
- 137 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
The Tao of Open Source Intelligence
About this book
What is OSINT and what can it do for you?
The Internet has become the defining medium for information exchange in the modern world, and the unprecedented success of new web publishing platforms such as those associated with social media has confirmed its dominance as the main information exchange platform for the foreseeable future.
But how do you conduct an online investigation when so much of the Internet isn't even indexed by search engines? Accessing and using the information that's freely available online is about more than just relying on the first page of Google results.
Open source intelligence (OSINT) is intelligence gathered from publically available sources, and is the key to unlocking this domain for the purposes of investigation.
Product overview
The Tao of Open Source Cyber Intelligence provides a comprehensive guide to OSINT techniques, for the investigator:
- It catalogues and explains the tools and investigative approaches that are required when conducting research within the surface, deep and dark webs.
- It explains how to scrutinise criminal activity without compromising your anonymity – and your investigation.
- It examines the relevance of cyber geography and how to get round its limitations
- It describes useful add-ons for common search engines, as well as considering Metasearch engines (including Dogpile, Zuula, PolyMeta, iSeek, Cluuz, and Carrot2) that collate search data from single-source intelligence platforms such as Google.
- It considers deep web social media platforms and platform-specific search tools, detailing such concepts as concept mapping, Entity Extraction tools, and specialist search syntax (Google Kung-Fu).
- It gives comprehensive guidance on Internet security for the smart investigator, and how to strike a balance between security, ease of use and functionality, giving tips on counterintelligence, safe practices, and debunking myths about online privacy.
OSINT is a rapidly evolving approach to intelligence collection, and its wide application makes it a useful methodology for numerous practices, including within the criminal investigative community.
The Tao of Open Source Cyber Intelligence is your guide to the cutting edge of this information collection capability.
About the author
Stewart K. Bertram is a career intelligence analyst who has spent over a decade working across the fields of counterterrorism, cyber security, corporate investigations and geopolitical analysis. The holder of a Master's degree in Computing and a Master of Letters in Terrorism studies, Stewart is uniquely placed at the cutting edge of intelligence and investigation, where technology and established tradecraft combine. Stewart fuses his academic knowledge with significant professional experience, having used open source intelligence on such diverse real-world topics as the terrorist use of social media in Sub-Saharan Africa and threat assessment at the London Olympic Games. Stewart teaches courses on open source intelligence as well as practising what he preaches in his role as a cyber threat intelligence manager for some of the world's leading private-sector intelligence and security agencies.
Tools to learn more effectively

Saving Books

Keyword Search

Annotating Text

Listen to it instead
Information
CHAPTER 1: THE SURFACE WEB


Web browsers – the first steps

Flexibility
Extendibility with Add-Ons
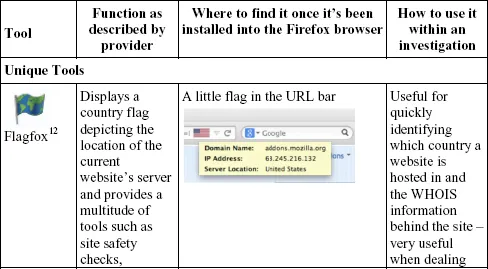
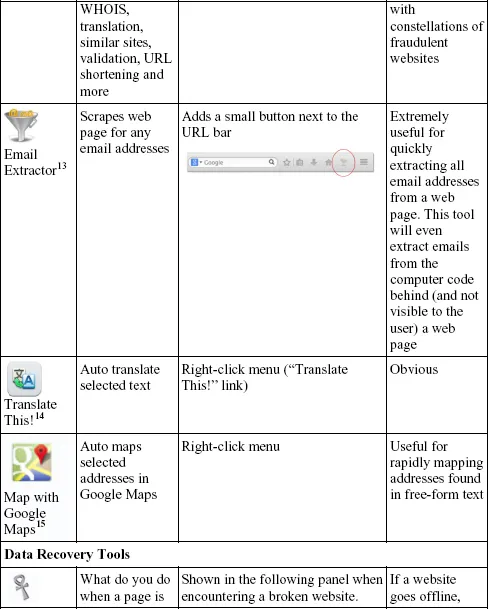

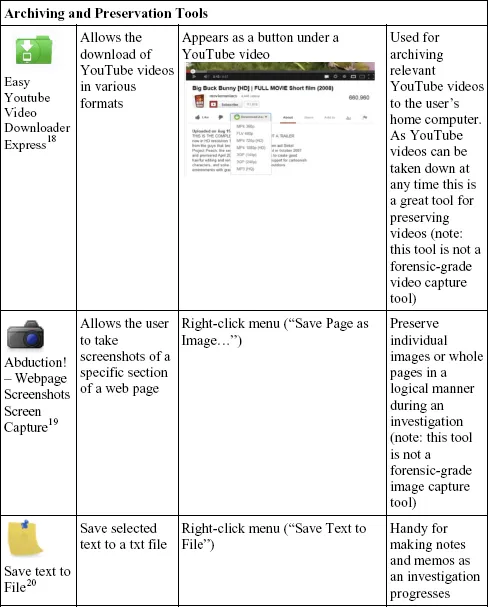
Speed
Table of contents
- Cover
- Title
- Copyright
- Preface
- About the Author
- Acknowledgements
- Dedication
- Contents
- Introduction: “What Can Open Source Intelligence Do For Me?”
- Chapter 1: The Surface Web
- Chapter 2: Deep Web
- Chapter 3: The Dark Web
- Chapter 4: Internet Security for the Smart Investigator
- Conclusion
- Annex A: Tips for Building a Credible Sock Puppet
- ITG Resources
Frequently asked questions
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app