
eBook - ePub
Industrial Security
Managing Security in the 21st Century
- English
- ePUB (mobile friendly)
- Available on iOS & Android
eBook - ePub
About this book
A comprehensive and practical guide to security organization and planning in industrial plants
- Features Basic definitions related to plant security
- Features Countermeasures and response methods
- Features Facilities and equipment, and security organization
- Topics covered are applicable to multiple types of industrial plants
- Illustrates practical techniques for assessing and evaluating financial and corporate risks
Frequently asked questions
Yes, you can cancel anytime from the Subscription tab in your account settings on the Perlego website. Your subscription will stay active until the end of your current billing period. Learn how to cancel your subscription.
No, books cannot be downloaded as external files, such as PDFs, for use outside of Perlego. However, you can download books within the Perlego app for offline reading on mobile or tablet. Learn more here.
Perlego offers two plans: Essential and Complete
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
We are an online textbook subscription service, where you can get access to an entire online library for less than the price of a single book per month. With over 1 million books across 1000+ topics, we’ve got you covered! Learn more here.
Look out for the read-aloud symbol on your next book to see if you can listen to it. The read-aloud tool reads text aloud for you, highlighting the text as it is being read. You can pause it, speed it up and slow it down. Learn more here.
Yes! You can use the Perlego app on both iOS or Android devices to read anytime, anywhere — even offline. Perfect for commutes or when you’re on the go.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app.
Yes, you can access Industrial Security by David L. Russell,Pieter C. Arlow in PDF and/or ePUB format, as well as other popular books in Política y relaciones internacionales & Terrorismo. We have over one million books available in our catalogue for you to explore.
Information
Chapter 1
Introduction to Security Risk Assessment and Management
Introduction
This course was developed out of a training outline and the course Col. Arlow and I taught together in Manama, Bahrain. Pieter’s background is South African Defense Force, and he was responsible for the security of the World Cup in 2011. Dave’s background is civilian, industrial chemical, and environmental consulting. Together, we believe that this book will provide a different and practical approach that combines security theory with practice. We hope that it is not just another book that is put on the shelf and used occasionally, but read and considered, and one where our suggestions are put into place.
Security is not just one group’s business; it is everybody’s business. The combination of security, safety, and environmental protection are critical to the operation of a modern-day chemical or industrial plant. Despite the heightened focus on security by the US Department of Homeland Security and Transportation Security Administration, in many instances, it amounts to little more than a theater of the absurd because the United States is only marginally more secure and it is more a chance of luck than of their expensive, large, and restrictive efforts to increase travel security in particular and homeland security in general. Paperwork does little to provide security.
Business Definition
The business definition of security is quite straight forward. Webster’s Dictionary provides us with the basis for security: “freedom danger, risk of loss, and trustworthy and dependable.” That is a very good start. The definition of security crosses a number of lines in the modern industrial plant and has many different definitions. Plant security can be anything from the guard force who keeps out the unwanted intruders to the executive protection service and to the corporate watchdog that looks after the financial and corporate affairs of the plant or the corporation to make sure that there is no theft or leaking of secrets at the highest level of the company.
With the advent of the Internet and the digital age, the job of security has been made, if anything, tougher because of the ease of communications and the proliferation of digital devices and the Internet. The communication is much easier, but then so is the ability to penetrate networks and obtain information or compromise security systems in a variety of ways. One has to look no further than the Stuxnet virus and how it delayed the development of the Iranian atomic program by attacking the centrifuges needed to refine the uranium. The success of the virus/worm delayed the development by up to 2 years.
Security Versus Risk
In order to get a better working definition of security, we should also have a working definition of risk. Risk is the chance of loss or injury. In a situation that includes favorable and unfavorable events, risk is the probability of an unfavorable event or outcome. We measure risk by examining the certainty that a particular bad outcome or outcomes will occur.
Risk comes in many forms. There is financial risk, enterprise risk, risk of self-organized criticality (failure),1,2 risk of injury, internal risk (theft, fire, economic loss, etc.), industrial/jurisdictional risk, operational risk, and several other types of often unforeseen and uncontrollable events that create damage. Within the various operations of a corporation, many of these have specific departments to address those risks. For example, safety, health, and environmental departments address specific risks for worker safety and environmental contamination; the IT security department manages risk for intellectual- and computer-related data. We are more concerned with the risks associated with external events such as terrorism, earthquakes, tornadoes, fire, etc. These are external risks. Internal risks might include sabotage and plant accidents resulting in fire, spills, explosion, etc.3
Within the scope of plant security, one is primarily concerned with events that are external to or imposed upon the plant, natural occurrences, and man-made occurrences, some of which are preventable and others not. Our working definition will include such elements as terrorism, external attacks, naturally occurring events such as tornadoes and hurricanes, and some limited scenarios for sabotage. Events such as spills, fire, and accidents may be equally unpredictable, but they are often addressable by proper design of facilities, installation of engineering controls, and management of personnel through procedures and training. Logically, we must also look into some of the process control and operational functions as a modern plant uses a variety of computer and wired and wireless control systems that are often open to sabotage or external influences.
