
Implementing Reverse Engineering
The Real Practice of X86 Internals, Code Calling Conventions, Ransomware Decryption, Application Cracking, Assembly Language, and Proven Cybersecurity Open Source Tools
- English
- ePUB (mobile friendly)
- Available on iOS & Android
Implementing Reverse Engineering
The Real Practice of X86 Internals, Code Calling Conventions, Ransomware Decryption, Application Cracking, Assembly Language, and Proven Cybersecurity Open Source Tools
About this book
More practical less theory
Key Features
? In-depth practical demonstration with multiple examples of reverse engineering concepts.
? Provides a step-by-step approach to reverse engineering, including assembly instructions.
? Helps security researchers to crack application code and logic using reverse engineering open source tools.
? Reverse engineering strategies for simple-to-complex applications like Wannacry ransomware and Windows calculator.
Description
The book 'Implementing Reverse Engineering' begins with a step-by-step explanation of the fundamentals of reverse engineering. You will learn how to use reverse engineering to find bugs and hacks in real-world applications. This book is divided into three sections. The first section is an exploration of the reverse engineering process. The second section explains reverse engineering of applications, and the third section is a collection of real-world use-cases with solutions.The first section introduces the basic concepts of a computing system and the data building blocks of the computing system. This section also includes open-source tools such as CFF Explorer, Ghidra, Cutter, and x32dbg. The second section goes over various reverse engineering practicals on various applications to give users hands-on experience. In the third section, reverse engineering of Wannacry ransomware, a well-known Windows application, and various exercises are demonstrated step by step. What you will learn
? Understand different code calling conventions like CDECL, STDCALL, and FASTCALL with practical illustrations.
? Analyze and break WannaCry ransomware using Ghidra.
? Using Cutter, reconstruct application logic from the assembly code.
? Hack the Windows calculator to modify its behavior.
Who this book is for
This book is for cybersecurity researchers, bug bounty hunters, software developers, software testers, and software quality assurance experts who want to perform reverse engineering for advanced security from attacks. Interested readers can also be from high schools or universities (with a Computer Science background). Basic programming knowledge is helpful but not required.
Table of Contents
1. Impact of Reverse Engineering
2. Understanding Architecture of x86 machines
3. Up and Running with Reverse Engineering tools
4. Walkthrough on Assembly Instructions
5. Types of Code Calling Conventions
6. Reverse Engineering Pattern of Basic Code
7. Reverse Engineering Pattern of the printf() Program
8. Reverse Engineering Pattern of the Pointer Program
9. Reverse Engineering Pattern of the Decision Control Structure
10. Reverse Engineering Pattern of the Loop Control Structure
11. Array Code Pattern in Reverse Engineering
12. Structure Code Pattern in Reverse Engineering
13. Scanf Program Pattern in Reverse Engineering
14. strcpy Program Pattern in Reverse Engineering
15. Simple Interest Code Pattern in Reverse Engineering
16. Breaking Wannacry Ransomware with Reverse Engineering
17. Generate Pseudo Code from the Binary File
18. Fun with Windows Calculator Using Reverse Engineering
About the Authors
Jitender Narula is an experienced Cyber Security Specialist currently associated with the International Institute of Cyber Security (www.iicybersecurity.com) having 18+ years of industry experience. He has many years of cybersecurity experience with the government and the corporate world. In India, he has worked for law enforcement agencies (LEA), government entities like Delhi Police, ICAI (Institute of Chartered Accountants of India), Delhi University, and private organizations. LinkedIn Profile: https://in.linkedin.com/in/jitender-narula-7146123
Blog Link: https://www.securitynewspaper.com/2020/04/24/employee-data-leaked-apple-google-microsoftlinkedin-intel-cisco-verizon-oracle-hp-nvidia-affected/
Tools to learn more effectively

Saving Books

Keyword Search

Annotating Text

Listen to it instead
Information
CHAPTER 1
Impact of Reverse Engineering
Structure
- Introduction to Reverse Engineering
- Importance of Reverse Engineering
- The Role of Reverse Engineering
Objective
Introduction to Reverse Engineering
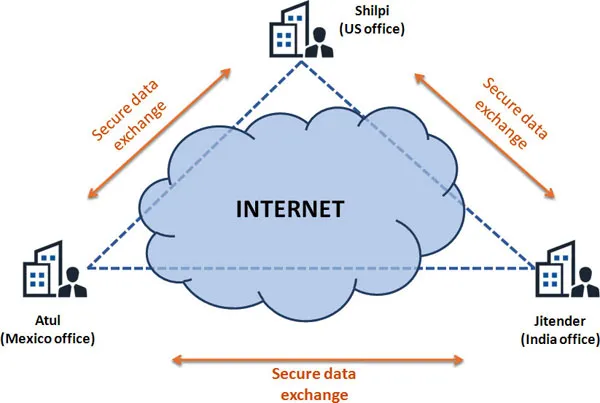
Importance of Reverse Engineering
Studying an existing design
Redeveloping an outdated or lost product
Security auditing
Finding sensitive data
Military espionage
Finding product vulnerabilities
Bounty for cyber enthusiasts
The Role of Reverse Engineering
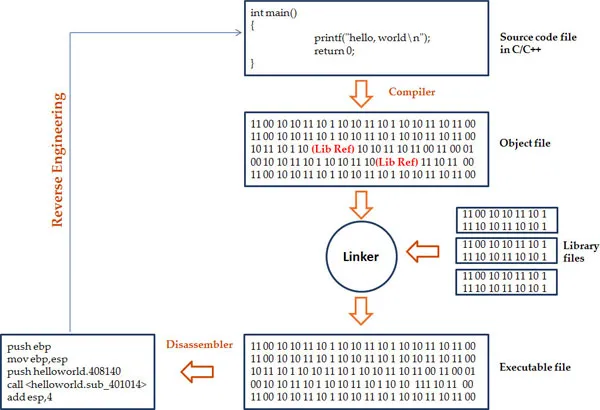
Conclusion
CHAPTER 2
Understanding Architecture of x86 Machines
Table of contents
- Cover Page
- Title Page
- Copyright Page
- Dedication Page
- About the Author
- About the Reviewer
- Acknowledgement
- Preface
- Errata
- Table of Contents
- 1. Impact of Reverse Engineering
- 2. Understanding Architecture of x86 Machines
- 3. Up and Running with Reverse Engineering Tools
- 4. Walk Through on Assembly Instructions
- 5. Types of Code Calling Conventions
- 6. Reverse Engineering Pattern of Basic Code
- 7. Reverse Engineering Pattern of Printf Program
- 8. Reverse Engineering Pattern of Pointer Program
- 9. Reverse Engineering Pattern of Decision Control Structure
- 10. Reverse Engineering Pattern of Loop Control Structure
- 11. Array Code Pattern in Reverse Engineering
- 12. Structure Code Pattern in Reverse Engineering
- 13. Scanf Program Pattern in Reverse Engineering
- 14. Strcpy Program Pattern in Reverse Engineering
- 15. Simple Interest Code Pattern in Reverse Engineering
- 16. Breaking Wannacry Ransomware With Reverse Engineering
- 17. Generate Pseudo Code From Binary File
- 18. Fun With Windows Calculator Using Reverse Engineering
- Appendix
- Index
Frequently asked questions
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app