
Dynamic Vulnerability Assessment and Intelligent Control
For Sustainable Power Systems
- English
- ePUB (mobile friendly)
- Available on iOS & Android
Dynamic Vulnerability Assessment and Intelligent Control
For Sustainable Power Systems
About this book
Identifying, assessing, and mitigating electric power grid vulnerabilities is a growing focus in short-term operational planning of power systems. Through illustrated application, this important guide surveys state-of-the-art methodologies for the assessment and enhancement of power system security in short term operational planning and real-time operation. The methodologies employ advanced methods from probabilistic theory, data mining, artificial intelligence, and optimization, to provide knowledge-based support for monitoring, control (preventive and corrective), and decision making tasks.
Key features:
- Introduces behavioural recognition in wide-area monitoring and security constrained optimal power flow for intelligent control and protection and optimal grid management.
- Provides in-depth understanding of risk-based reliability and security assessment, dynamic vulnerability assessment methods, supported by the underpinning mathematics.
- Develops expertise in mitigation techniques using intelligent protection and control, controlled islanding, model predictive control, multi-agent and distributed control systems
- Illustrates implementation in smart grid and self-healing applications with examples and real-world experience from the WAMPAC (Wide Area Monitoring Protection and Control) scheme.
Dynamic Vulnerability Assessment and Intelligent Control for Power Systems is a valuable reference for postgraduate students and researchers in power system stability as well as practicing engineers working in power system dynamics, control, and network operation and planning.
Frequently asked questions
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app.
Information
Chapter 1
Introduction: The Role of Wide Area Monitoring Systems in Dynamic Vulnerability Assessment
1.1 Introduction
1.2 Power System Vulnerability
1.2.1 Vulnerability Assessment
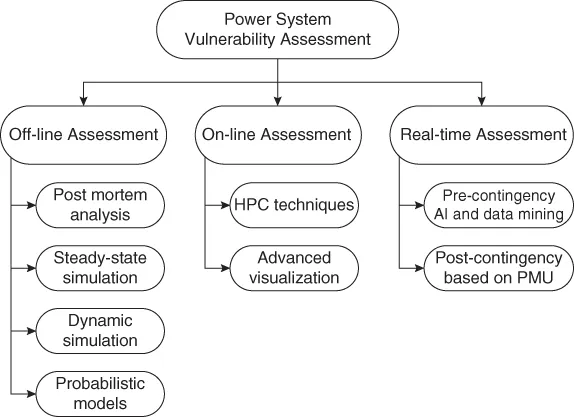
- Off-line assessment: Off-line assessment is done using conventional methods that are based on different complex model simulations; these usually involve time-consuming tasks, which restricts on-line applications. The high complexity is provoked by the huge number and diversity of the components that constitute an electric power system and their particular performance during dynamic phenomena. Among t...
Table of contents
- Cover
- Title Page
- Copyright
- Table of Contents
- List of Contributors
- Foreword
- Preface
- Chapter 1: Introduction: The Role of Wide Area Monitoring Systems in Dynamic Vulnerability Assessment
- Chapter 2: Steady-State Security
- Chapter 3: Probabilistic Indicators for the Assessment of Reliability and Security of Future Power Systems
- Chapter 4: An Enhanced WAMS-based Power System Oscillation Analysis Approach
- Chapter 5: Pattern Recognition-Based Approach for Dynamic Vulnerability Status Prediction
- Chapter 6: Performance Indicator-Based Real-Time Vulnerability Assessment
- Chapter 7: Challenges Ahead Risk-Based AC Optimal Power Flow Under Uncertainty for Smart Sustainable Power Systems
- Chapter 8: Modeling Preventive and Corrective Actions Using Linear Formulation
- Chapter 9: Model-based Predictive Control for Damping Electromechanical Oscillations in Power Systems
- Chapter 10: Voltage Stability Enhancement by Computational Intelligence Methods
- Chapter 11: Smart Control of Offshore HVDC Grids
- Chapter 12: Model Based Voltage/Reactive Control in Sustainable Distribution Systems
- Chapter 13: Multi-Agent based Approach for Intelligent Control of Reactive Power Injection in Transmission Systems
- Chapter 14: Operation of Distribution Systems Within Secure Limits Using Real-Time Model Predictive Control
- Chapter 15: Local Control of Distribution Networks
- Chapter 16: Electric Power Network Splitting Considering Frequency Dynamics and Transmission Overloading Constraints
- Chapter 17: High-Speed Transmission Line Protection Based on Empirical Orthogonal Functions
- Chapter 18: Implementation of a Real Phasor Based Vulnerability Assessment and Control Scheme: The Ecuadorian WAMPAC System
- Index
- End User License Agreement