
- English
- ePUB (mobile friendly)
- Available on iOS & Android
eBook - ePub
Cybersecurity of Industrial Systems
About this book
How to manage the cybersecurity of industrial systems is a crucial question. To implement relevant solutions, the industrial manager must have a clear understanding of IT systems, of communication networks and of control-command systems. They must also have some knowledge of the methods used by attackers, of the standards and regulations involved and of the available security solutions. Cybersecurity of Industrial Systems presents these different subjects in order to give an in-depth overview and to help the reader manage the cybersecurity of their installation. The book addresses these issues for both classic SCADA architecture systems and Industrial Internet of Things (IIoT) systems.
Frequently asked questions
Yes, you can cancel anytime from the Subscription tab in your account settings on the Perlego website. Your subscription will stay active until the end of your current billing period. Learn how to cancel your subscription.
No, books cannot be downloaded as external files, such as PDFs, for use outside of Perlego. However, you can download books within the Perlego app for offline reading on mobile or tablet. Learn more here.
Perlego offers two plans: Essential and Complete
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
We are an online textbook subscription service, where you can get access to an entire online library for less than the price of a single book per month. With over 1 million books across 1000+ topics, we’ve got you covered! Learn more here.
Look out for the read-aloud symbol on your next book to see if you can listen to it. The read-aloud tool reads text aloud for you, highlighting the text as it is being read. You can pause it, speed it up and slow it down. Learn more here.
Yes! You can use the Perlego app on both iOS or Android devices to read anytime, anywhere — even offline. Perfect for commutes or when you’re on the go.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app.
Yes, you can access Cybersecurity of Industrial Systems by Jean-Marie Flaus in PDF and/or ePUB format, as well as other popular books in Technology & Engineering & Electrical Engineering & Telecommunications. We have over one million books available in our catalogue for you to explore.
Information
Edition
11
Components of an Industrial Control System
1.1. Introduction
1.1.1. Definition: automated and cyber-physical systems
The systems we are interested in are automated systems in the broad sense: they consist of a computerized control system, sensors to access physical quantities and actuators to act on the controlled system.
Such systems are found in industrial production facilities, where control is carried out by a programmable logic controller (PLC) or by a set of connected objects. There are also such systems for the automation of buildings, water and electricity distribution networks, transport systems, etc. They have a computer part constituting an information system (IS) and a physical part. We are talking about a cyber-physical system (CPS).
1.1.2. Definition: Information System (IS)
An Information System (IS) is an organized set of resources (hardware, software, personnel, data, procedures, etc.) for acquiring, processing and storing information (in the form of data, text, images, sounds, etc.) within and between organizations.
Many ISs only process information, others affect the physical world. It is the latter that we are interested in this book.
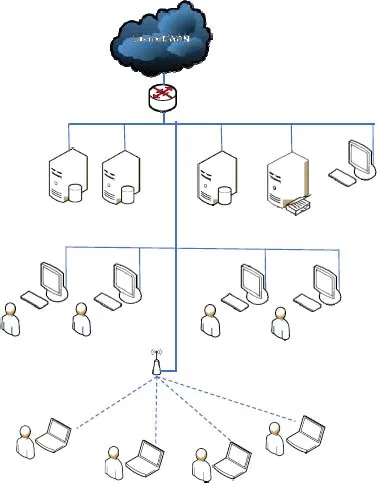
Figure 1.1. Information system. For a color version of this figure, see www.iste.co.uk/flaus/cybersecurity.zip
1.1.3. Definition: industrial IS or ICS
An industrial IS, or an industrial control system (ICS), is a system composed of an IS plus specific equipment for control and measurement.
The architecture of a traditional industrial IS is shown in Figure 1.2, which is called Supervisory Control And Data Acquisition (SCADA) or Distributed Control System (DCS).
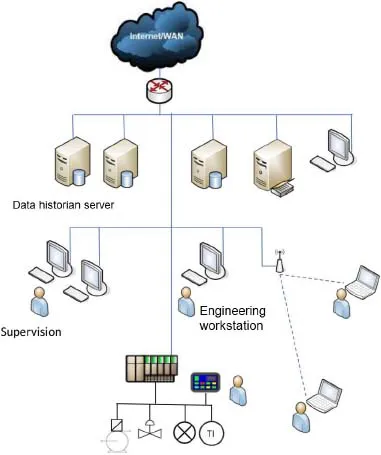
Figure 1.2. Industrial information system. For a color version of this figure, see www.iste.co.uk/flaus/cybersecurity.zip
The architecture of an industrial IS based on the Internet of Things (IoT) is shown in Figure 1.3. It is based on the Cloud and introduces new components and protocols described in the rest of the book.
