
- English
- ePUB (mobile friendly)
- Available on iOS & Android
CISM Certified Information Security Manager Study Guide
About this book
Sharpen your information security skills and grab an invaluable new credential with this unbeatable study guide
As cybersecurity becomes an increasingly mission-critical issue, more and more employers and professionals are turning to ISACA's trusted and recognized Certified Information Security Manager qualification as a tried-and-true indicator of information security management expertise.
In Wiley's Certified Information Security Manager (CISM) Study Guide, you'll get the information you need to succeed on the demanding CISM exam. You'll also develop the IT security skills and confidence you need to prove yourself where it really counts: on the job.
Chapters are organized intuitively and by exam objective so you can easily keep track of what you've covered and what you still need to study. You'll also get access to a pre-assessment, so you can find out where you stand before you take your studies further.
Sharpen your skills with Exam Essentials and chapter review questions with detailed explanations in all four of the CISM exam domains: Information Security Governance, Information Security Risk Management, Information Security Program, and Incident Management.
In this essential resource, you'll also:
- Grab a head start to an in-demand certification used across the information security industry
- Expand your career opportunities to include rewarding and challenging new roles only accessible to those with a CISM credential
- Access the Sybex online learning center, with chapter review questions, full-length practice exams, hundreds of electronic flashcards, and a glossary of key terms
Perfect for anyone prepping for the challenging CISM exam or looking for a new role in the information security field, the Certified Information Security Manager (CISM) Study Guide is an indispensable resource that will put you on the fast track to success on the test and in your next job.
Tools to learn more effectively

Saving Books

Keyword Search

Annotating Text

Listen to it instead
Information
Chapter 1
Today's Information Security Manager
- Domain 1: Information Security Governance
- A. Enterprise Governance
- 1A1. Organizational Culture
- 1A3. Organizational Structures, Roles and Responsibilities
- B. Information Security Strategy
- 1B1. Information Security Strategy Development
- A. Enterprise Governance
- 1. Identify internal and external influences to the organization that impact the information security strategy.
- 2. Establish and/or maintain an information security strategy in alignment with organizational goals and objectives.
- 7. Gain ongoing commitment from senior leadership and other stakeholders to support the successful implementation of the information security strategy.
- 8. Define, communicate, and monitor information security responsibilities throughout the organization and lines of authority.
Information Security Objectives
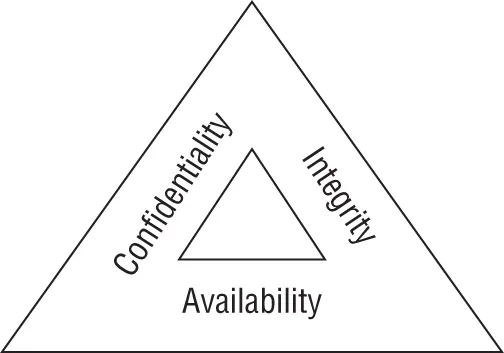
Role of the Information Security Manager

Chief Information Security Officer
- Vice president...
Table of contents
- Cover
- Table of Contents
- Title Page
- Copyright
- Dedication
- Acknowledgments
- About the Author
- About the Technical Editor
- Introduction
- Chapter 1: Today's Information Security Manager
- Chapter 2: Information Security Governance and Compliance
- Chapter 3: Information Risk Management
- Chapter 4: Cybersecurity Threats
- Chapter 5: Information Security Program Development and Management
- Chapter 6: Security Assessment and Testing
- Chapter 7: Cybersecurity Technology
- Chapter 8: Incident Response
- Chapter 9: Business Continuity and Disaster Recovery
- Appendix: Answers to the Review Questions
- Index
- End User License Agreement
Frequently asked questions
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app