Practical Mobile Forensics
Forensically investigate and analyze iOS, Android, and Windows 10 devices, 4th Edition
Rohit Tamma, Oleg Skulkin, Heather Mahalik, Satish Bommisetty
- 400 Seiten
- English
- ePUB (handyfreundlich)
- Über iOS und Android verfügbar
Practical Mobile Forensics
Forensically investigate and analyze iOS, Android, and Windows 10 devices, 4th Edition
Rohit Tamma, Oleg Skulkin, Heather Mahalik, Satish Bommisetty
Über dieses Buch
Become well-versed with forensics for the Android, iOS, and Windows 10 mobile platforms by learning essential techniques and exploring real-life scenarios
Key Features
- Apply advanced forensic techniques to recover deleted data from mobile devices
- Retrieve and analyze data stored not only on mobile devices but also on the cloud and other connected mediums
- Use the power of mobile forensics on popular mobile platforms by exploring different tips, tricks, and techniques
Book Description
Mobile phone forensics is the science of retrieving data from a mobile phone under forensically sound conditions. This updated fourth edition of Practical Mobile Forensics delves into the concepts of mobile forensics and its importance in today's world.
The book focuses on teaching you the latest forensic techniques to investigate mobile devices across various mobile platforms. You will learn forensic techniques for multiple OS versions, including iOS 11 to iOS 13, Android 8 to Android 10, and Windows 10. The book then takes you through the latest open source and commercial mobile forensic tools, enabling you to analyze and retrieve data effectively. From inspecting the device and retrieving data from the cloud, through to successfully documenting reports of your investigations, you'll explore new techniques while building on your practical knowledge. Toward the end, you will understand the reverse engineering of applications and ways to identify malware. Finally, the book guides you through parsing popular third-party applications, including Facebook and WhatsApp.
By the end of this book, you will be proficient in various mobile forensic techniques to analyze and extract data from mobile devices with the help of open source solutions.
What you will learn
- Discover new data extraction, data recovery, and reverse engineering techniques in mobile forensics
- Understand iOS, Windows, and Android security mechanisms
- Identify sensitive files on every mobile platform
- Extract data from iOS, Android, and Windows platforms
- Understand malware analysis, reverse engineering, and data analysis of mobile devices
- Explore various data recovery techniques on all three mobile platforms
Who this book is for
This book is for forensic examiners with basic experience in mobile forensics or open source solutions for mobile forensics. Computer security professionals, researchers or anyone looking to gain a deeper understanding of mobile internals will also find this book useful. Some understanding of digital forensic practices will be helpful to grasp the concepts covered in the book more effectively.
Häufig gestellte Fragen
Information
Section 1: iOS Forensics
- Chapter 2, Understanding the Internals of iOS Devices
- Chapter 3, Data Acquisition from iOS Devices
- Chapter 4, Data Acquisition from iOS Backups
- Chapter 5, iOS Data Analysis and Recovery
- Chapter 6, iOS Forensic Tools
Understanding the Internals of iOS Devices
- iPhone models and hardware
- iPad models and hardware
- The Hierarchical File System (HFS) Plus and Apple File System (APFS) filesystems
- The iPhone OS
iPhone models and hardware
Identifying the correct hardware model
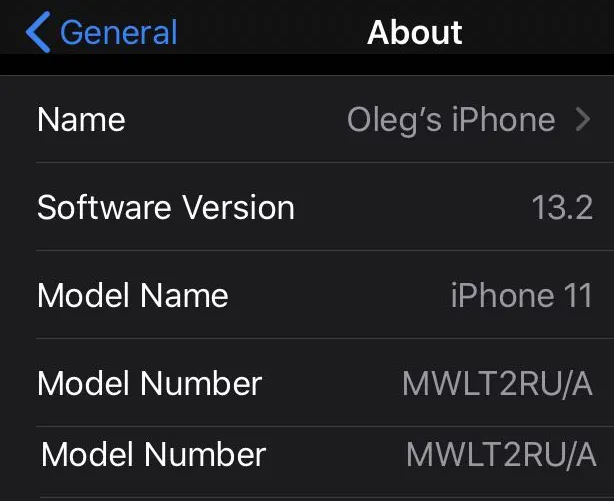
- Download the latest binaries from the following link: https://dev.azure.com/libimobiledevice-win32/imobiledevice-net/_build/results?buildId=419 (click on Artifacts | Binaries to start downloading).
- Unzip the archive with x86 or x64 binaries, depending on your workstation's version.
- Open Command Prompt and change the directory to the one with binaries (use the cd command for this).
- Connect the iPhone to your workstation using a Universal Serial Bus (USB) cable (for the latest iOS versions, the passcode is also required), and run the ideviceinfo command with the -s option, as shown in the following code:
$ ideviceinfo -s