
Enterprise Cybersecurity in Digital Business
Building a Cyber Resilient Organization
- 530 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
About this book
Cyber risk is the highest perceived business risk according to risk managers and corporate insurance experts. Cybersecurity typically is viewed as the boogeyman: it strikes fear into the hearts of non-technical employees. Enterprise Cybersecurity in Digital Business: Building a Cyber Resilient Organization provides a clear guide for companies to understand cyber from a business perspective rather than a technical perspective, and to build resilience for their business.
Written by a world-renowned expert in the field, the book is based on three years of research with the Fortune 1000 and cyber insurance industry carriers, reinsurers, and brokers. It acts as a roadmap to understand cybersecurity maturity, set goals to increase resiliency, create new roles to fill business gaps related to cybersecurity, and make cyber inclusive for everyone in the business. It is unique since it provides strategies and learnings that have shown to lower risk and demystify cyber for each person. With a clear structure covering the key areas of the Evolution of Cybersecurity, Cybersecurity Basics, Cybersecurity Tools, Cybersecurity Regulation, Cybersecurity Incident Response, Forensics and Audit, GDPR, Cybersecurity Insurance, Cybersecurity Risk Management, Cybersecurity Risk Management Strategy, and Vendor Risk Management Strategy, the book provides a guide for professionals as well as a key text for students studying this field.
The book is essential reading for CEOs, Chief Information Security Officers, Data Protection Officers, Compliance Managers, and other cyber stakeholders, who are looking to get up to speed with the issues surrounding cybersecurity and how they can respond. It is also a strong textbook for postgraduate and executive education students in cybersecurity as it relates to business.
Frequently asked questions
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app.
Information
Part IThe Evolution of Cyber Risk
1CyberA business issue
I know not with what weapons World War III will be fought, but World War IV will be fought with sticks and stones.Albert Einstein
The internet—welcome to my nightmare
Cyber gets real for businesses
Regulators put their money where their mouth is
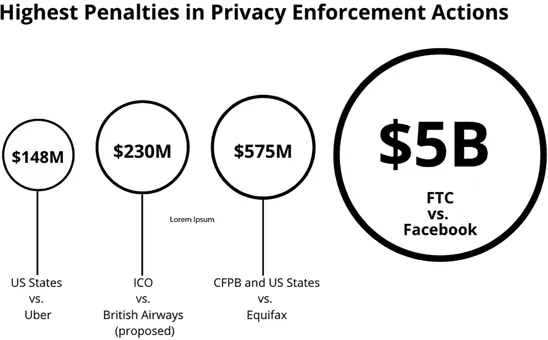
- Document the program. Document the “content, implementation, and maintenance of the Privacy Program” and provide that description to the Principal Executive Officer (Mark Zuckerberg) and an Independent Privacy Committee that reports to the board at least once a year.
- Hire an independent privacy chief. Designate an employee as a “Chief Privacy Officer for Product” (
CPO) to run the program. The CPO's hiring and removal must be approved by the Independent Privacy Committee. - Conduct risk assessments. Assess and document, at least annually, both internal and external risks in each area of operations, including, within 30 days, risks relating to a Covered Incident. A Covered Incident is a verified incident where data from 500 or more users was accessed, collected, used, or shared by a third party in violation of Facebook's terms.
- Implement safeguards which include the following:
- Annual third-party certifications, monitoring, and enforcement against third parties that violate contract terms.
- Privacy review of new products, services, or practices, with documentation and a detailed written report about any privacy risks and safeguards, and a quarterly report from the CPO to the Principal Executive Officer (Mark Zuckerberg) of these reviews and all privacy decisions, in advance of meetings of the Independent Privacy Commission.
- Controls that limit employee access to information and that protect information shared with affiliates.
- Disclosure and consent for facial recognition.
- Test safeguards. Safeguards must be tested, assessed, and monitored annually and within 30 days after a cyber incident.
- Implement training. Establish regular privacy training programs.
- Ensure the performance of service providers. Retain providers capable of safeguarding information and contractually require them to safeguard it.
- Use outside experts. Seek guidance from independent third parties on implementing, maintaining, and updating the program.
- Evaluate the program. Evaluate the program at least annually, taking into account cyber incidents.
Digitization—the explosion in cybercrime
Table of contents
- Cover Page
- Half-Title Page
- Title Page
- Copyright Page
- Contents
- List of figures
- List of images
- Notices
- Abstract
- About the author
- Acknowledgment
- Preface
- Introduction
- Overview
- PART I The evolution of cyber risk
- PART II Cyber basics
- PART III Cybersecurity tools
- PART IV Cybersecurity regulation and frameworks
- PART V Incident response, audit, and forensics
- PART VI Cybersecurity risk management
- PART VII The general data protection regulation (GDPR) and privacy
- PART VIII Cybersecurity risk strategy
- PART IX Cybersecurity insurance
- PART X Cyber vendor risk management
- The way forward
- Abbreviations
- Glossary
- Index