
Blockchain for Distributed Systems Security
Sachin Shetty, Charles A. Kamhoua, Laurent L. Njilla, Sachin S. Shetty, Charles A. Kamhoua, Laurent L. Njilla
- English
- ePUB (handyfreundlich)
- Über iOS und Android verfügbar
Blockchain for Distributed Systems Security
Sachin Shetty, Charles A. Kamhoua, Laurent L. Njilla, Sachin S. Shetty, Charles A. Kamhoua, Laurent L. Njilla
Über dieses Buch
AN ESSENTIAL GUIDE TO USING BLOCKCHAIN TO PROVIDE FLEXIBILITY, COST-SAVINGS, AND SECURITY TO DATA MANAGEMENT, DATA ANALYSIS, AND INFORMATION SHARING
Blockchain for Distributed Systems Security contains a description of the properties that underpin the formal foundations of Blockchain technologies and explores the practical issues for deployment in cloud and Internet of Things (IoT) platforms. The authors—noted experts in the field—present security and privacy issues that must be addressed for Blockchain technologies to be adopted for civilian and military domains. The book covers a range of topics including data provenance in cloud storage, secure IoT models, auditing architecture, and empirical validation of permissioned Blockchain platforms.
The book's security and privacy analysis helps with an understanding of the basics of Blockchain and it explores the quantifying impact of the new attack surfaces introduced by Blockchain technologies and platforms. In addition, the book contains relevant and current updates on the topic. This important resource:
- Provides an overview of Blockchain-based secure data management and storage for cloud and IoT
- Covers cutting-edge research findings on topics including invariant-based supply chain protection, information sharing framework, and trust worthy information federation
- Addresses security and privacy concerns in Blockchain in key areas, such as preventing digital currency miners from launching attacks against mining pools, empirical analysis of the attack surface of Blockchain, and more
Written for researchers and experts in computer science and engineering, Blockchain for Distributed Systems Security contains the most recent information and academic research to provide an understanding of the application of Blockchain technology.
Häufig gestellte Fragen
Information
Part I
Introduction to Blockchain
1
Introduction
1.1 Blockchain Overview
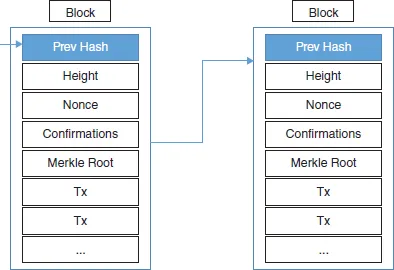
1.1.1 Blockchain Building Blocks
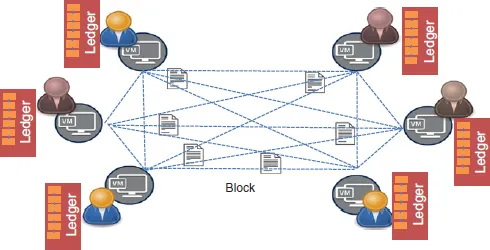
- Decentralized Network—The function of the decentralized network is to ensure the propagation of transaction messages among the nodes responsible for maintaining the distributed ledger. The network protocol allows the transaction message to be broadcast from any node to all nodes in the decentralized network. However, the network is not a pure broadcast medium and allows nodes to propagate messages that represent valid transactions. The network can be part of a private or public blockchain that has ramifications on network performance and security. Irrespective of whether the blockchain is public or private, the decentralized network is based on a p2p architecture. The nodes can join and leave freely. There is no centralized arbitrator. The network has built-in redundancy and robustness to mitigate node and link failures.
- Distributed Consensus—Blockchain uses consensus protocols over a decentralized p2p network for verification of transactions prior to adding blocks to the public ledger. The consensus protocol receives messages from the p2p network and inserts transactions in the distributed ledger. The consensus protocol is responsible for mining blocks and reaching consensus on their integration in the blockchain. The consensus protocol chooses the set of transactions that is accepted after passing a verification process. The verification process is determined by users and does not require a centralized administrator. The consensus protocols ensure that the newly added transactions are not at odds with the confirmed transactions in ...