
eBook - ePub
Hacking of Computer Networks
Full Course on Hacking of Computer Networks
- 288 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
eBook - ePub
Hacking of Computer Networks
Full Course on Hacking of Computer Networks
About this book
The objective of the book is to summarize to the user with main topics in computer networking hacking.The book consists of the following parts: Part 1: Lab SetupPart2: Foot printing and ReconnaissancePart 3: Scanning MethodologyPart 4: EnumerationPart 5: System HackingPart 6: Trojans and Backdoors and VirusesPart 7: Sniffer and Phishing HackingPart 8: Hacking Web ServersPart 9: Hacking Windows and Linux SystemsPart 10: Wireless HackingPart 11: Hacking Mobile Applications
Frequently asked questions
Yes, you can cancel anytime from the Subscription tab in your account settings on the Perlego website. Your subscription will stay active until the end of your current billing period. Learn how to cancel your subscription.
No, books cannot be downloaded as external files, such as PDFs, for use outside of Perlego. However, you can download books within the Perlego app for offline reading on mobile or tablet. Learn more here.
Perlego offers two plans: Essential and Complete
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
We are an online textbook subscription service, where you can get access to an entire online library for less than the price of a single book per month. With over 1 million books across 1000+ topics, we’ve got you covered! Learn more here.
Look out for the read-aloud symbol on your next book to see if you can listen to it. The read-aloud tool reads text aloud for you, highlighting the text as it is being read. You can pause it, speed it up and slow it down. Learn more here.
Yes! You can use the Perlego app on both iOS or Android devices to read anytime, anywhere — even offline. Perfect for commutes or when you’re on the go.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app.
Yes, you can access Hacking of Computer Networks by Dr. Hidaia Mahmood Alassouli in PDF and/or ePUB format, as well as other popular books in Computer Science & Cyber Security. We have over one million books available in our catalogue for you to explore.
Information
Part 1: Setup Lab
1) Setup lab
- From the virtualization technology with software VMware or virtual box we can do more than one virtual machines, one linux and other windows 2007 or windows Xp
- Download vmware and install it
- Create folder edurs-vm in non-windows partition. Create a folder for each operating system
- Install any windows operating system.
- Download backtrack
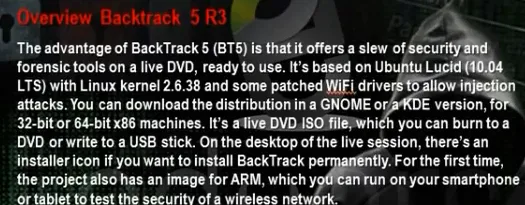
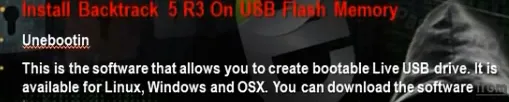
- To install backtrack on usb, download unebootin. We need also to use the tool to support booting from flash memory in vmware.
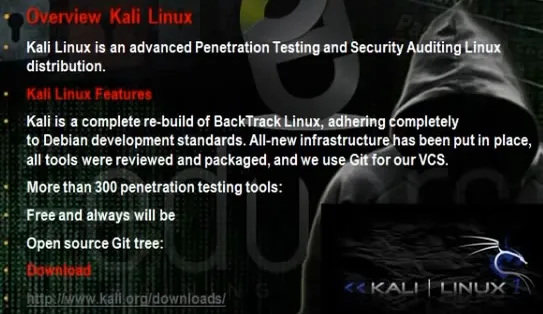
- Download and install kali linux
- Download and install metasploit.
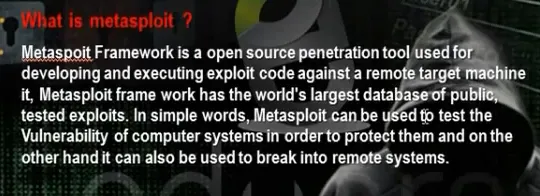
Metasploit is big project that contains a lot of modules or programs. These modules or programs can utilize the holes in windows machines or linux machines operating systems. For any hole that occur in the operating systems, we can develop the program that can utilize this hole. We can work on it through command line or graphical interface. The programs that use graphical interface are armitage and Koblet Strike . In linux we can update the metasploite using command msfupdate.
Part 2: Foot printing and Reconnaissance
Part 2 of Certified Ethical Hacker (CEH) Course
By
Dr. Hidaia Mahmood Alassouli
Part 2: Foot printing and Reconnaissance
1)Footprinting and Reconnaissance
- Use nslookup to get information about server.
- see dnsstuf to get information about server domain .
- Use www.ip-address.com to get information about server.
- Use www.robtex.com to get information about server domain.
- Use backtack or any linux machine to know the dns servers of certain domain. For example,
Dig –t NS Wikimedia.org
- Use backtack or any linux machine to know the A and MX records of certain domain. For example,
Dig –t A Wikimedia.org
Dig –t MX Wikimedia.org
- To see the zone transfer
Dig –t AXFR Wikimedia.org @ ns1.wikimedia.org
- We can see all the records in that dns server.
- We can use the nslookup command to see the host of certain ip address
Nslookup –type= ptr 31.13.81.17
- We can use who.is to know information about server, when created , and when expired and all information about that the dns servers of domain and about the administrator. You can get the same information from backtrack terminal. Write
whois Microsoft.com
- We can use tool called smartwhois to get same information.
- We can use tool called countrywhois to get information about country of a domain.
- We can use tool called lanwhois to get same information from who.is.
- There is tool called alchemy eye to make monitoring for certain services in a target server. It can check the status of certain services on a server.
- Use robots.txt file to know what is not allowed on the website. Eg www.microsoft.com/robots.txt
- To search site in google write eg, site:tedata.com filetype:pdf. You can search the following in google
Intitele: search in the title page
Inurl: search in the url page
Site: search on site
Link: other sites that links to our subject
Inanchor: search on hyperlinks
Filetype: search to see pattern yet
- There is google hacking dat...
Table of contents
- Ethical Computer Networking Hacking
- Author Biography
- Part 1: Setup Lab
- Part 2: Foot printing and Reconnaissance
- Part 2: Foot printing and Reconnaissance
- Part 3: Scanning Methodology
- Part 3: Scanning Methodology
- Part 4: Enumeration
- Part 4: Enumeration
- Part 5: System Hacking
- Part 5: System Hacking
- Part 6: Trojens and Backdoors and Viruses
- Part 6: Trojens and Backdoors and Viruses
- Part 7: Sniffer and Phishing Hacking
- Part 7: Sniffer and Phishing Hacking
- Part 8: Hacking Web Servers
- Part 8: Hacking Web Servers
- Part 9: Hacking Windows and Linux Systems
- Part 9: Windows and Linux Hacking
- Part 10: Wireless Hacking
- Part 10: Wireless Hacking Networks in Linux
- Part 11: Hacking Mobile Applications
- Part 11: Mobile Platforms Hacking