
- 416 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
About this book
This book is the first of its kind to introduce the integration of ethics, laws, risks, and policies in cyberspace. The book provides understanding of the ethical and legal aspects of cyberspace along with the risks involved. It also addresses current and proposed cyber policies, serving as a summary of the state of the art cyber laws in the United States. It also, importantly, incorporates various risk management and security strategies from a number of organizations.
Using easy-to-understand language and incorporating case studies, the authors begin with the consideration of ethics and law in cybersecurity and then go on to take into account risks and security policies. The section on risk covers identification, analysis, assessment, management, and remediation. The very important topic of cyber insurance is covered as well—its benefits, types, coverage, etc. The section on cybersecurity policy acquaints readers with the role of policies in cybersecurity and how they are being implemented by means of frameworks. The authors provide a policy overview followed by discussions of several popular cybersecurity frameworks, such as NIST, COBIT, PCI/DSS, ISO series, etc.
Frequently asked questions
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app.
Information
PART I Cybersecurity: Ethics and Legal
CHAPTER 1 Introduction to Cyberethics
1.1 ETHICS IN CYBERSPACE AND CYBERSECURITY
1.1.1 DEFINITION 1.1: CYBERSPACE
1.1.2 DEFINITION 1.2: CYBERSECURITY
- Confidentiality: It refers to protecting the information from disclosure to unauthorized parties. It is associated with the protection of details which should be visible or accessible to people who have appropriate privileges.
- Integrity: It is responsible for ensuring trustworthiness, accuracy, and completeness of the sensitive information. The main objective of integrity is to protect information from being altered by unauthorized or unintended parties and individuals.
- Availability: It is responsible for ensuring that only authorized parties can access the information when at the time of need.
- Authentication: It refers to the process of ensuring and confirming the identity of a user.
