
- 480 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
Istio in Action
About this book
Solve difficult service-to-service communication challenges around security, observability, routing, and resilience with an Istio-based service mesh. Istio allows you to define these traffic policies as configuration and enforce them consistently without needing any service-code changes. In Istio in Action you will learn: Why and when to use a service mesh
Envoy's role in Istio's service mesh
Allowing "North-South" traffic into a mesh
Fine-grained traffic routing
Make your services robust to network failures
Gain observability over your system with telemetry "golden signals"
How Istio makes your services secure by default
Integrate cloud-native applications with legacy workloads such as in VMs Reduce the operational complexity of your microservices with an Istio-powered service mesh! Istio in Action shows you how to implement this powerful new architecture and move your application-networking concerns to a dedicated infrastructure layer. Non-functional concerns stay separate from your application, so your code is easier to understand, maintain, and adapt regardless of programming language. In this practical guide, you'll go hands-on with the full-featured Istio service mesh to manage microservices communication. Helpful diagrams, example configuration, and examples make it easy to understand how to control routing, secure container applications, and monitor network traffic. Foreword by Eric Brewer. About the technology
Offload complex microservice communication layer challenges to Istio! The industry-standard Istio service mesh radically simplifies security, routing, observability, and other service-to-service communication challenges. With Istio, you use a straightforward declarative configuration style to establish application-level network policies. By separating communication from business logic, your services are easier to write, maintain, and modify. About the book
Istio in Action teaches you how to implement an Istio-based service mesh that can handle complex routing scenarios, traffic encryption, authorization, and other common network-related tasks. You'll start by defining a basic service mesh and exploring the data plane with Istio's service proxy, Envoy. Then, you'll dive into core topics like traffic routing and visualization and service-to-service authentication, as you expand your service mesh to workloads on multiple clusters and legacy VMs. What's inside Comprehensive coverage of Istio resources
Practical examples to showcase service mesh capabilities
Implementation of multi-cluster service meshes
How to extend Istio with WebAssembly
Traffic routing and observability
VM integration into the mesh About the reader
For developers, architects, and operations engineers. About the author
Christian Posta is a well-known architect, speaker, and contributor. Rinor Maloku is an engineer at Solo.io working on application networking solutions. ToC
PART 1 UNDERSTANDING ISTIO
1 Introducing the Istio service mesh
2 First steps with Istio
3 Istio's data plane: The Envoy proxy
PART 2 SECURING, OBSERVING, AND CONTROLLING YOUR SERVICE'S NETWORK TRAFFIC
4 Istio gateways: Getting traffic into a cluster
5 Traffic control: Fine-grained traffic routing
6 Resilience: Solving application networking challenges
7 Observability: Understanding the behavior of your services
8 Observability: Visualizing network behavior with Grafana, Jaeger, and Kiali
9 Securing microservice communication
PART 3 ISTIO DAY-2 OPERATIONS
10 Troubleshooting the data plane
11 Performance-tuning the control plane
PART 4 ISTIO IN YOUR ORGANIZATION
12 Scaling Istio in your organization
13 Incorporating virtual machine workloads into the mesh
14 Extending Istio on the request path
Tools to learn more effectively

Saving Books

Keyword Search

Annotating Text

Listen to it instead
Information
Part 1 Understanding Istio
1 Introducing the Istio service mesh
- Addressing the challenges of service-oriented architectures with service meshes
- Introducing Istio and how it helps solve microservice issues
- Comparing service meshes to earlier technologies
1.1 Challenges of going faster
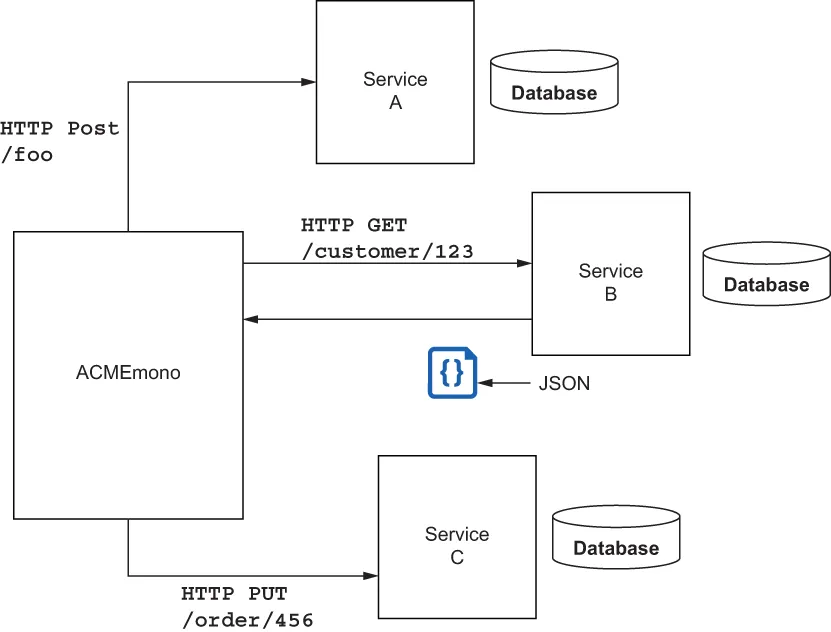
Table of contents
- Istio in Action
- Copyright
- dedication
- contents
- front matter
- Part 1 Understanding Istio
- 1 Introducing the Istio service mesh
- 2 First steps with Istio
- 3 Istio’s data plane: The Envoy proxy
- Part 2 Securing, observing, and controlling your service’s network traffic
- 4 Istio gateways: Getting traffic into a cluster
- 5 Traffic control: Fine-grained traffic routing
- 6 Resilience: Solving application networking challenges
- 7 Observability: Understanding the behavior of your services
- 8 Observability: Visualizing network behavior with Grafana, Jaeger, and Kiali
- 9 Securing microservice communication
- Part 3 Istio day-2 operations
- 10 Troubleshooting the data plane
- 11 Performance-tuning the control plane
- Part 4 Istio in your organization
- 12 Scaling Istio in your organization
- 13 Incorporating virtual machine workloads into the mesh
- 14 Extending Istio on the request path
- appendix A. Customizing the Istio installation
- appendix B. Istio’s sidecar and its injection options
- appendix C. Istio security: SPIFFE
- appendix D. Troubleshooting Istio components
- appendix E. How the virtual machine is configured to join the mesh
- index
Frequently asked questions
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app