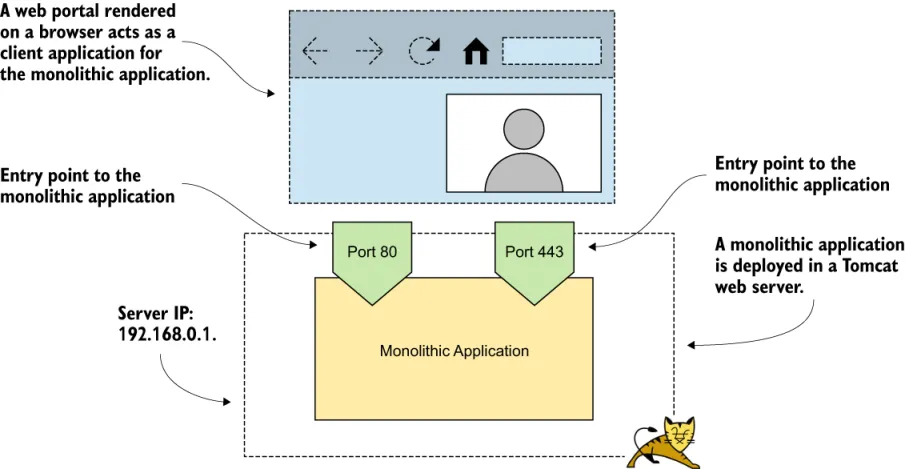
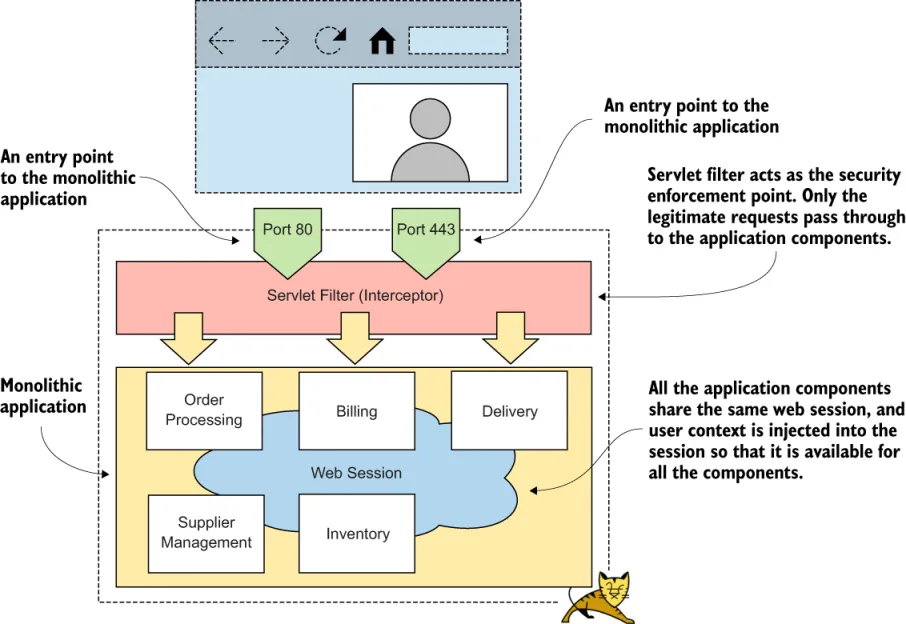
1.2 Challenges of securing microservices
Table of contents
- Microservices Security in Action
- Copyright
- dedication
- brief contents
- contents
- front matter
- Part 1. Overview
- 1 Microservices security landscape
- 2 First steps in securing microservices
- Part 2. Edge security
- 3 Securing north/south traffic with an API gateway
- 4 Accessing a secured microservice via a single-page application
- 5 Engaging throttling, monitoring, and access control
- Part 3. Service-to-service communications
- 6 Securing east/west traffic with certificates
- 7 Securing east/west traffic with JWT
- 8 Securing east/west traffic over gRPC
- 9 Securing reactive microservices
- Part 4. Secure deployment
- 10 Conquering container security with Docker
- 11 Securing microservices on Kubernetes
- 12 Securing microservices with Istio service mesh
- Part 5. Secure development
- 13 Secure coding practices and automation
- Appendix A. OAuth 2.0 and OpenID Connect
- Appendix B. JSON Web Token
- Appendix C. Single-page application architecture
- Appendix D. Observability in a microservices deployment
- Appendix E. Docker fundamentals
- Appendix F. Open Policy Agent
- Appendix G. Creating a certificate authority and related keys with OpenSSL
- Appendix H. Secure Production Identity Framework for Everyone
- Appendix I. gRPC fundamentals
- Appendix J. Kubernetes fundamentals
- Appendix K. Service mesh and Istio fundamentals
- index
Frequently asked questions
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app