
- 328 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
An Introduction to the Analysis of Algorithms
About this book
-->
A successor to the first and second editions, this updated and revised book is a leading companion guide for students and engineers alike, specifically software engineers who design algorithms. While succinct, this edition is mathematically rigorous, covering the foundations for both computer scientists and mathematicians with interest in the algorithmic foundations of Computer Science.
Besides expositions on traditional algorithms such as Greedy, Dynamic Programming and Divide & Conquer, the book explores two classes of algorithms that are often overlooked in introductory textbooks: Randomised and Online algorithms — with emphasis placed on the algorithm itself. The book also covers algorithms in Linear Algebra, and the foundations of Computation.
The coverage of Randomized and Online algorithms is timely: the former have become ubiquitous due to the emergence of cryptography, while the latter are essential in numerous fields as diverse as operating systems and stock market predictions.
While being relatively short to ensure the essentiality of content, a strong focus has been placed on self-containment, introducing the idea of pre/post-conditions and loop invariants to readers of all backgrounds, as well as all the necessary mathematical foundations. The programming exercises in Python will be available on the web (see http://www.msoltys.com/book for the companion web site).
-->
--> Contents:
- Preliminaries
- Greedy Algorithms
- Divide and Conquer
- Dynamic Programming
- Online Algorithms
- Randomized Algorithms
- Algorithms in Linear Algebra
- Computational Foundations
- Mathematical Foundations
-->
--> Readership: Students of undergraduate courses in algorithms and programming and associated professionals. -->
Keywords:Algorithms;Greedy;Dynamic Programming;Online;Randomized;Loop InvariantReview:0
Frequently asked questions
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app.
Information
Chapter 1
Preliminaries
1.1What is correctness?
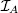
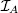
1.1.1Complexity
Table of contents
- Cover Page
- Title
- Copyright
- Dedication
- Preface
- Contents
- 1. Preliminaries
- 2. Greedy Algorithms
- 3. Divide and Conquer
- 4. Dynamic Programming
- 5. Online Algorithms
- 6. Randomized Algorithms
- 7. Algorithms in Linear Algebra
- 8. Computational Foundations
- 9. Mathematical Foundations
- Bibliography
- Index