
- 60 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
eBook - ePub
About this book
This report offers an analytical framework that allows for more systemic assessments of distributed ledger technology (DLT) and its applications. It examines the evolution and typology of the emergent technology, its existing and projected applications, and regulatory and policy issues that they entail. This report highlights the trends, concerns, and potential opportunities of DLTs, especially for Asian markets. It also identifies the benefits and risks to using DLT and offers a functional and proportional approach to these issues.
Frequently asked questions
Yes, you can cancel anytime from the Subscription tab in your account settings on the Perlego website. Your subscription will stay active until the end of your current billing period. Learn how to cancel your subscription.
No, books cannot be downloaded as external files, such as PDFs, for use outside of Perlego. However, you can download books within the Perlego app for offline reading on mobile or tablet. Learn more here.
Perlego offers two plans: Essential and Complete
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
We are an online textbook subscription service, where you can get access to an entire online library for less than the price of a single book per month. With over 1 million books across 1000+ topics, we’ve got you covered! Learn more here.
Look out for the read-aloud symbol on your next book to see if you can listen to it. The read-aloud tool reads text aloud for you, highlighting the text as it is being read. You can pause it, speed it up and slow it down. Learn more here.
Yes! You can use the Perlego app on both iOS or Android devices to read anytime, anywhere — even offline. Perfect for commutes or when you’re on the go.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app.
Yes, you can access Distributed Ledger Technology and Digital Assets by in PDF and/or ePUB format, as well as other popular books in Business & E-Commerce. We have over one million books available in our catalogue for you to explore.
Information
1. Introduction
Distributed ledger technology (DLT) and blockchain have attracted massive investment interest in recent years,1 with asset values, projects, and investment hitting records in 2017. This is particularly so since alternative currencies, such as Bitcoin, a cryptoasset, have risen to global attention.
This investment interest reflects the very real transformative potential of DLT, especially in the financial sector. Many financial institutions are investing heavily in proof-of-concept demonstrations and the rollout of pilot applications of DLT, in addition to a range of high-profile consortium projects and an ever increasing range of startups.
Proponents hold out a long list of the potential promise of DLT—from capital raising and trading, to deposits and lending, to property and casualty claims processing (InsurTech), to digital identity management and authentication, to regulatory technology such as anti-money laundering and client-suitability checks. This report finds it likely that over time, DLT will become a useful tool in several contexts.
It is also true, however, that these developments warrant close attention to DLT by regulators as they aim to strike a balance between the potential benefits and the pitfalls. An increasing number of jurisdictions in Asia have become concerned about risks, particularly with nonsovereign cryptoassets and initial coin offerings (ICOs). This report therefore aims to clarify the most prominent issues.
It is now clear that Bitcoin and a number of other cryptoassets—regardless of their eventual long-term performance—were the focus of one of the biggest speculative bubbles in history, with a large volume of mining and trading taking place in Asia. The Bitcoin Bubble of 2017 and 2018 has now joined the Tulip Mania of 1637, the South Sea Bubble of 1720, the Dot.com Bubble of 2000, and many others.2 During 2017, the price of Bitcoin and other cryptoassets increased dramatically, before falling steeply in 2018 (Figure 1).
Figure 1: Major Cryptoasset Price Changes, 2013–2018
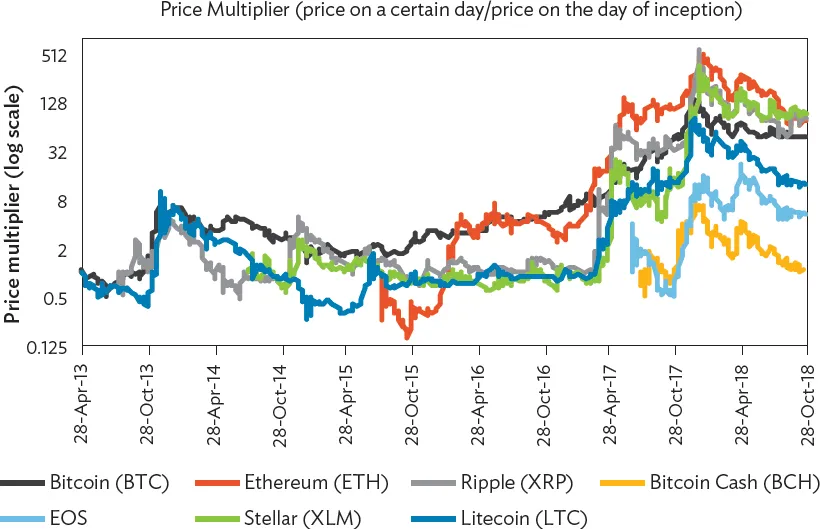
Notes: The price multiplier shows the price change of each cryptoasset since its inception. A value above 1 (below 1) indicates the price has increased (decreased) by the factor. Period: 28 April 2013 to 31 October 2018.
