Microsoft Windows Security Essentials
Darril Gibson
- English
- ePUB (adapté aux mobiles)
- Disponible sur iOS et Android
Microsoft Windows Security Essentials
Darril Gibson
À propos de ce livre
Windows security concepts and technologies for IT beginners
IT security can be a complex topic, especially for those new to the field of IT. This full-color book, with a focus on the Microsoft Technology Associate (MTA) program, offers a clear and easy-to-understand approach to Windows security risks and attacks for newcomers to the world of IT. By paring down to just the essentials, beginners gain a solid foundation of security concepts upon which more advanced topics and technologies can be built.
This straightforward guide begins each chapter by laying out a list of topics to be discussed, followed by a concise discussion of the core networking skills you need to have to gain a strong handle on the subject matter. Chapters conclude with review questions and suggested labs so you can measure your level of understanding of the chapter's content.
- Serves as an ideal resource for gaining a solid understanding of fundamental security concepts and skills
- Offers a straightforward and direct approach to security basics and covers anti-malware software products, firewalls, network topologies and devices, network ports, and more
- Reviews all the topics you need to know for taking the MTA 98-367 exam
- Provides an overview of security components, looks at securing access with permissions, addresses audit policies and network auditing, and examines protecting clients and servers
If you're new to IT and interested in entering the IT workforce, then Microsoft Windows Security Essentials is essential reading.
Foire aux questions
Informations
Chapter 1
Understanding Core Security Principles
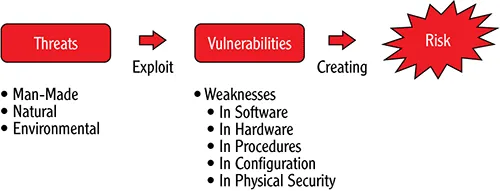
- Understanding risk
- Exploring the security triad
- Implementing a defense-in-depth security strategy
- Enforcing the principle of least privilege
- Hardening a server
Understanding Risk