![]()
Who is this book for?
This book is intended for any professional who is interested in protecting their business or property from ransomware. The whole point is to distribute this publication as widely as possible to mitigate as many ransomware attacks as possible and starve attackers of their resources.
I have organized this book in a stepwise fashion walking you through what ransomware is, defining the methods which protect you from ransomware, explaining how to implement that methodology properly, and finally, how to handle a ransomware attack on your business.
This publication is heavily cited for good purpose. It shows all of the data points provided by research firms that studied ransomware attacks. Further, the data regarding the success of recovering from an attack provides empirical evidence of what works and what does not work. This data-driven approach allows you to prepare to make quick decisions when your business is suffering downtime. The data will make it clear which choices benefit businesses and which choices do not.
Read carefully and consider how your organization can improve its protection mechanisms. Carry this book with you. Have a copy at your desk. Give a copy to your friends and colleagues. Together, we can reverse the prevalence of ransomware attacks and turn back the trend of the explosive growth of ransomware!
Chapter 1
What is Ransomware?
Ransomware is a type of malicious software that leverages encryption and exfiltration of data to take advantage of an organization’s documents, files, or other digital property. An attacker encrypts the victim’s data and then demands a ransom to provide access to the encrypted data. Cybercriminals usually demand that victims pay in cryptocurrency and oftentimes over the dark web.
Ransomware uses modern encryption technology. A variety of encryption mechanisms are used and there is no point to doing a deep dive on these mechanisms. The main point is that the encryption key acts as a mechanism to lock and unlock data that you may want encrypted or decrypted. In the case of ransomware, upon receipt of the ransom payment, attackers tend to give the victim the decryption key or a decryption tool so that they can again access their files, although this is not always the case. Some attackers simply take the ransom, and the victims do not get access to their data again.
There are several well-known types of ransomware, which will be covered later on. Most often, ransomware attacks are generated through email spam campaigns and phishing through fraudulent websites. Recent reports have shown that the complexity of phishing campaigns is increasing, making phishing harder to detect both by software and end-users.
Once a system is exposed to ransomware, the malware is executed and starts to search for a file system to attack. These file systems could be anything on the local network, including images, audio files, valuable business documents, databases, and anything stored on a hard drive or solid-state disk (SSD).
When data is located and encrypted, the ransomware notifies the user that a ransom must be paid within a specific time frame for the files to be decrypted. In addition, various threats, which will be covered, also tend to be made regarding the fate of the victim’s data if a ransom is not paid.
The Increased Frequency of Ransomware Attacks
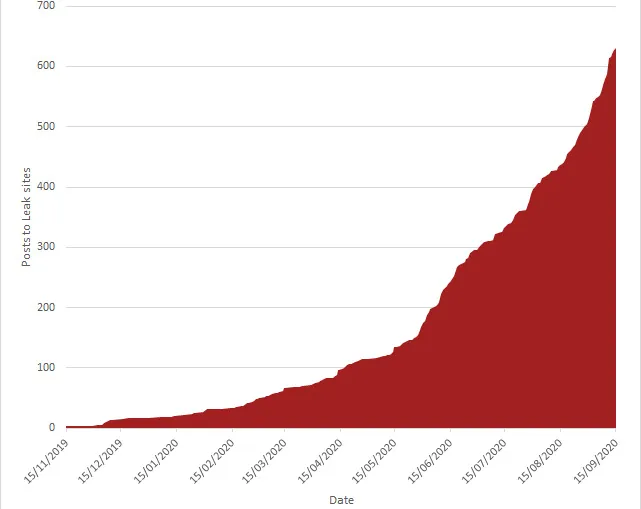
Unfortunately, ransomware attacks are on the rise, as several organizations and publications have documented. A recent report published by PwC has shown a long-term rise in the number of ransomware-based attacks1. Another survey carried out by Cloudwards2, showed that of all the businesses surveyed, 51% of those fell victim to ransomware in 2020. Figure 1 shows the steep rise in attacks.
Figure 1- The rise of ransomware attacks, source: PwC - What’s behind the increase in ransomware attacks this year?
The reason ransomware attacks are rising is due to a relatively new trend: ransomware kits are being sold on the Darknet for around $502. This means that the barrier to entry for an attacker is becoming lower as less and less technical knowledge is needed to carry out an attack. The UK Government’s National Cyber Security Center has also reported, “in the last 3 years, there’s been a real explosion of growth”3.
Within the top 3 types of organizations that have been experiencing the most growth in attacks is;
1.Retail at 14.8% of the attacks
2.Manufacturing at 13.4%
3.Financial services firms at 11.4% of ransomware attacks
The attacks are so frequent that an organization falls victim to a ransomware attack every 11 seconds2.
The Increased Size of Ransomware Demands
In addition to the frequency of attacks skyrocketing, the monetary demands are also rising. The average ransom payment for small and medium-sized enterprises was $5,900, while the overall average is $178,000, which is a 37% year-over-year increase4. The highest confirmed ransom payment in recent history was $11.8 million.
Apple is currently being extorted for product design documentation. Reports from various news agencies are stating that the ransom is between $50 and $100 million. If this is confirmed in the future, this event alone will drastically change the landscape of ransomware attacks.
An additional scenario involving a gasoline distributor, Colonial Pipeline, involves ransomware as well. Few details regarding the exact situation and internal information are known. However, this marks a massive shift in ransomware cases whereby critical infrastructure is directly impacted, which has further knock-on effects. This specific one is analyzed in a case study towards the end of the book because of its unique scenario.
Depending on the data sources, between 25% and 26% of all victims paid a ransom to an attacker.
Quantifying the Total Average Cost of a Ransomware Attack
To understand the full impact of what ransomware can do to an organization, we have to take a look at several factors quantifying the average cost of an attack. Various calculations went into the figure, which will be explained later. One crucial figure that can’t necessarily be quantified is the value or cost of the lost data. The good news is that roughly 94% of companies end up recovering their data through one process or another. However, no information described the 6% of the victims which could not recover their data. Some companies that business models rely on data could literally see the end of their business if their data remains inaccessible. So for them, their proprietary data is invaluable. The ways businesses leverage data depend heavily on the business model and how the business’s day-to-day operations actually run. However, most businesses leverage digitalization to some degree today to stay competitive.
The total impact of ransomware reaches several aspects of a business. The most obvious and direct business impact is downtime. Additional factors are personnel costs, hardware costs, lost opportunities, reputational costs, third-party costs, and the ransom paid. According to a report which surveyed over 5,000 IT managers across 30 countries, who have directly dealt with ransomware, the total average cost for dealing with a ransomware-based security event is $732,520 for companies that do not pay the ransom (remember this for later).
For organizations that do pay the ransom, the cost is significantly greater at roughly double, coming...