
(ISC)2 CISSP Certified Information Systems Security Professional Official Study Guide
Mike Chapple, James Michael Stewart, Darril Gibson
- English
- ePUB (mobile friendly)
- Available on iOS & Android
(ISC)2 CISSP Certified Information Systems Security Professional Official Study Guide
Mike Chapple, James Michael Stewart, Darril Gibson
About This Book
The only Official CISSP Study Guide - fully updated for the 2021 CISSP Body of Knowledge
(ISC)2 Certified Information Systems Security Professional (CISSP) Official Study Guide, 9th Edition has been completely updated based on the latest 2021 CISSP Exam Outline. This bestselling Sybex Study Guide covers 100% of the exam objectives. You'll prepare for the exam smarter and faster with Sybex thanks to expert content, knowledge from our real-world experience, advice on mastering this adaptive exam, access to the Sybex online interactive learning environment, and much more. Reinforce what you've learned with key topic exam essentials and chapter review questions.
The three co-authors of this book bring decades of experience as cybersecurity practitioners and educators, integrating real-world expertise with the practical knowledge you'll need to successfully pass the CISSP exam. Combined, they've taught cybersecurity concepts to millions of students through their books, video courses, and live training programs.
Along with the book, you also get access to Sybex's superior online interactive learning environment that includes:
- Over 900 new and improved practice test questions with complete answer explanations. This includes all of the questions from the book plus four additional online-only practice exams, each with 125 unique questions. You can use the online-only practice exams as full exam simulations. Our questions will help you identify where you need to study more. Get more than 90 percent of the answers correct, and you're ready to take the certification exam.
- More than 700 Electronic Flashcards to reinforce your learning and give you last-minute test prep before the exam
- A searchable glossary in PDF to give you instant access to the key terms you need to know for the exam
- New for the 9th edition: Audio Review. Author Mike Chapple reads the Exam Essentials for each chapter providing you with 2 hours and 50 minutes of new audio review for yet another way to reinforce your knowledge as you prepare.
All of the online features aresupported by Wiley's support agents who are available 24x7 via email or live chat to assist with access and login questions.
Coverage of all of the exam topics in the book means you'll be ready for:
- Security and Risk Management
- Asset Security
- Security Architecture and Engineering
- Communication and Network Security
- Identity and Access Management (IAM)
- Security Assessment and Testing
- Security Operations
- Software Development Security
Frequently asked questions
Information
Chapter 1
Security Governance Through Principles and Policies
- Domain 1.0: Security and Risk Management
- 1.2 Understand and apply security concepts
- 1.2.1 Confidentiality, integrity, and availability, authenticity and nonrepudiation
- 1.3 Evaluate and apply security governance principles
- 1.3.1 Alignment of security function to business strategy, goals, mission, and objectives
- 1.3.2 Organizational processes (e.g., acquisitions, divestitures, governance committees)
- 1.3.3 Organizational roles and responsibilities
- 1.3.4 Security control frameworks
- 1.3.5 Due care/due diligence
- 1.7 Develop, document, and implement security policy, standards, procedures, and guidelines
- 1.11 Understand and apply threat modeling concepts and methodologies
- 1.12 Apply Supply Chain Risk Management (SCRM) concepts
- 1.12.1 Risks associated with hardware, software, and services
- 1.12.2 Third-party assessment and monitoring
- 1.12.3 Minimum security requirements
- 1.12.4 Service level requirements
- 1.2 Understand and apply security concepts
- Domain 3: Security Architecture and Engineering
- 3.1 Research, implement and manage engineering processes using secure design principles
- 3.1.1 Threat modeling
- 3.1.3 Defense in depth
- 3.1 Research, implement and manage engineering processes using secure design principles

Security 101
Understand and Apply Security Concepts
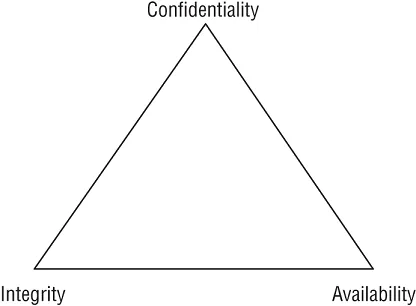
Confidentiality
- Sensitivity Sensitivity refers to the quality of information, which could cause harm or damage if disclosed.
- Discretion Discretion is an act of decision where an operator can influence or control disclosure in order to minimize harm or damage.
- Criticality The level to which information is mission critical is its measure of criticality. The higher the level of criticality, the more likely the need to maintain the confidentiality of the information.
- Concealment Concealment is the act of hiding or preventing disclosure. Often concealment is viewed as a means of cover, obfuscation, or distraction. A related concept to concealment is security through obscurity, which is the concept of attempting to gain protection through hiding, silence, or secrecy.
- Secrecy Secrecy is the act of keeping something a secret or preventing the disclosure of information.
- Privacy Privacy refers to keeping information confidential that is personally identifiable or that might cause harm, embarrassment, or disgrace to s...