
- 282 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
Malware Analysis Techniques
About this book
Analyze malicious samples, write reports, and use industry-standard methodologies to confidently triage and analyze adversarial software and malwareKey Features• Investigate, detect, and respond to various types of malware threat• Understand how to use what you've learned as an analyst to produce actionable IOCs and reporting• Explore complete solutions, detailed walkthroughs, and case studies of real-world malware samplesBook DescriptionMalicious software poses a threat to every enterprise globally. Its growth is costing businesses millions of dollars due to currency theft as a result of ransomware and lost productivity. With this book, you'll learn how to quickly triage, identify, attribute, and remediate threats using proven analysis techniques. Malware Analysis Techniques begins with an overview of the nature of malware, the current threat landscape, and its impact on businesses. Once you've covered the basics of malware, you'll move on to discover more about the technical nature of malicious software, including static characteristics and dynamic attack methods within the MITRE ATT&CK framework. You'll also find out how to perform practical malware analysis by applying all that you've learned to attribute the malware to a specific threat and weaponize the adversary's indicators of compromise (IOCs) and methodology against them to prevent them from attacking. Finally, you'll get to grips with common tooling utilized by professional malware analysts and understand the basics of reverse engineering with the NSA's Ghidra platform. By the end of this malware analysis book, you'll be able to perform in-depth static and dynamic analysis and automate key tasks for improved defense against attacks.What you will learn• Discover how to maintain a safe analysis environment for malware samples• Get to grips with static and dynamic analysis techniques for collecting IOCs• Reverse-engineer and debug malware to understand its purpose• Develop a well-polished workflow for malware analysis• Understand when and where to implement automation to react quickly to threats• Perform malware analysis tasks such as code analysis and API inspectionWho this book is forThis book is for incident response professionals, malware analysts, and researchers who want to sharpen their skillset or are looking for a reference for common static and dynamic analysis techniques. Beginners will also find this book useful to get started with learning about malware analysis. Basic knowledge of command-line interfaces, familiarity with Windows and Unix-like filesystems and registries, and experience in scripting languages such as PowerShell, Python, or Ruby will assist with understanding the concepts covered.
Tools to learn more effectively

Saving Books

Keyword Search

Annotating Text

Listen to it instead
Information
Section 1: Basic Techniques
- Chapter 1, Creating and Maintaining Your Detonation Environment
- Chapter 2, Static Analysis – Techniques and Tooling
- Chapter 3, Dynamic Analysis – Techniques and Tooling
- Chapter 4, A Word on Automated Sandboxing
Chapter 1: Creating and Maintaining your Detonation Environment
- How do we execute and study malicious code while ensuring our real environments remain safe and we do not assist the malware authors in propagating their code?
- What tools do we require to ensure that we're able to adequately study the malware?
- How do we achieve the two aforementioned goals in a repeatable fashion so that we do not have to rebuild our environment after every piece of malware we study?
- Setting up VMware Workstation with Windows 10
- Tooling installation – FLARE
- Isolating your environment
- Maintenance and snapshotting
Technical requirements
- A PC/Mac with at least 8 GB of memory and a quad-core processor
- An internet connection
- FLARE VM GitHub package: https://github.com/fireeye/flare-vm
- The latest VirtualBox installer: https://virtualbox.org/wiki/downloads
- A Windows 10 ISO and product key
Setting up VirtualBox with Windows 10

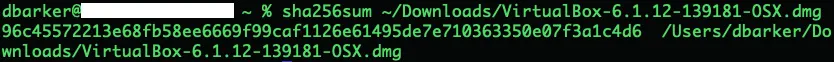
Downloading and verifying VirtualBox

Installing Windows 10

Table of contents
- Malware Analysis Techniques
- Contributors
- Preface
- Section 1: Basic Techniques
- Chapter 1: Creating and Maintaining your Detonation Environment
- Chapter 2: Static Analysis – Techniques and Tooling
- Chapter 3: Dynamic Analysis – Techniques and Tooling
- Chapter 4: A Word on Automated Sandboxing
- Section 2: Debugging and Anti-Analysis – Going Deep
- Chapter 5: Advanced Static Analysis – Out of the White Noise
- Chapter 6: Advanced Dynamic Analysis – Looking at Explosions
- Chapter 7: Advanced Dynamic Analysis Part 2 – Refusing to Take the Blue Pill
- Chapter 8: De-Obfuscating Malicious Scripts: Putting the Toothpaste Back in the Tube
- Section 3: Reporting and Weaponizing Your Findings
- Chapter 9: The Reverse Card: Weaponizing IOCs and OSINT for Defense
- Chapter 10: Malicious Functionality: Mapping Your Sample to MITRE ATT&CK
- Section 4: Challenge Solutions
- Chapter 11: Challenge Solutions
- Other Books You May Enjoy
Frequently asked questions
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app