Framework for Risk Management
The basic framework for risk management is a cost-associated function where the general sequence starts with identification of the assets at risk, evaluation of the likelihood of their occurrence, development of a cost and a probability associated with the occurrence of an attack or an event, and estimation of the costs to reduce the risk to manageable levels. This is a cyclic process, illustrated by Figures 1.1 and 1.2.
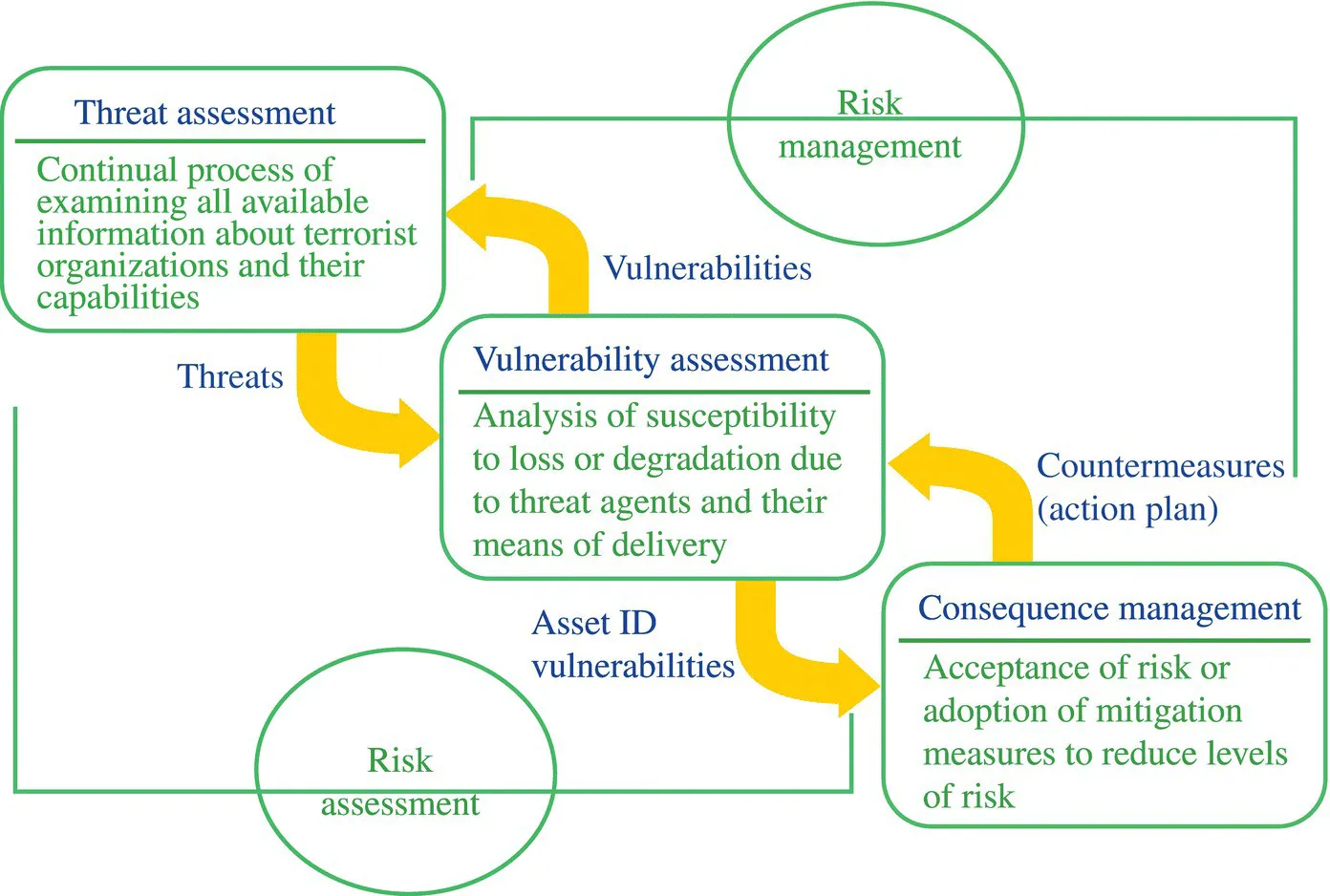
Figure 1.1 Outline of risk management actions.
