
Security and Privacy Trends in Cloud Computing and Big Data
- 216 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
Security and Privacy Trends in Cloud Computing and Big Data
About this book
It is essential for an organization to know before involving themselves in cloud computing and big data, what are the key security requirements for applications and data processing. Big data and cloud computing are integrated together in practice. Cloud computing offers massive storage, high computation power, and distributed capability to support processing of big data. In such an integrated environment the security and privacy concerns involved in both technologies become combined.
This book discusses these security and privacy issues in detail and provides necessary insights into cloud computing and big data integration. It will be useful in enhancing the body of knowledge concerning innovative technologies offered by the research community in the area of cloud computing and big data. Readers can get a better understanding of the basics of cloud computing, big data, and security mitigation techniques to deal with current challenges as well as future research opportunities.
Tools to learn more effectively

Saving Books

Keyword Search

Annotating Text

Listen to it instead
Information
Chapter 1 Information security framework for cloud and virtualization security
CONTENTS
- 1.1 Introduction
- 1.2 Virtualization
- 1.2.1 Type-I hypervisor
- 1.2.2 Type-II hypervisor
- 1.2.3 Virtualization benefits
- 1.2.3.1 Low cost/save energy
- 1.2.3.2 Small footprints
- 1.2.3.3 Fast lab provisioning
- 1.2.3.4 Abstraction
- 1.2.3.5 Disaster recovery
- 1.2.3.6 Application isolation
- 1.2.3.7 Easy migration to cloud
- 1.2.3.8 Better testing
- 1.3 Cloud and security issues in virtualization
- 1.3.1 Virtualization issues
- 1.3.1.1 Virtualization based malware
- 1.3.1.2 Mobility
- 1.3.1.3 Denial of service attack
- 1.3.1.4 Communication attack among guest VMs and hosts
- 1.3.1.5 Virtual machine escape
- 1.3.1.6 Inter-VM attacks and network blind spots
- 1.3.1 Virtualization issues
- 1.4 Information security framework for cloud computing
- 1.4.1 User network
- 1.4.2 Security layer
- 1.4.3 Private cloud
- 1.4.3.1 User interface layer
- 1.4.3.2 Platform layer
- 1.4.3.3 Software layer
- 1.4.3.4 Management layer
- 1.4.4 Public cloud
- 1.5 Conclusion
- References
1.1 Introduction
1.2 Virtualization
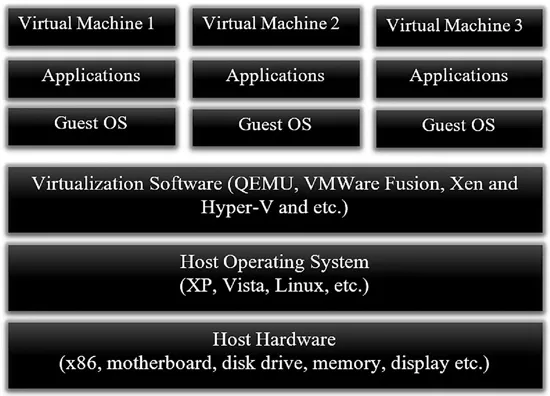
1.2.1 Type-I hypervisor
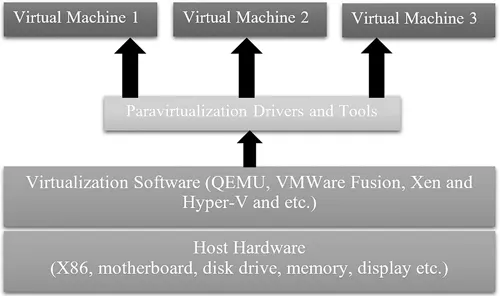
1.2.2 Type-II hypervisor
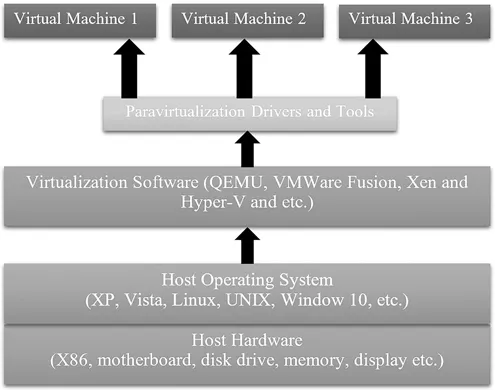
1.2.3 Virtualization benefits
1.2.3.1 Low cost/save energy
1.2.3.2 Small footprints
1.2.3.3 Fast lab provisioning
1.2.3.4 Abstraction
1.2.3.5 Disaster recovery
Table of contents
- Cover
- Half Title
- Title Page
- Copyright Page
- Table of Contents
- Preface
- Editors
- Contributors
- 1 Information security framework for cloud and virtualization security
- 2 Security, integrity, and privacy of cloud computing and big data
- 3 The ways of networks intrusion their detection and prevention
- 4 Cloud-based face recognition for low resource clients
- 5 Data mining security for big data
- 6 Cloud computing security challenges and their solutions
- 7 Security algorithms for secure cloud environment
- 8 Cloud computing security challenges, analysis of security problems and cloud computing forensics issues
- 9 Impact of big data in healthcare and management analysis
- 10 Privacy and security issues of big data
- Index
Frequently asked questions
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app