Source: Coinmarketcap. https://coinmarketcap.com/(accessed 15 November 2018).
Over the past 24 months, the “tokenization” of assets and creation of using ICOs, has also exploded.3 ICOs typically use blockchain technology to offer tokens that confer various rights in return, most often for cryptoassets. These offerings can be seen as a conjunction of crowdfunding and blockchain.
Although ICOs have indeed displayed the hallmarks of a classic speculative bubble, it must be noted that the tulip hysteria notwithstanding, such investment crazes are often not without foundation. The joint stock company, the internet, and other advances of the past clearly demonstrate this fact. Afterall, at the height of the dot.com bubble in the late 1990s and early 2000s, no one would have ever expected Amazon and Google to become as significant as they have. This is the core of Amara’s law:
“We tend to overestimate the effect of a technology in the short run and underestimate the effect in the long run.” (Amara 2006).
While the law may be dull and the technology exciting, the impact of sovereigns and their institutions—in particular, central banks, regulatory agencies, and legal systems—cannot be simply wished away. Risk will remain from both a legal and technological standpoint. (Zetzsche, Buckley, and Arner 2018, 1407). Policymakers and regulators seeking to support appropriate approaches to 21st century financial infrastructure must focus on these potential consequences.
A disparate range of policy and regulatory responses across Asia has accompanied the surge in DLT activity, with substantial differences between approaches to the specific contexts of cryptoassets and ICOs, as compared to DLT and blockchain more generally.4 While there are common features in the regulatory responses, such as the issuance of cautions in most jurisdictions in relation to the investment risks associated with ICOs and a slow shift toward regulation of these applications, policy approaches seem diverse across jurisdictions.
Both the People’s Republic of China (PRC) and the Republic of Korea, for example, announced in 2013 that cryptoassets were to be treated as “virtual commodities” and not currencies. This restrictive approach has continued to date with the banning of ICOs. However, the Republic of Korea recently announced plans to allow ICOs in the near future. Singapore and Japan have both taken permissive approaches and early steps toward the regulation of these technologies. In 2014, Japan began developing cryptoasset regulations, and in 2016 recognized virtual currency as a legal means of payment subject to anti-money-laundering and know-your-customer requirements. In Singapore, cryptoassets have been regulated since 2014, and the jurisdiction has since engaged in a number of blockchain development projects. Thailand similarly issued its own regulatory approach to ICOs in 2017.
Other jurisdictions in Asia have taken less active approaches to the regulation of these technologies, and have instead issued cautions or similar alerts about associated risks. For example, in 2017, Malaysia issued cautions about the risks of virtual currencies while Macau, China issued cautions about the risks of ICOs.
Taking all this into account, this report aims to expand knowledge of the applications of the new technologies. As the report illuminates the trends in Asia for DLT and related concerns, risks and its very real potential, the report focuses on policy options and approaches to balancing risks and supporting useful innovation in the region.
2. Distributed Ledger Technology, Blockchain, and Applications
As is often the case with new technologies and other innovations, confusion frequently surrounds terminology arising out of emergent applications and the different perspectives of those involved. The best way to understand the field of DLT, blockchain, and related applications is to begin with the relevant underlying technology. A “distributed ledger” is a digital database that is shared, independently updated, and synchronized by consensus among the network participants. It is the underlying technology for blockchain which is, in fact, a form of distributed ledger with each block of transaction records linked by cryptographic signatures.
Section 2.1 provides typologies of DLT. The first sets forth the differences between centralized and distributed ledgers, and offers an explanation for the benefits of DLT over centralized ledgers that are currently the most common data storage system. Second is the difference between “permissioned” (such as Corda)5 versus “permissionless” structures (such as Bitcoin) within those distributed ledgers. Section 2.2 zooms in on blockchain, which refers to how data are stored as a “block” on a distributed ledger and “smart contracts” as one aspect of this. It also reviews a range of applications, including cryptoassets and ICOs. Section 2.3 discusses the potential of DLT beyond blockchain and its implications.
2.1 About Distributed Ledger Technology
Centralized and Distributed Ledgers
Distributed ledgers are perhaps best understood diagrammatically and in contrast to their counterpart, the centralized ledger (Figure 2).
Figure 2: Distributed Communication Networks: Definition of Redundancy Level
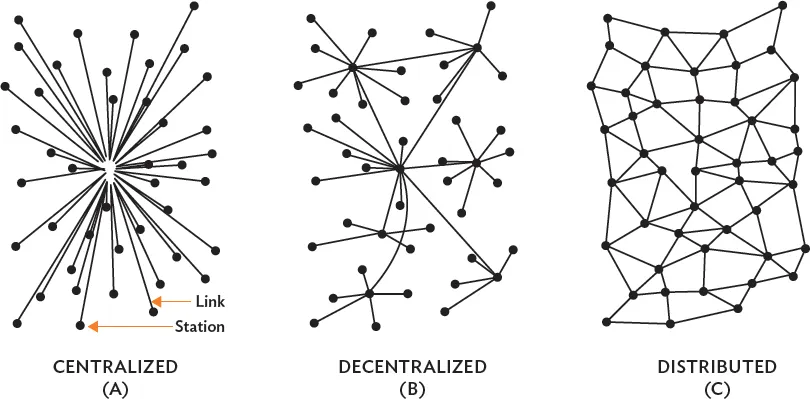
Sources: Mougayar 2015. Baran, P. 1962. On Distributed Communication Networks. Rand Corporation. Paper. Quoted in Mougayar 2015. Understanding the Blockchain. O’Reilly. 16 January.
