
Building Effective Cybersecurity Programs
A Security Manager's Handbook
- 249 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
Building Effective Cybersecurity Programs
A Security Manager's Handbook
About this book
You know by now that your company could not survive without the Internet. Not in today's market. You are either part of the digital economy or reliant upon it. With critical information assets at risk, your company requires a state-of-the-art cybersecurity program. But how do you achieve the best possible program? Tari Schreider, in Building Effective Cybersecurity Programs: A Security Manager's Handbook, lays out the step-by-step roadmap to follow as you build or enhance your cybersecurity program.
Over 30+ years, Tari Schreider has designed and implemented cybersecurity programs throughout the world, helping hundreds of companies like yours. Building on that experience, he has created a clear roadmap that will allow the process to go more smoothly for you. Building Effective Cybersecurity Programs: A Security Manager's Handbook is organized around the six main steps on the roadmap that will put your cybersecurity program in place:
- Design a Cybersecurity Program
- Establish a Foundation of Governance
- Build a Threat, Vulnerability Detection, and Intelligence Capability
- Build a Cyber Risk Management Capability
- Implement a Defense-in-Depth Strategy
- Apply Service Management to Cybersecurity Programs
Because Schreider has researched and analyzed over 150 cybersecurity architectures, frameworks, and models, he has saved you hundreds of hours of research. He sets you up for success by talking to you directly as a friend and colleague, using practical examples. His book helps you to:
- Identify the proper cybersecurity program roles and responsibilities.
- Classify assets and identify vulnerabilities.
- Define an effective cybersecurity governance foundation.
- Evaluate the top governance frameworks and models.
- Automate your governance program to make it more effective.
- Integrate security into your application development process.
- Apply defense-in-depth as a multi-dimensional strategy.
- Implement a service management approach to implementing countermeasures.
With this handbook, you can move forward confidently, trusting that Schreider is recommending the best components of a cybersecurity program for you. In addition, the book provides hundreds of citations and references allow you to dig deeper as you explore specific topics relevant to your organization or your studies.
Tools to learn more effectively

