
Mastering Rust
Learn about memory safety, type system, concurrency, and the new features of Rust 2018 edition, 2nd Edition
- 554 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
Mastering Rust
Learn about memory safety, type system, concurrency, and the new features of Rust 2018 edition, 2nd Edition
About this book
Become proficient in designing, developing and deploying effective software systems using the advanced constructs of Rust
Key Features
- Improve your productivity using the latest version of Rust and write simpler and easier code
- Understand Rust's immutability and ownership principle, expressive type system, safe concurrency
- Deep dive into the new doamins of Rust like WebAssembly, Networking and Command line tools
Book Description
Rust is an empowering language that provides a rare combination of safety, speed, and zero-cost abstractions. Mastering Rust – Second Edition is filled with clear and simple explanations of the language features along with real-world examples, showing you how you can build robust, scalable, and reliable programs.
This second edition of the book improves upon the previous one and touches on all aspects that make Rust a great language. We have included the features from latest Rust 2018 edition such as the new module system, the smarter compiler, helpful error messages, and the stable procedural macros. You'll learn how Rust can be used for systems programming, network programming, and even on the web. You'll also learn techniques such as writing memory-safe code, building idiomatic Rust libraries, writing efficient asynchronous networking code, and advanced macros. The book contains a mix of theory and hands-on tasks so you acquire the skills as well as the knowledge, and it also provides exercises to hammer the concepts in.
After reading this book, you will be able to implement Rust for your enterprise projects, write better tests and documentation, design for performance, and write idiomatic Rust code.
What you will learn
- Write generic and type-safe code by using Rust's powerful type system
- How memory safety works without garbage collection
- Know the different strategies in error handling and when to use them
- Learn how to use concurrency primitives such as threads and channels
- Use advanced macros to reduce boilerplate code
- Create efficient web applications with the Actix-web framework
- Use Diesel for type-safe database interactions in your web application
Who this book is for
The book is aimed at beginner and intermediate programmers who already have familiarity with any imperative language and have only heard of Rust as a new language. If you are a developer who wants to write robust, efficient and maintainable software systems and want to become proficient with Rust, this book is for you. It starts by giving a whirlwind tour of the important concepts of Rust and covers advanced features of the language in subsequent chapters using code examples that readers will find useful to advance their knowledge.
Frequently asked questions
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app.
Information
Memory Management and Safety
- Programs and memory
- Memory allocations and safety
- Memory management
- Stack and Heap
- Trifecta of safety—Ownership, borrowing, and lifetimes
- Smart pointer types
Programs and memory
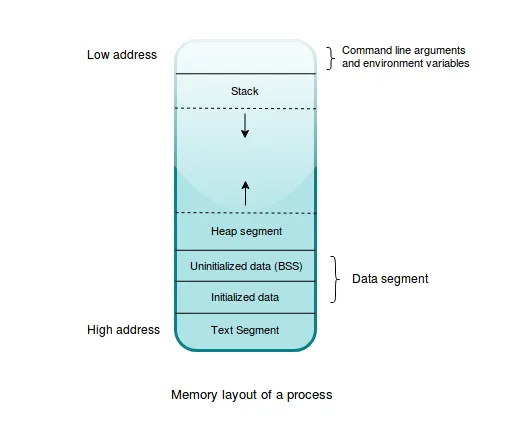
- Text segment: This section contains the actual code to be executed in the compiled binary. The text segment is a read-only segment and any user code is forbidden to modify it. Doing so can result in a crash of the program.
- Data segment: This is further divided into subsections, that is, the initialized data segment and uninitialized data segment, which is historically known as Block Started by Symbol (BSS), and holds all global and static values declared in the program. Uninitialized values are initialized to zero when they are loaded into memory.
- Stack segment: This segment is used to hold any local variables and the return addresses of functions. All resources whose sizes are known in advance and any temporary/intermediary variables that a program creates are implicitly stored on the stack.
- Heap segment: This segment is used to store any dynamically allocated data whose size is not known up front and can change at runtime depending on the needs of the program. This is the ideal allocation place when we want values to outlive their declaration within a function.
How do programs use memory?
Memory management and its kinds
Table of contents
- Title Page
- Copyright and Credits
- About Packt
- Contributors
- Preface
- Getting Started with Rust
- Managing Projects with Cargo
- Tests, Documentation, and Benchmarks
- Types, Generics, and Traits
- Memory Management and Safety
- Error Handling
- Advanced Concepts
- Concurrency
- Metaprogramming with Macros
- Unsafe Rust and Foreign Function Interfaces
- Logging
- Network Programming in Rust
- Building Web Applications with Rust
- Interacting with Databases in Rust
- Rust on the Web with WebAssembly
- Building Desktop Applications with Rust
- Debugging
- Other Books You May Enjoy