Centralized ledgers are the most common data storage device in finance today. A trusted administrator maintains the stored data, recording transfers of assets and the like upon receipt of appropriately verified notifications. Examples of their use by the financial sector include most securities clearing and settlement systems and central counterparties as well as large value payment systems, including real time gross settlement in many jurisdictions across Asia. Others include traditional property registries whether digital or not. Centralized structures are typically secure because the single controlling entity can focus on this security aspect as well as speed of execution.
Centralized structures face risks, however. A ledger stored on a network server can be destroyed or, more likely, hacked or otherwise compromised, so that the original data are held for ransom or manipulated and replaced with new (inaccurate) data. Mathematical approaches can be used to determine how much effort is necessary to manipulate any given server. Every single server can be manipulated with sufficient computing power.
Centralized structures thus concentrate risk and use that concentration to focus security and management. Perhaps the best example of this comes in central counterparty clearing, which has been a major focus of post-2008 global financial regulatory reforms. For instance, central counterparty clearing in over-the-counter derivatives or securities exchanges provides a trusted central counterparty for transactions, reducing counterparty risk and interconnections with potential systemic implications in the financial system. At the same time, however, central counterparty clearing centralizes and concentrates risk and thus arguably creates a new form of systemic risk, highlighted in a range of processes from the Financial Stability Board, the Bank for International Settlements Committee on Payment and Market Infrastructure, and the International Organization of Securities Commissions (IOSCO) to develop regulatory approaches to systemically important financial market infrastructure, such as central counterparties and major payment systems, among others.
Distributed ledgers6 address these problems by raising the barriers for manipulation of stored data. In distributed ledgers, many data storage points (nodes) are connected with each other and store all data simultaneously, and together constitute the common ledger. DLT requires consensus of those nodes. However, the technical details of how to achieve consensus vary—multiple concepts have been developed, such as proof-of-work, proof-of-stake, proof-of-authority, and many others.7
To illustrate, assume that in distributed communication networks, there are N nodes (rather than one centralized ledger) and E describes the effort necessary to break into any single server. Given that all other conditions such as the security of each server are equal, it is expected that the efforts necessary to manipulate all servers linked in the ledger would be N x E rather than 1 x E. The number of servers that will need to be manipulated to alter the outcome will depend on the number of servers necessary for consensus (C). If C>1, the distributed ledger is more secure than the centralized one. As already noted, this calculation is rather simplistic, since it assumes equal security of each server. In real-life applications, the security of the central node on a centralized ledger is likely to be far superior to that of each of the distributed nodes. This calculation also assumes that the manipulation of existing nodes is necessary to alter the overall consensus, whereas, in reality, consensus can be steered by other factors (such as control of the majority of processing power in a proof-of-work system). Furthermore, the calculation will be noticeably more difficult in an open, “permissionless” distributed database where new nodes can be easily added to the ledger (in which case one could simply create a sufficient number of new nodes to achieve C).
DLT systems thus offer the potential for greater security without the risks of concentration of centralized ledger systems. At the same time, however, they typically suffer in speed of execution when compared to centralized systems.
Permissioned and Permissionless Systems
DLT can also take various forms. In particular, DLT systems can be permissioned or permissionless. Permissioned systems are essentially private networks with a predefined governance structure where data authorization depends upon the agreement of multiple predefined servers. The leading example in the financial sector is Corda, under the governance of R3, a global consortium of financial institutions and related organizations.
In contrast, permissionless DLT systems, such as Bitcoin, operate on public domain software and allow anyone who downloads and runs the software to participate. In some cases, even the code is further developed in the public domain. The participants in those distributed ledgers may not know who else is running a server functioning as a node at any given time. There is an additional security element in this “unknown” inherent in this structure: if ...
Table of contents
- Front Cover
- Title Page
- Copyright Page
- Contents
- Tables, Figures, and Box
- Foreword
- Acknowledgments
- Abbreviations
- Executive Summary
- 1. Introduction
- 2. Distributed Ledger Technology, Blockchain, and Applications
- 3. Cryptoassets
- 4. Initial Coin Offerings and Tokenization
- 5. Distributed Ledger Technology: Risks and Concerns
- 6. Policy Issues and Suggestions
- Appendixes
- References
- Footnotes
- Back Cover