
- 84 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
About this book
Cyber security could be defined as, beginning of the concept of trust and belief in cyber transactions. The era of computing began in the 20th century, with an enormous investment on computational research. Software programing languages were the foundational blocks of history of computing. Progressive research then led to networking, bringing about the formation of connectivity. Along with these creations, there was an accompanying factor of compromise on data privacy and hacking of data. This factor was the introduction to cyber security.
This book is primarily created for the objective of knowledge sharing and knowledge-enabling on the conceptual ideologies of the cybersecurity. This book is aimed at students, early-career researchers, and also advanced researchers and professionals. The case studies described in the book create renewed knowledge on the innovations built on the applied theories of cybersecurity. These case studies focus on the financial markets and space technologies.
Frequently asked questions
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app.
Information
CHAPTER 1
Introduction to Cybersecurity

CHAPTER 2
Theory of Cybersecurity
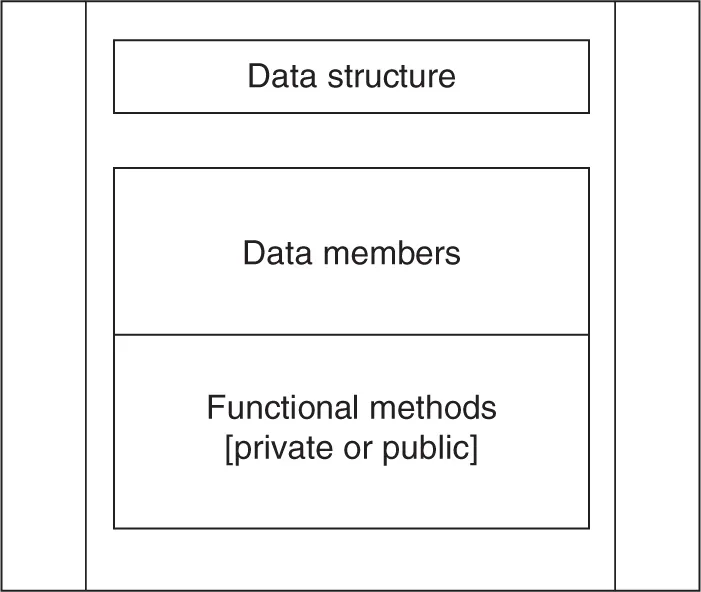
Data Members
Functional Methods
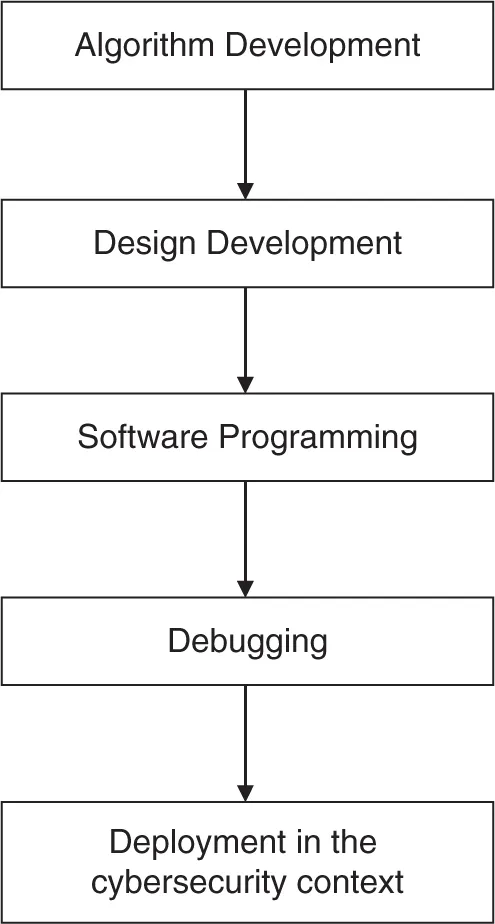
Program Contribution to Data Structure

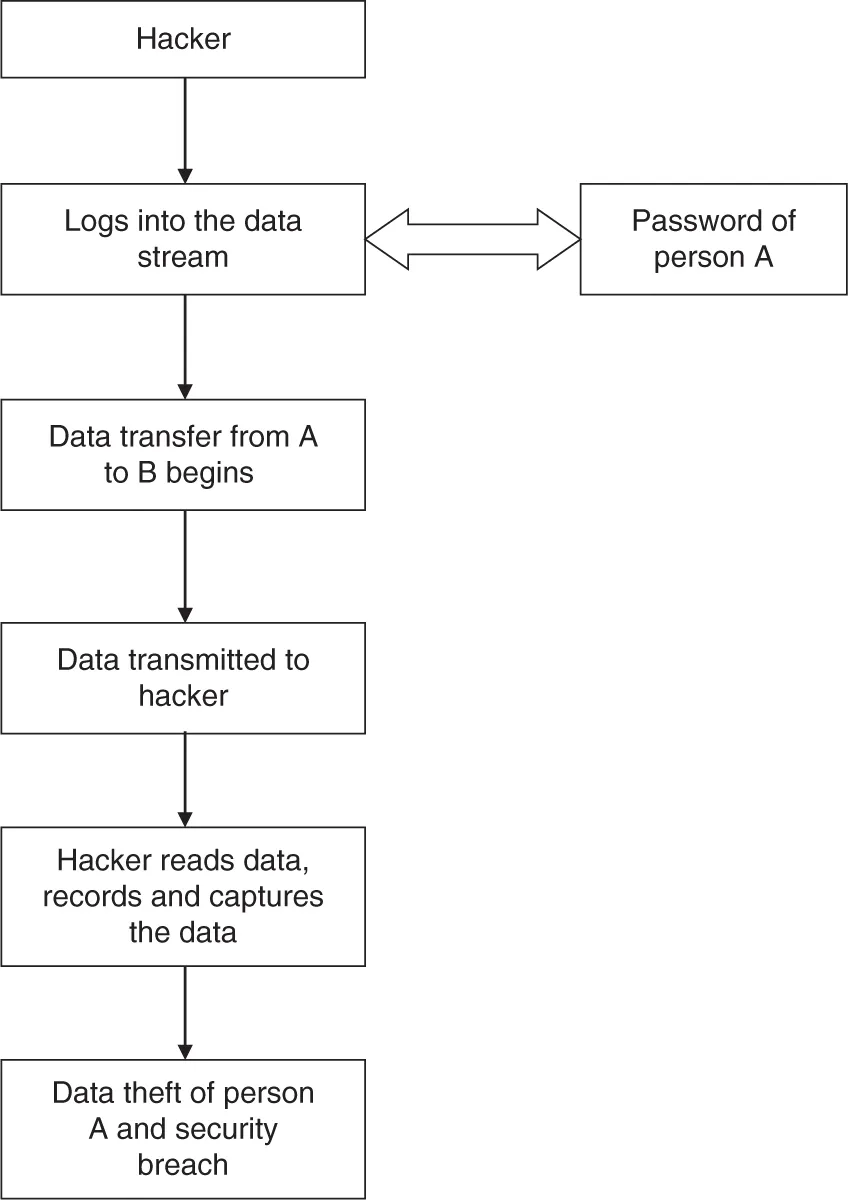
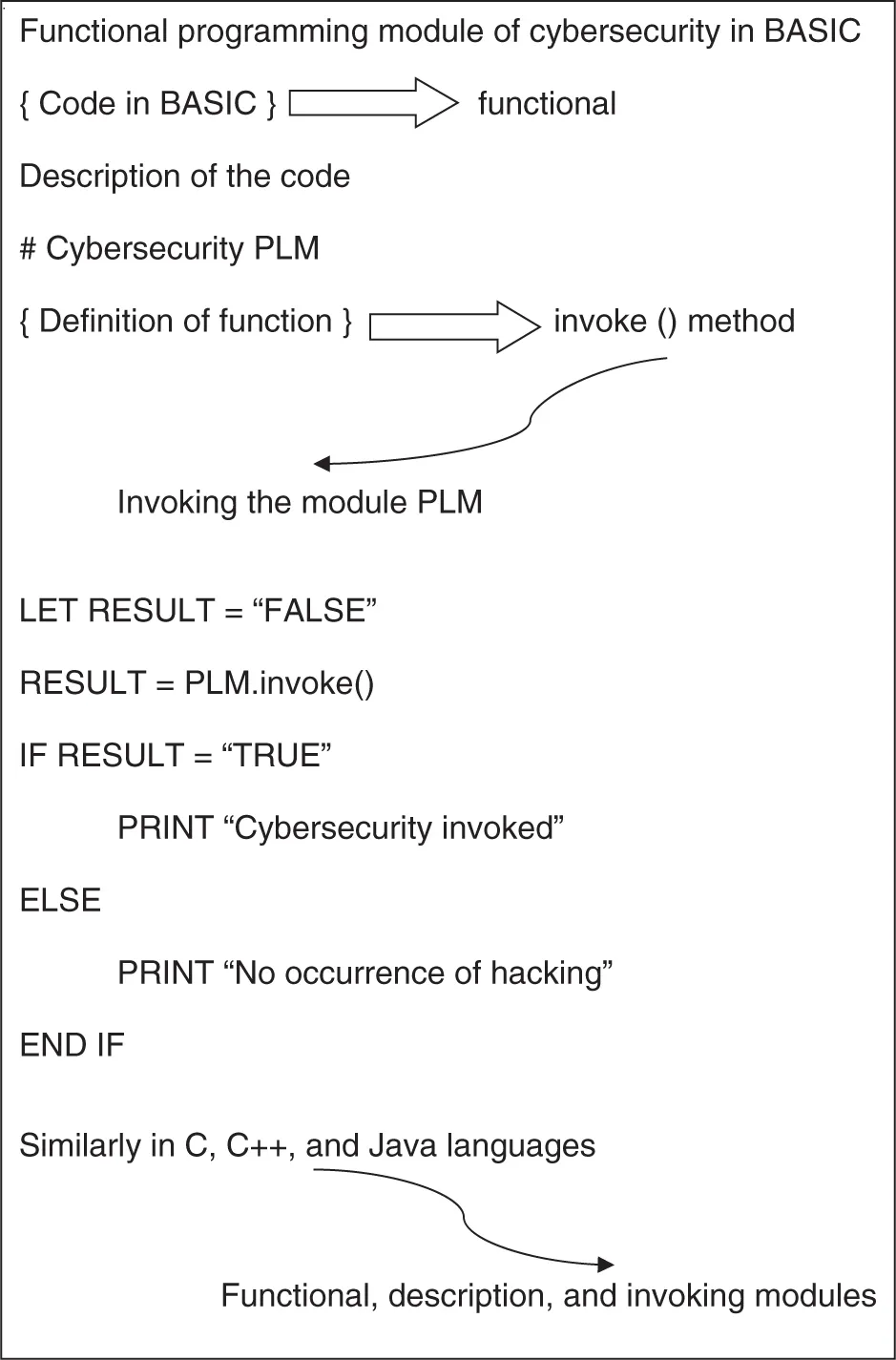
Database Design of the Cybersecurity Module

CHAPTER 3
Emerging Technologies for the Theories of Cybersecurity
Table of contents
- Cover
- Halftitle Page
- Title Page
- Copyright Page
- Contents
- Acknowledgments
- Chapter 1 Introduction to Cybersecurity
- Chapter 2 Theory of Cybersecurity
- Chapter 3 Emerging Technologies for the Theories of Cybersecurity
- Chapter 4 Innovative Ideologies of the Theories of Blockchain Technologies
- Chapter 5 ICTs Introduced into the Applications of the Concept of Digital Financial Services and Financial Inclusion
- Chapter 6 The Various Steps of the Processes of Building Cyber Secure Applications
- Chapter 7 The Types of Risks that Emerge With the Concept of Fraud
- Chapter 8 Consumer Protection and Financial Inclusion
- Chapter 9 Solar Flares and Quantum Neural Networks
- About the Author
- Index