![]()
CHAPTER 1: INTRODUCTION TO PENETRATION TESTING
Penetration testing captures the imagination and sparks the interests of many people. It is part mystery, part challenge, part creativity and part risk. It has the glamour and mystique of doing something on the wild side of life by simulating a criminal act, but without the penalties. Therefore, it is no surprise that many people are drawn to penetration testing and want to know more about what it is, how to do it and, moreover, how they can use it to help protect their systems and defend their networks.
Protecting the systems and networks of today requires a broad understanding and in-depth knowledge of the tactics, tools and motivations of the adversary. The person given the responsibility to protect a system should know the nature and techniques of the enemy, and be able to prevent successful attacks by discovering and securing any vulnerabilities in their systems or networks before the adversary can find them.
Penetration testing is the simulation of an attack on a system, network, piece of equipment or other facility, with the objective of proving how vulnerable that system or “target” would be to a real attack.
Penetration testing is based on knowledge. The more knowledge the tester has, the more effective their attack will likely be. But what knowledge do they need? They need knowledge about the target, the operating environment, the users, the culture, the business itself, the physical security and, most of all, knowledge of how to use the tools (and their imagination) effectively.
Many people have a narrow and limited perception of penetration testing; they see it as an attack using a few common tools against a list of commonly known vulnerabilities. This type of testing provides some benefit to the organization, but is far too superficial and restrained to be really effective and meaningful. A pen test is innovative, probing, testing, evaluative, persistent and thorough.
In this booklet, we will examine various types of penetration tests, the tools commonly used, and the ways to leverage a pen test to provide the greatest possible benefit to the organization. The resulting penetration tests will deliver assurance and confidence to clients and business owners that their systems, networks and facilities are secure, that the level of risk to the organization of an attack is within acceptable levels, and that their information systems are being managed properly.
Case study
The General responsible for overseeing the security and operations of a military network requested a penetration test. The General was convinced that his network was secure, well-hidden and impenetrable. He had diligently instructed his staff to ensure that the network was well managed, unnecessary services were disabled, and that no extraneous information about the network was available anywhere outside of the network itself. He hired a top-quality pen testing team and challenged them to enter his network, but, at the same time, was convinced they would not even find it, let alone gain enough knowledge to launch a proper attack.
A couple of weeks into the test schedule, the pen testing team requested a meeting with the General. As he entered the meeting, the General asked if they had “given up already.” The team then laid in front of the General the information they had managed to access, and stated that they were required to cease the test once they had obtained such information under the rules of the engagement. (Note: these rules must be set out at the beginning of the test, since there may be serious implications and potential damage to the organization once the testing team has gained access – especially when succeeding in penetrating a military network.)
Upon reviewing the documents obtained by the pen testing team, the General exploded in rage, demanding to know how they had managed to obtain so much sensitive, classified material. He threatened to demote his entire technical team and launch a legal investigation into his department. It was at this point that the pen testing team advised the General that the General’s network was quite secure, and that the way they broke into the network was not through a sophisticated technical attack. They were able to access all of the information by simply sending a DVD that contained a Trojan horse to the General himself. When inserted into the General’s machine, the Trojan promptly copied the entire contents of the hard drive on the General’s machine to a secure server that the pen testing team had set up.
They delivered the DVD to the General using a journalist that had an interview with him to discuss a news article being written about technology in today’s military. The DVD contained video clips and articles as a sample of the work that the journalist had already done to prepare the article.
Such an attack should not have been successful – no foreign media should have been installed onto a classified machine, and both policies and technical controls should have prevented this. But what happens in reality? Many people, including Generals, senior managers and even technical staff, could fall for such an easy trick.
As can be seen in this case, there are many challenges involved in carrying out a successful pen test. The first is to gain approval to conduct the test, the second is to determine the rules of engagement, the third is to know the reporting structure and who to deliver the results to, the fourth is to ensure the pen test is not limited to a strictly technical attack and, finally, the fifth is to ensure that the test provides meaningful results and recommendations for the organization.
We all know that most organizations would fall for such an attack. There is no technical control that is sufficient to totally prevent user mistakes! The 2011 attacks against RSA (the security division of the EMC) are an example of how easy it can be to penetrate even the most security-conscious organization. In the case of RSA, the exploit was enabled through a simple spear phishing e-mail sent to an employee. The employee opened the attachment that was linked to the e-mail (which promised them a list of open employment positions) and thereby launched the hacking tool that provided a backdoor into the company for the attacker to use1.
The purpose of a pen test is to find any problems on the system and network, and in the user training, business procedures and operational controls related to the system being tested. A successful pen test is one that discovers the vulnerabilities and determines the level of risk they pose to the organization. An unsuccessful pen test is one where the team fails to find existing serious vulnerabilities and provides management with a false assurance of security, or one that provides the organization with a flood of meaningless data that is not sorted according to priorities or levels of risk.
The many breaches that Sony experienced in 2011 were mostly the result of simple attacks. The vulnerabilities that allowed the attacks to do the damage and compromise those systems affected should have been found by competent pen testers and thereby corrected. The Verizon-USSS data breach report of 2010 indicated that 96% of all data breaches were avoidable through simple or intermediate controls2. This is where many pen tests are failing. The pen tester bears the responsibility to perform their duties in a professional and competent manner, and thereby provide the information required by their clients to strengthen and secure their systems and networks.
Security basics
Penetration testing is a process of testing and validating the security posture and maturity of an organization. In order to test the security program, it is necessary for the pen tester to know what to look for and what the security priorities are.
The first problem is that the term “security” is an abstract term and can mean many different things to different people.
Definition
One resource3 defines security in the following ways:
1. Freedom from danger, risk, etc.; safety
2. Freedom from care, anxiety, or doubt; well-founded confidence
3. Something that secures or makes safe; protection; defense
4. Freedom from financial cares or from want
5. Precautions taken to guard against crime, attack, sabotage, espionage, etc.
We can see many positive aspects of security – freedom from worry and danger, for example – but we also see that security is very much an emotional term, conveying a sense of safety and protection. The last definition is most relevant for us: “precautions taken to guard.”
A pen tester is not testing emotion or a feeling of safety; the tester is testing the precautions, the defenses and the levels of risk or danger.
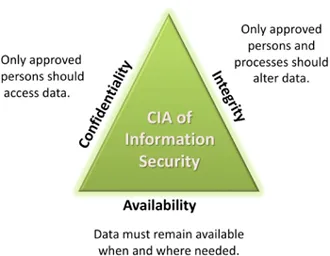
The information security triad
For many years, the information security industry has defined the term “security” as comprising three core elements: confidentiality, integrity and availability. There are good reasons for this. Using these three elements to define security gives a more complete picture, and provides a way to move the term away from an abstract, emotion-based meaning to one denoting something solid and measureable.
Figure 1: The CIA triad
Confidentiality
Confidentiality is based on confidence – trust and assurance that the organization is protecting sensitive information and systems from unauthorized access and disclosure. This requires the organization to know what information it has that requires protection. It starts with the classification of systems and data according to the level of damage that would occur if the security of that system or data was compromised.
The objective of an attacker is not just to prove that they can get access. They want ...