
- 314 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
Windows 10 for Enterprise Administrators
About this book
Learn the art of configuring, deploying, managing and securing Windows 10 for your enterprise.About This Book• Enhance your enterprise administration skills to manage Windows 10 Redstone 3• Get acquainted with configuring Azure Active Directory for enabling cloud-based services and Remote Server Admin Tools for managing Windows Server• Provide enterprise-level security with ease using the built-in data loss prevention of Windows 10Who This Book Is ForIf you are a system administrator who has been given the responsibility of administering and managing Windows 10 Redstone 3, then this book is for you. If you have deployed and managed previous versions of Windows, it would be an added advantage.What You Will Learn• Understand the remote access capabilities• Use third-party tools to deploy Windows 10• Customize image and user Interface experience• Implement assigned access rights• Configure remote administration• Manage Windows 10 security• Work with Azure AD and Intune managementIn DetailMicrosoft's launch of Windows 10 is a step toward satisfying the enterprise administrator's needs for management and user experience customization. This book provides the enterprise administrator with the knowledge needed to fully utilize the advanced feature set of Windows 10 Enterprise.This practical guide shows Windows 10 from an administrator's point of view. You'll focus on areas such as installation and configuration techniques based on your enterprise requirements, various deployment scenarios and management strategies, and setting up and managing admin and other user accounts. You'll see how to configure Remote Server Administration Tools to remotely manage Windows Server and Azure Active Directory.Lastly, you will learn modern Mobile Device Management for effective BYOD and how to enable enhanced data protection, system hardening, and enterprise-level security with the new Windows 10 in order to prevent data breaches and impede attacks.By the end of this book, you will know the key technologies and capabilities in Windows 10 and will confidently be able to manage and deploy these features in your organization.Style and approachThis step-by-step guide will show you how to configure, deploy, manage, and secure the all new Windows 10 Redstone 3 for your enterprise.
Tools to learn more effectively

Saving Books

Keyword Search

Annotating Text

Listen to it instead
Information
Windows 10 Security
- Windows Hello and Windows Hello for Business
- Virtual-based security
- Credential Guard
- Device Guard
- Windows Defender Application Guard (WDAG) for Microsoft Edge
- Windows Defender Exploit Guard
- Device Health Attestation
- New BitLocker options
- Local Administrator Password Solution
Today's security challenges
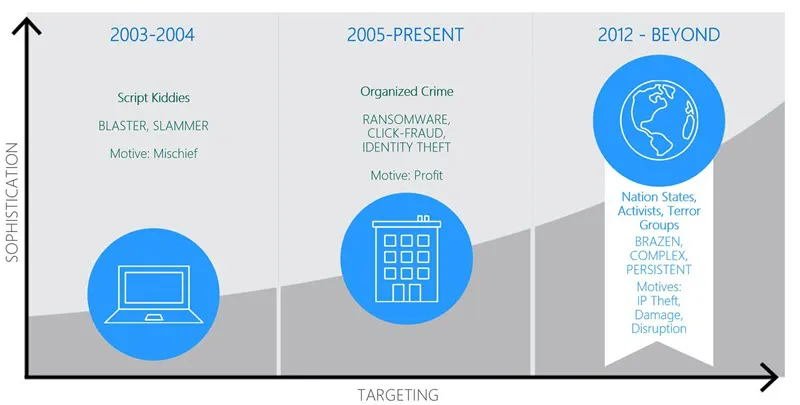
- Device protection
- Threat resistance
- Identity protection
- Information protection

Windows Hello/Windows Hello for Business
Table of contents
- Title Page
- Copyright
- Credits
- About the Authors
- About the Reviewer
- www.PacktPub.com
- Customer Feedback
- Preface
- Installation and Upgrading
- Configuration and Customization
- User Account Administration
- Remote Administration Tools
- Device Management
- Protecting Enterprise Data in BYOD Scenarios
- Windows 10 Security
- Windows Defender Advanced Threat Protection
- Advanced Configurations
- RedStone 3 Changes
Frequently asked questions
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app