
- English
- ePUB (mobile friendly)
- Available on iOS & Android
About this book
Prepare for success on the new PenTest+ certification exam and an exciting career in penetration testing
In the revamped Second Edition of CompTIA PenTest+ Study Guide: Exam PT0-002, veteran information security experts Dr. Mike Chapple and David Seidl deliver a comprehensive roadmap to the foundational and advanced skills every pentester (penetration tester) needs to secure their CompTIA PenTest+ certification, ace their next interview, and succeed in an exciting new career in a growing field.
You'll learn to perform security assessments of traditional servers, desktop and mobile operating systems, cloud installations, Internet-of-Things devices, and industrial or embedded systems. You'll plan and scope a penetration testing engagement including vulnerability scanning, understand legal and regulatory compliance requirements, analyze test results, and produce a written report with remediation techniques.
This book will:
- Prepare you for success on the newly introduced CompTIA PenTest+ PT0-002 Exam
- Multiply your career opportunities with a certification that complies with ISO 17024 standards and meets Department of Defense Directive 8140/8570.01-M requirements
- Allow access to the Sybex online learning center, with chapter review questions, full-length practice exams, hundreds of electronic flashcards, and a glossary of key terms
Perfect for anyone preparing for the updated CompTIA PenTest+ certification exam, CompTIA PenTest+ Study Guide: Exam PT0-002 is also a must-read resource for aspiring penetration testers and IT security professionals seeking to expand and improve their skillset.
Tools to learn more effectively

Saving Books

Keyword Search

Annotating Text

Listen to it instead
Information
Chapter 1
Penetration Testing
- 1.3 Given a scenario, demonstrate an ethical hacking mindset by maintaining professionalism and integrity.
- Background checks of penetration testing team
- Adhere to specific scope of engagement
- Identify criminal activity
- Immediately report breaches/criminal activity
- Limit the use of tools to a particular engagement
- Limit invasiveness based on scope
- Maintain confidentiality of data/information
- Risks to the professional
What Is Penetration Testing?
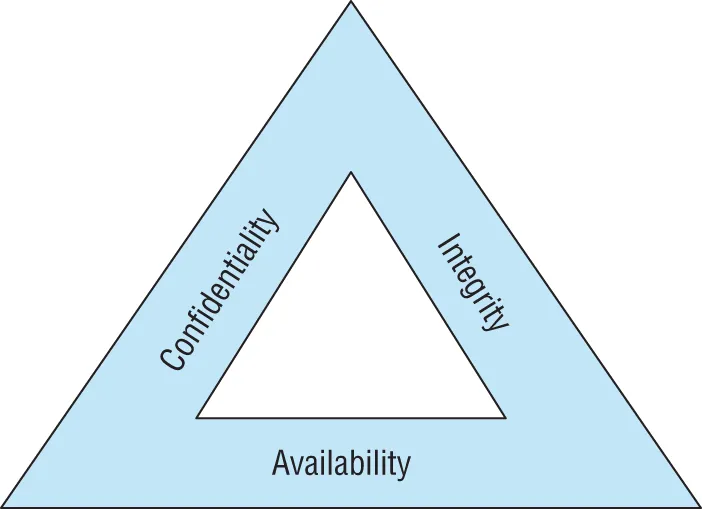
Cybersecurity Goals
- Confidentiality measures seek to prevent unauthorized access to information or systems.
- Integrity measures seek to prevent unauthorized modification of information or systems.
- Availability measures seek to ensure that legitimate use of information and systems remains possible.
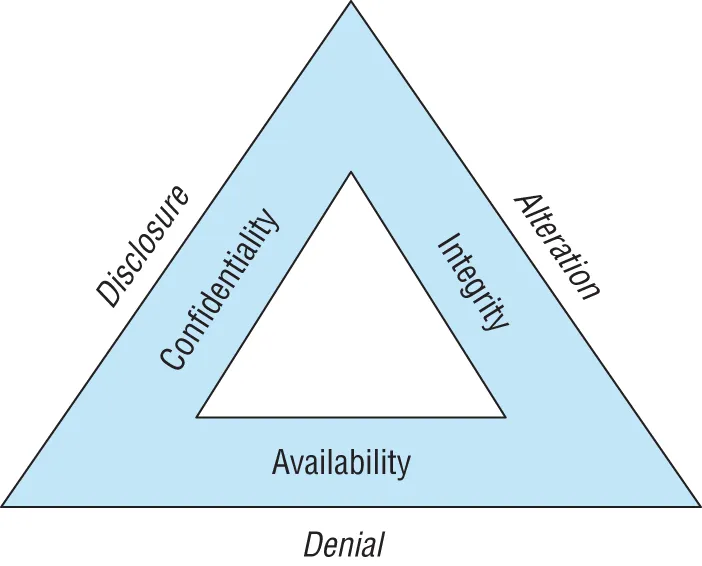
- Disclosure attacks seek to gain unauthorized access to information or systems.
- Alteration attacks seek to make unauthorized changes to information or systems.
- Denial attacks seek to prevent legitimate use of information and systems.
Adopting the Hacker Mindset
- Security cameras in high‐risk areas
- Auditing of cash register receipts
- Theft detectors at the main entrance/exit of the store
- Exit alarms on emergency exits
- Burglar al...
Table of contents
- Cover
- Table of Contents
- Title Page
- Copyright
- Dedication
- Acknowledgments
- About the Author
- About the Technical Editor
- Introduction
- Chapter 1: Penetration Testing
- Chapter 2: Planning and Scoping Penetration Tests
- Chapter 3: Information Gathering
- Chapter 4: Vulnerability Scanning
- Chapter 5: Analyzing Vulnerability Scans
- Chapter 6: Exploiting and Pivoting
- Chapter 7: Exploiting Network Vulnerabilities
- Chapter 8: Exploiting Physical and Social Vulnerabilities
- Chapter 9: Exploiting Application Vulnerabilities
- Chapter 10: Attacking Hosts, Cloud Technologies, and Specialized Systems
- Chapter 11: Reporting and Communication
- Chapter 12: Scripting for Penetration Testing
- Appendix A: Answers to Review Questions
- Appendix B: Solution to Lab Exercise
- Index
- End User License Agreement
Frequently asked questions
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app