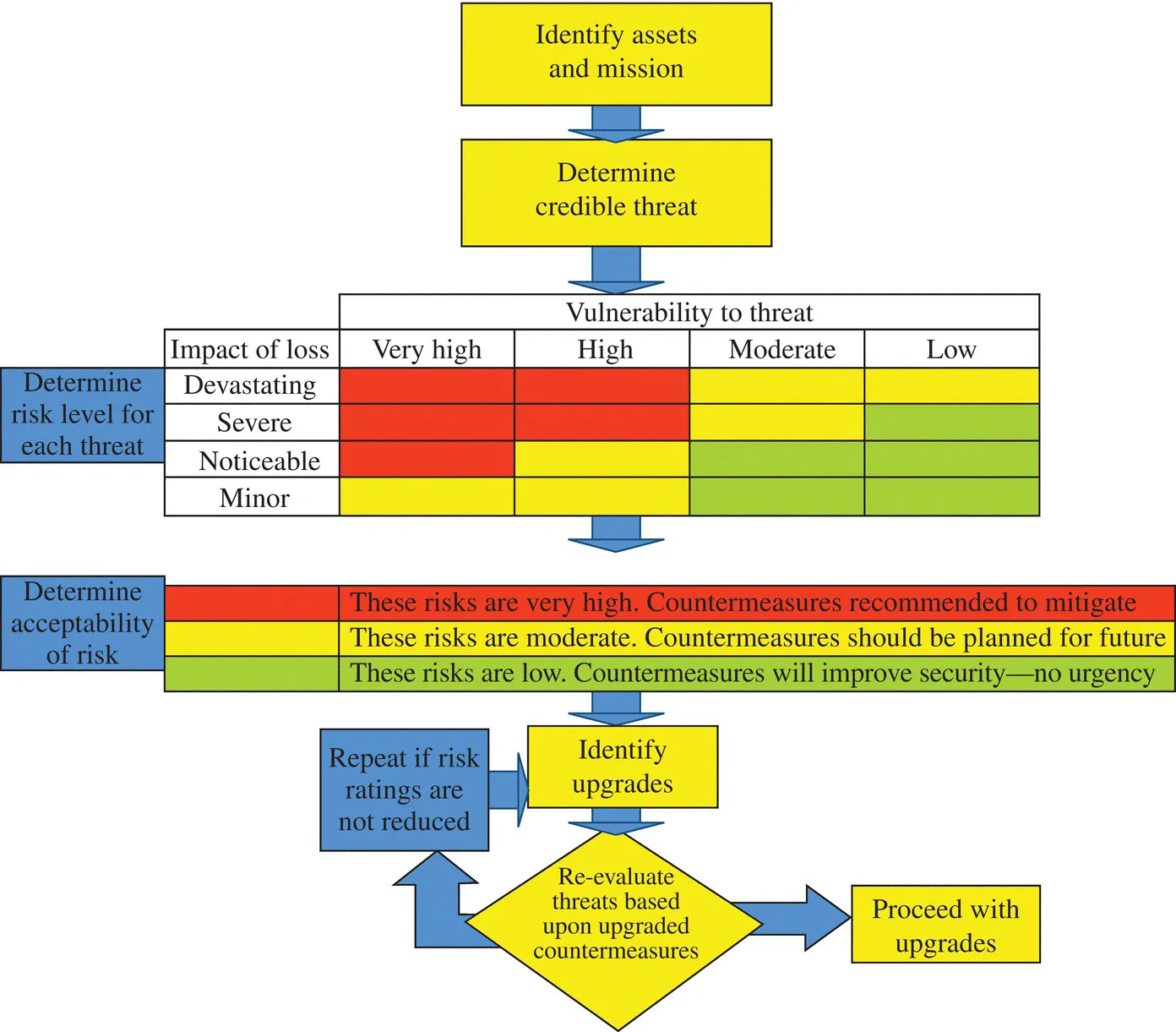
Figure 1.2 A second view of the risk analysis process. The risk analysis matrix is usually in color. Red indicates high risk, yellow indicates moderate risk, and green indicates lower levels of risk, but we have chosen to use stripes, dots, and white spaces to highlight the risk levels, respectively.
We measure and estimate the cost of a particular event occurring so that we can provide a financial plan for the plant or facility. We develop scenarios and the cost of those occurrences. For example, if we assume an attack by a hostile force, we try to estimate the damage and costs associated with that attack. We may create several scenarios and the associated costs. Things like standoff weapons such as a grenade launcher, a rocket, or a bazooka might have a damage level (cost) of C1 for the first scenario, C2 for the second scenario, etc. C1 might be for a mortar. C2 might be for a car bomb. The objective is to make these scenarios as realistic as possible when one views the likelihood of the attack.4
An attack can be any unplanned event and is subject to wide interpretation. Natural meteorological events can be an attack. So can an intruder into the plant. Terrorism is an attack, but then so is a civil unrest. Sabotage is a type of attack, but it is special and separate because it is imposed internally rather than from outside. However, a good risk management plan may want to consider sabotage as an element of a response plan.
Once we have a range of costs and scenarios, we can begin to determine the risk based on the probability of the events. This is often the most difficult and controversial part of the exercise because different assumptions on the likelihood of the event can produce dramatically different outcomes and costs. This is also complicated by the prospect of expenditures for increasing security and estimates as to how much specific improvements will reduce risk.
Just because a pl...
Table of contents
- Cover
- Title page
- Table of Contents
- Chapter 1: Introduction to Security Risk Assessment and Management
- Chapter 2: Risk Assessment Basics
- Chapter 3: Assessing Types of Attacks and Threats with Data Sources
- Chapter 4: Evaluating a Company’s Protective Systems
- Chapter 5: Port Security
- Chapter 6: Basics of Cyber security
- Chapter 7: Scenario Planning and Analyses
- Chapter 8: Security System Design and Implementation: Practical Notes
- Appendix I: Physical Security Checklist
- Appendix II
- Index
- End User License Agreement