
- 51 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
About this book
Where your information security is concerned, prevention is better than cure.
If you want to tackle the problem of information security, you cannot rely on the help of technology alone. Information security breaches tend to occur as a result of human, as well as technological, failings. However, the human factor usually receives far less attention. Training
Computer systems are complex, so people who work with them often need to be trained in how to use them correctly. This applies especially to your company's information security. The loss of a memory stick by a careless employee, or the downloading of a file that contains a virus, may be all it takes to cause a security breach.
Practical advice
This book offers you practical advice on how to develop an IT Induction programme for your staff that can help safeguard your business information. By providing your employees with simple instruction in good IT working practices, and by making sure they know what is expected of them, you can strengthen your company's information security and reduce the risk that your data will be stolen or lost.
A sense of responsibility
Encouraging good corporate working and a strong sense of responsibility are, the author argues, essential for the protection of your business information. She shows you how to strike the right balance in your approach to staff training, thereby enabling you to provide your employees with an IT Induction that is at once informative and accessible.
Benefits to business include:
- Reduce the likelihood of a damaging security breach. Putting in place a programme of IT Induction will help ensure that your company's staff are following information security best practice. Educating employees in good IT working practices will help them to avoid the errors that might otherwise put your organisation at risk.
- Protect the company's reputation. The damage an information security breach can do to your business goes beyond the initial cost of clearing up the mess. Without proper staff training, the danger is that theft or loss of data will damage your company's reputation. You need to provide your staff with a proper IT Induction in order to preserve good relations with your customers.
- Avoid legal complications. IT offers business new, less formal means of communication. Employees write e-mails in a different style from the way they write letters. However, contracts can be made or broken via e-mail, and e-mail correspondence can be cited in litigation. An IT Induction programme will give your staff the appropriate guidance on e-mail communication with the clients or business partners of your company.
- Manage employee working practices. Laptop computers and broadband mean that for many employees, the boundaries between work and home are becoming blurred. If you allow your staff to mix and match between working in the office and working from home, you need to make sure they know what they have to do to safeguard your firm's data both inside and outside the office.
Tools to learn more effectively

Saving Books

Keyword Search

Annotating Text

Listen to it instead
Information
CHAPTER 1:
PUTTING IT INDUCTION IN PERSPECTIVE
To explain:
So what is the relationship between IT Induction and Information Security Awareness?
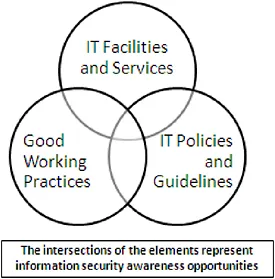
How does an ICT Code of Conduct fit with IT Induction?
CHAPTER 2:
THE TARGET AUDIENCE
Table of contents
- FOREWORD
- PREFACE
- ABOUT THE AUTHOR
- CONTENTS
- CHAPTER 1: PUTTING IT INDUCTION IN PERSPECTIVE
- CHAPTER 2: THE TARGET AUDIENCE
- CHAPTER 3: WHOSE RESPONSIBILITY IS IT ANYWAY?
- CHAPTER 4: INDICATIVE CONTENT
- CHAPTER 5: DELIVERY OPTIONS
- CHAPTER 6: MAKING IT INDUCTION PART OF A NEW USER PROCESS
- CHAPTER 7: IT INDUCTION – A ONE TIME ONLY EXPERIENCE?
- ITG RESOURCES
Frequently asked questions
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app