Saving Books

Keyword Search

Annotating Text

Listen to it instead
Information

Chapter 1
Designing a Cybersecurity Program
- Learn that investing the time and effort to properly design your cybersecurity program is tantamount to its success.
- Create a properly structured cybersecurity program.
- Leverage good practices to improve your cybersecurity program design.
1.1 Cybersecurity Program Design Methodology
1.1.1 Need for a Design to Attract the Best Personnel
1.1.2 A Recommended Design Approach: ADDIOI Model™
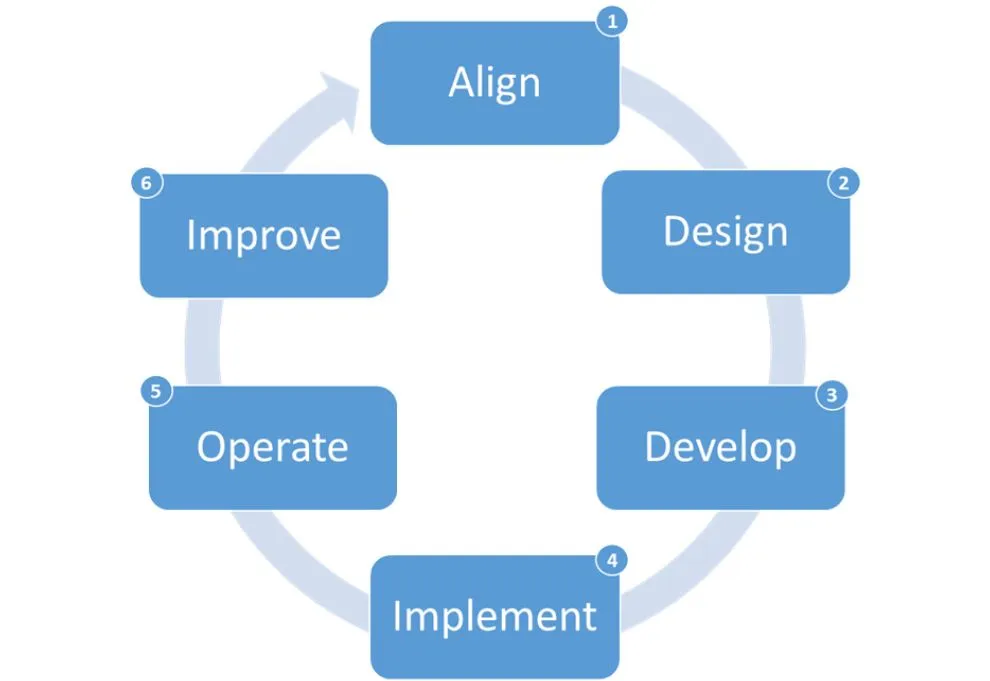
1.1.3 The Six Phases of the ADDIOI Model™
- Align - This phase is where you identify your organization’s business goals and align them to the capabilities of the cybersecurity program. Always remember the business is your benefactor paying for all your cybersecurity gizmos, so alignment is crucial. You must show the value of your program by demonstrating how it reduces operational risk. A key outcome will be program design requirements. The align phase is an ongoing process and supports the improve phase.
- Design - This phase is what this chapter predominately addresses - designing the structure of your cybersecurity program. Here you create your program blueprint to show stakeholders the vision of the final product and validate alignment to the business in a concrete manner. For example, if one of your business goals is to maintain regulatory compliance, compliance capability should be reflected in your design.
- Develop - This phase is where you configure and test the cybersecurity countermeasures called out within the design requirements. Development may also include creating or modifying application code to support cybersecurity countermeasures. For example, integrating an access authentication or single sign-on solution will require application integration. Countermeasure testing provides the basis to create experience-based implementation plans and acceptance criteria to move countermeasures from test to production. Information technology (IT) infrastructure is locked down (hardened) in this phase, making it resilient to cyberattack. Develop and customize are the primary activities of this phase.
- Implement - This phase is the execution of implementation plans to “go live” with your cybersecurity countermeasures developed in the previous phase. You should strive to create a culture of security with your training program, instilling the human firewall philosophy, your first line and many times your last line of defense. This is the phase where you will organize cybersecurity program staff around the program’s components. Onboarding security service providers occurs within this phase. Deployment and training are the primary activities of the implement phase.
- Operate - This phase is where the day-to-day management and operations of the cybersecurity countermeasures occur. Most commonly referred to as security operations (SecOps), security tools administration, threat monitoring, and the security service desk are located here as well. The service desk is an IT function that serves as a single point of contact for customers to resolve their computing or applications issues. Other parts of the cybersecurity program such as cyber threat intelligence may use security tools; however, SecOps generally handles their daily administration. Program sustainability is the primary focus of the operate phase.
- Improve - This phase is the process of continuous improvement. Most cybersecurity programs operate as a good practice, but moving to a best practice requires continuous improvement. I discuss the difference between good and best practices later in the chapter. Key performance metrics and regular assessments are used to baseline the program, and a maturity model is used to guide program improvem...
Table of contents
- Cover
- Title page
- Copyright
- Dedication
- Preface
- Introduction
- Foreword
- Chapter 1: Designing a Cybersecurity Program
- Chapter 2: Establishing a Foundation of Governance
- Chapter 3: Building a Cyber Threat, Vulnerability Detection, and Intelligence Capability
- Chapter 4: Building a Cyber Risk Management Capability
- Chapter 5: Implementing a Defense-in-Depth Strategy
- Chapter 6: Applying Service Management to Cybersecurity Programs
- Appendix A: Useful Checklists and Information
- Credits
- About the Author
- More From Rothstein Publishing
Frequently asked questions
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app