In general, an ICS is composed of the same elements as a management IS with, in addition, specific equipment and specific software such as control command programs. These ensure real-time control and manage the archiving of data that characterize the evolution of the installation (history and alarm logs).
Henceforth, we will use the term ICS to refer to all the computer systems used to control a physical system.
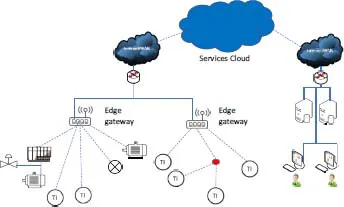
Figure 1.3. IIoT information system. For a color version of this figure, see www.iste.co.uk/flaus/cybersecurity.zip
1.1.4. Definition: IT and OT system
To distinguish ICSs from management ISs, the terms Information Technology (IT) and Operation Technology (OT) are often used.
An IT system is an IS as presented above. It is intended for the processing and storage of information. It is composed of computers, software, networks and human–machine interfaces (HMIs). An OT system is intended to interact with a physical system. It is composed of hardware and software to capture the evolution of a physical system via sensors, and to perform actions via actuators.
ICSs rely on varied information processing equipment, but integrate additional equipment to act on physical systems, and therefore belong to the OT world.
1.1.5. Definition: SCADA
A SCADA (Figure 1.4) is a system for controlling automation and data acquisition equipment. It makes it possible to centralize the control of an installation and to present an ergonomic HMI.
It includes workstations that generally run on Windows and are equipped with specialized software with a graphical interface that displays synoptics and trend curves. These workstations are connected via a network to equipment directly linked to the physical system: PLCs, input–output components, remote HMI, etc. It also includes servers, routers and other useful technical equipment. A SCADA is an ICS, but not all ICSs are SCADAs.
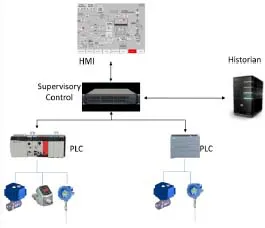
Figure 1.4. The minimal functions of a SCADA. For a color version of this figure, see www.iste.co.uk/flaus/cybersecurity.zip
1.1.6. Definition: Distributed Control Systems (DCS)
A DCS is a set of control systems connected in a network with a central unit to carry out supervision. The whole set is from the same manufacturer. Historically, this architecture was very different from the more heterogeneous SCADA systems, but with the evolution of technology, the differences have faded.
1.1.7. Definition: Industrial Internet of Things (IIOT)
The IoT refers to the extension of the Internet, that is, the global network for exchanging information with objects connected to the physical world. The Industrial Internet of Things (IIoT) is the use of the IoT in the industrial sector. These objects, more or less autonomous, will transform the industrial world. We sometimes talk about the plant of the future or Industry 4.0. The potential of this technology is enormous. The challenges posed by this interconnection are commensurate with the potential of this technology.
1.1.8. Different types of ICS
ICSs are used in many industrial sectors and critical infrastructures. A distinction is made between the manufacturing sector (e.g. the chemical industry or building management systems) and the distribution sector (e.g. of water or energy).
In the first case, the installation is geographically located. The manufacturing processes can be:
- – continuous: these processes operate continuously, often with transitions to produce different qualities of a product, the quantit...
Table of contents
- Cover
- Table of Contents
- Foreword
- Introduction
- 1 Components of an Industrial Control System
- 2 Architecture and Communication in an Industrial Control System
- 3 IT Security
- 4 Threats and Attacks to ICS
- 5 Vulnerabilities of ICS
- 6 Standards, Guides and Regulatory Aspects
- 7 The Approach Proposed by Standard 62443
- 8 Functional Safety and Cybersecurity
- 9 Risk Assessment Methods
- 10 Methods and Tools to Secure ICS
- 11 Implementation of the ICS Cybersecurity Management Approach
- Appendix 1: Cryptography Basics
- Appendix 2: Blockchain and IIoT Security
- Appendix 3: NIST SP 800-82 Security Measures
- Appendix 4: ANSSI Security Measures
- Appendix 5: Additions to the IEC 62433 Standard
- Appendix 6: Some Tools
- List of acronyms and abbreviations
- References
- Index
- End User License Agreement