- Non‑Repudiation: It can be used to ensure that a party involved in a communication cannot deny the authenticity of their signature on a document or the sending of a message that they originated.

- First, lack of proper cybersecurity ethics training may make the employee unaware of any breach of ethics in cyberspace. An employee may not realize if he/she has been victimized on the grounds of ethics.
- Second, the employee themselves may at some point of time do something that is ethically wrong.
- Third, due to the lack of cyberethics training, an employee may not know what is to be done in this situation, further deteriorating the situation.
- Second, the employee themselves may at some point of time do something that is ethically wrong.
1.1.3 DEFINITION 1.3: CYBERETHICS
- Cyberethics underpins the study of ethics pertaining to computers and networks;
- Cyberethics also takes into account user behavior as well as what computers are programmed to do;
- Cyberethics has its effects on individuals and society;
- Cyberethics focuses on responsible behaviors on the internet;
- Cyberethics deal with ethics applied to the Online Environment.
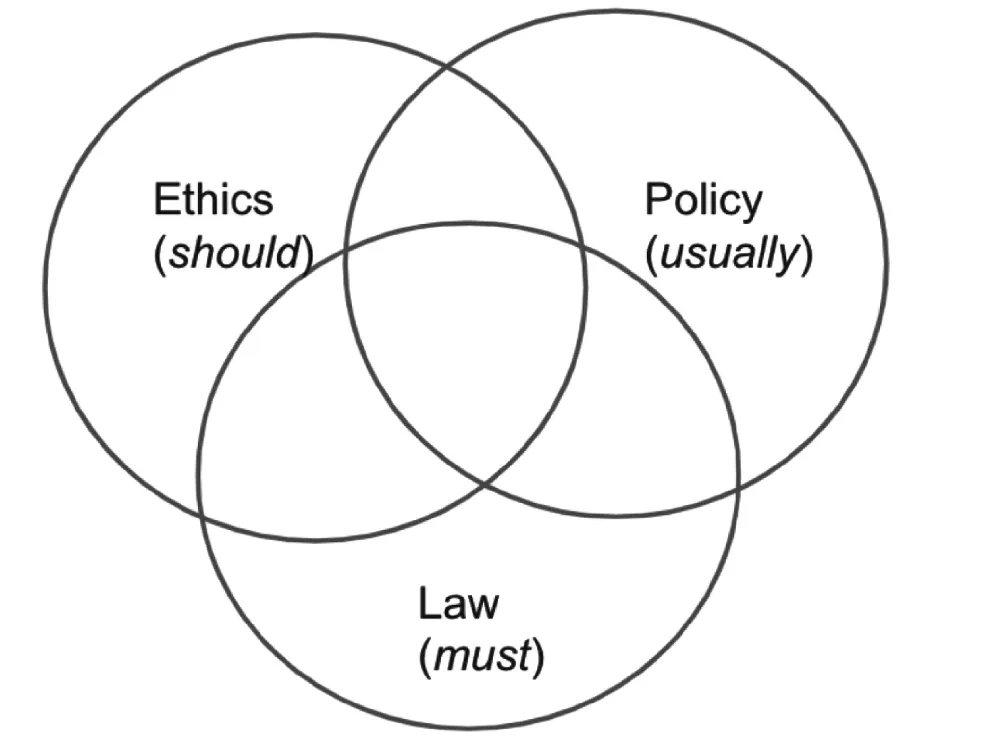
1.2 ETHICS, LAW, AND POLICY
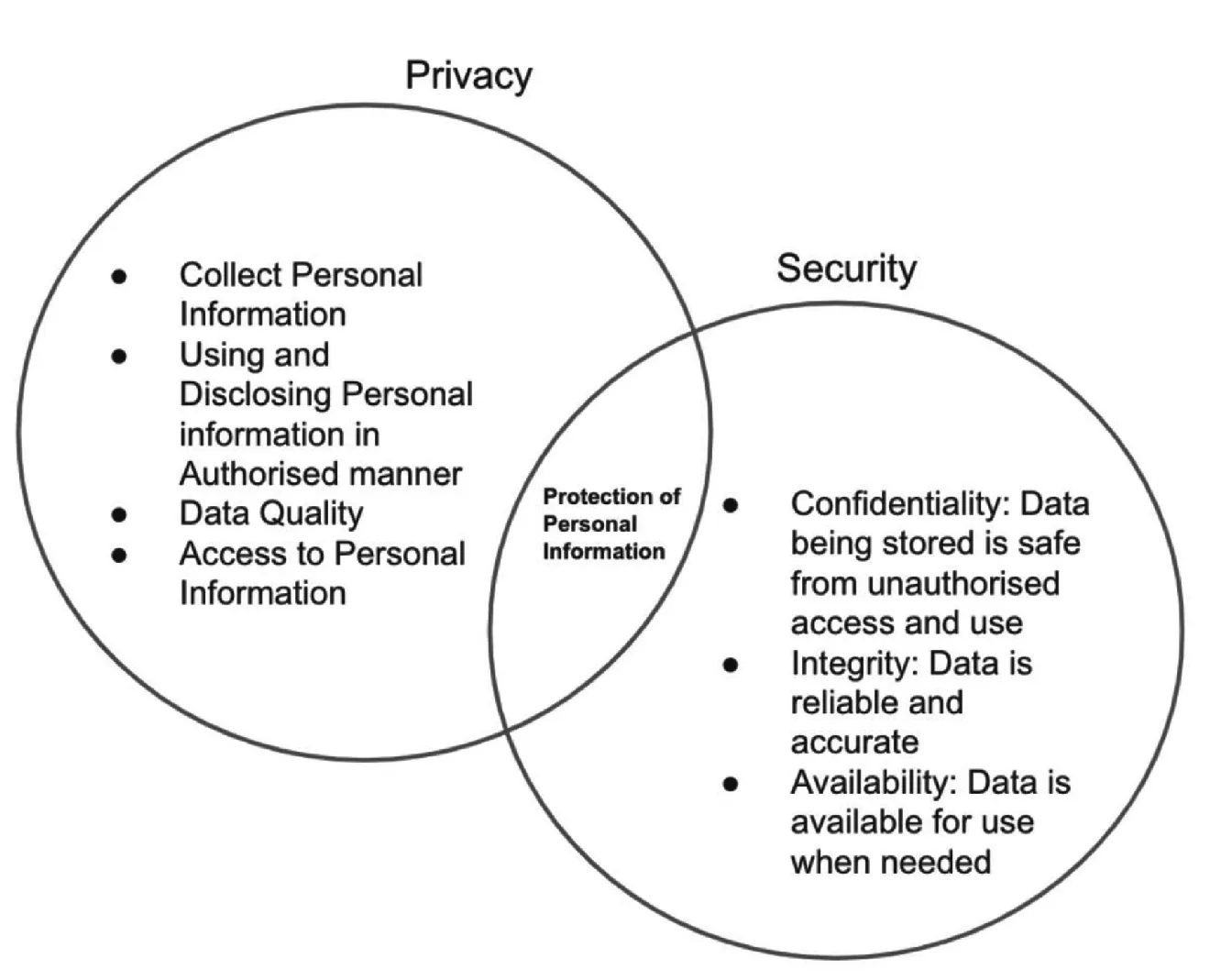
1.3 PRIVACY AND SECURITY
- First, both privacy and security are maintained. Your personal information stays with you;
- Second, privacy may be compromised, but security is still maintained (Figure 1.3). Your personal information may not be only with you; and
- Third, both privacy and security are compromised.
1.3.1 DEFINITION 1.4: SECURITY

1.3.2 DEFINITION 1.5: PRIVACY
1.4 THE NEED FOR CYBERETHICS
- Social media constitutes a significant part of cyberspace, and the number of users in social media is very high. These are the platforms where people can express their opinions anonymously in the free society. However, these platforms also witness anonymous postings to blogs, websites, and social media that can encourage bad behavior anytime. Bullying, harassment, stalking, gender inequality, human rig...
Table of contents
- Cover Page
- Half-Title Page
- Title Page
- Copyright Page
- About the Authors
- Table of Contents
- Abbreviations
- Preface
- Introduction
- Part I: Cybersecurity: Ethics and Legal
- Part II: Cybersecurity: Risks and Policies
- Bibliography
- Index