
Cryptography Algorithms
A guide to algorithms in blockchain, quantum cryptography, zero-knowledge protocols, and homomorphic encryption
- 358 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
Cryptography Algorithms
A guide to algorithms in blockchain, quantum cryptography, zero-knowledge protocols, and homomorphic encryption
About this book
Build your real-world cryptography knowledge, from understanding the fundamentals to implementing the most popular modern-day algorithms to excel in your cybersecurity careerKey Features• Learn modern algorithms such as zero-knowledge, elliptic curves, and quantum cryptography• Explore vulnerability and new logical attacks on the most-used algorithms• Understand the practical implementation of algorithms and protocols in cybersecurity applicationsBook DescriptionCryptography Algorithms is designed to help you get up and running with modern cryptography algorithms. You'll not only explore old and modern security practices but also discover practical examples of implementing them effectively.The book starts with an overview of cryptography, exploring key concepts including popular classical symmetric and asymmetric algorithms, protocol standards, and more. You'll also cover everything from building crypto codes to breaking them. In addition to this, the book will help you to understand the difference between various types of digital signatures. As you advance, you will become well-versed with the new-age cryptography algorithms and protocols such as public and private key cryptography, zero-knowledge protocols, elliptic curves, quantum cryptography, and homomorphic encryption. Finally, you'll be able to apply the knowledge you've gained with the help of practical examples and use cases.By the end of this cryptography book, you will be well-versed with modern cryptography and be able to effectively apply it to security applications.What you will learn• Understand key cryptography concepts, algorithms, protocols, and standards• Break some of the most popular cryptographic algorithms• Build and implement algorithms efficiently• Gain insights into new methods of attack on RSA and asymmetric encryption• Explore new schemes and protocols for blockchain and cryptocurrency• Discover pioneering quantum cryptography algorithms• Perform attacks on zero-knowledge protocol and elliptic curves• Explore new algorithms invented by the author in the field of asymmetric, zero-knowledge, and cryptocurrencyWho this book is forThis hands-on cryptography book is for IT professionals, cybersecurity enthusiasts, or anyone who wants to develop their skills in modern cryptography and build a successful cybersecurity career. Working knowledge of beginner-level algebra and finite fields theory is required.
Tools to learn more effectively

Saving Books

Keyword Search

Annotating Text

Listen to it instead
Information
Section 1: A Brief History and Outline of Cryptography
- Chapter 1, Deep Diving into Cryptography
Chapter 1: Deep Diving into Cryptography
- A brief introduction to cryptography
- Basic definitions and principal mathematical notations used in the book
- Binary conversion and ASCII code
- Fermat Last's Theorem, prime numbers, and modular mathematics
- The history of the principal cryptographic algorithms and an explanation of some of them (Rosetta cipher, Caesar, ROT13, Beale, Vernam)
- Security notation (semantic, provable, OTP, and so on)
An introduction to cryptography
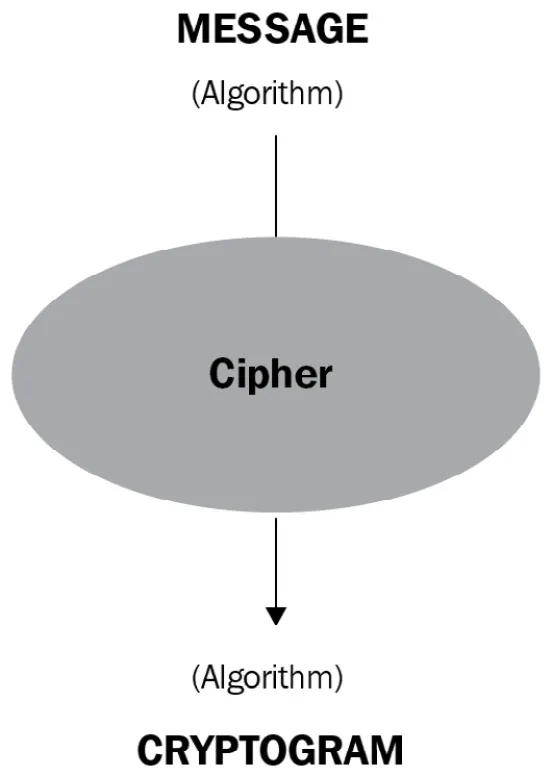
- In cryptography, a private or secret key (Kpr), denoted as [K] or [k], is an encryption/decryption parameter known only to one, both, or multiple parties in order to exchange secret messages.
- In cryptography, a public key (Kpu) or (K) is an encryption key known by everyone who wants to send a secret message or authenticate a user.
- Symmetric encryption uses only one shared key to both encrypt and decrypt the message.
- Asymmetric encryption implements more parameters to generate a public key (to encrypt the message) and just one private key to decrypt the message.
Table of contents
- Cryptography Algorithms
- Contributors
- Preface
- Section 1: A Brief History and Outline of Cryptography
- Chapter 1: Deep Diving into Cryptography
- Section 2: Classical Cryptography (Symmetric and Asymmetric Encryption)
- Chapter 2: Introduction to Symmetric Encryption
- Chapter 3: Asymmetric Encryption
- Chapter 4: Introducing Hash Functions and Digital Signatures
- Section 3: New Cryptography Algorithms and Protocols
- Chapter 5: Introduction to Zero-Knowledge Protocols
- Chapter 6: New Algorithms in Public/Private Key Cryptography
- Chapter 7: Elliptic Curves
- Chapter 8: Quantum Cryptography
- Section 4: Homomorphic Encryption and the Crypto Search Engine
- Chapter 9: Crypto Search Engine
- Other Books You May Enjoy
Frequently asked questions
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app