
Fraud Data Analytics Methodology
The Fraud Scenario Approach to Uncovering Fraud in Core Business Systems
- English
- ePUB (mobile friendly)
- Available on iOS & Android
Fraud Data Analytics Methodology
The Fraud Scenario Approach to Uncovering Fraud in Core Business Systems
About this book
Uncover hidden fraud and red flags using efficient data analytics
Fraud Data Analytics Methodology addresses the need for clear, reliable fraud detection with a solid framework for a robust data analytic plan. By combining fraud risk assessment and fraud data analytics, you'll be able to better identify and respond to the risk of fraud in your audits. Proven techniques help you identify signs of fraud hidden deep within company databases, and strategic guidance demonstrates how to build data interrogation search routines into your fraud risk assessment to locate red flags and fraudulent transactions. These methodologies require no advanced software skills, and are easily implemented and integrated into any existing audit program. Professional standards now require all audits to include data analytics, and this informative guide shows you how to leverage this critical tool for recognizing fraud in today's core business systems.
Fraud cannot be detected through audit unless the sample contains a fraudulent transaction. This book explores methodologies that allow you to locate transactions that should undergo audit testing.
- Locate hidden signs of fraud
- Build a holistic fraud data analytic plan
- Identify red flags that lead to fraudulent transactions
- Build efficient data interrogation into your audit plan
Incorporating data analytics into your audit program is not about reinventing the wheel. A good auditor must make use of every tool available, and recent advances in analytics have made it accessible to everyone, at any level of IT proficiency. When the old methods are no longer sufficient, new tools are often the boost that brings exceptional results. Fraud Data Analytics Methodology gets you up to speed, with a brand new tool box for fraud detection.
Frequently asked questions
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app.
Information
Chapter 1
Introduction to Fraud Data Analytics
What Is Fraud Data Analytics?
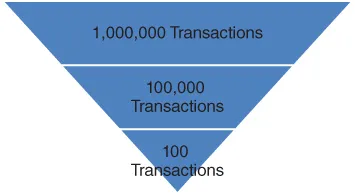
What Is Fraud Auditing?
- Fraud risk identification. The process starts with identifying the inherent fraud schemes and customizing the inherent fraud scheme into a fraud scenario. Fraud scenarios in this context will be discussed in Chapter 2.
- Fraud risk assessment. In the traditional audit methodology the fraud risk assessment is the process of linking of internal controls to the fraud scenario to determine the extent of residual risk. In this book, fraud data analytics is used as an assessment tool through the use of data‐mining search routines to determine if transactions exist that are consistent with the fraud scenario data profile.
- Fraud audit procedure. The audit procedure focuses on gathering audit evidence that is outside the point of the fraud opportunity (person committing the fraud scenario). The general standard is to gather evidence that is externally created and externally stored from the fraud opportunity point.
- Fraud conclusion. The conclusion is an either/or outcome, either requiring the transaction to be referred to investigation or leading to the determination that no relevant red flags exist. Chapters 6 through 15 contain relevant discussion of fraud data analytics in the core business systems.
What Is a Fraud Scenario?
- The common fraud scenario. Every business sy...
Table of contents
- Cover
- Title Page
- Copyright
- Dedication
- Table of Contents
- Preface
- Acknowledgments
- Chapter 1: Introduction to Fraud Data Analytics
- Chapter 2: Fraud Scenario Identification
- Chapter 3: Data Analytics Strategies for Fraud Detection
- Chapter 4: How to Build a Fraud Data Analytics Plan
- Chapter 5: Data Analytics in the Fraud Audit
- Chapter 6: Fraud Data Analytics for Shell Companies
- Chapter 7: Fraud Data Analytics for Fraudulent Disbursements
- Chapter 8: Fraud Data Analytics for Payroll Fraud
- Chapter 9: Fraud Data Analytics for Company Credit Cards
- Chapter 10: Fraud Data Analytics for Theft of Revenue and Cash Receipts
- Chapter 11: Fraud Data Analytics for Corruption Occurring in the Procurement Process
- Chapter 12: Corruption Committed by the Company
- Chapter 13: Fraud Data Analytics for Financial Statements
- Chapter 14: Fraud Data Analytics for Revenue and Accounts Receivable Misstatement
- Chapter 15: Fraud Data Analytics for Journal Entries
- Appendix A: Data Mining Audit Program for Shell Companies
- About the Author
- Index
- End User License Agreement