SQL Injection Strategies
Practical techniques to secure old vulnerabilities against modern attacks
Ettore Galluccio, Edoardo Caselli, Gabriele Lombari
- 210 pages
- English
- ePUB (adapté aux mobiles)
- Disponible sur iOS et Android
SQL Injection Strategies
Practical techniques to secure old vulnerabilities against modern attacks
Ettore Galluccio, Edoardo Caselli, Gabriele Lombari
À propos de ce livre
Learn to exploit vulnerable database applications using SQL injection tools and techniques, while understanding how to effectively prevent attacks
Key Features
- Understand SQL injection and its effects on websites and other systems
- Get hands-on with SQL injection using both manual and automated tools
- Explore practical tips for various attack and defense strategies relating to SQL injection
Book Description
SQL injection (SQLi) is probably the most infamous attack that can be unleashed against applications on the internet. SQL Injection Strategies is an end-to-end guide for beginners looking to learn how to perform SQL injection and test the security of web applications, websites, or databases, using both manual and automated techniques. The book serves as both a theoretical and practical guide to take you through the important aspects of SQL injection, both from an attack and a defense perspective.
You'll start with a thorough introduction to SQL injection and its impact on websites and systems. Later, the book features steps to configure a virtual environment, so you can try SQL injection techniques safely on your own computer. These tests can be performed not only on web applications but also on web services and mobile applications that can be used for managing IoT environments. Tools such as sqlmap and others are then covered, helping you understand how to use them effectively to perform SQL injection attacks.
By the end of this book, you will be well-versed with SQL injection, from both the attack and defense perspective.
What you will learn
- Focus on how to defend against SQL injection attacks
- Understand web application security
- Get up and running with a variety of SQL injection concepts
- Become well-versed with different SQL injection scenarios
- Discover SQL injection manual attack techniques
- Delve into SQL injection automated techniques
Who this book is for
This book is ideal for penetration testers, ethical hackers, or anyone who wants to learn about SQL injection and the various attack and defense strategies against this web security vulnerability. No prior knowledge of SQL injection is needed to get started with this book.
Foire aux questions
Informations
Section 1: (No)SQL Injection in Theory
- Chapter 1, Structured Query Language for SQL Injection
- Chapter 2, Manipulating SQL – Exploiting SQL Injection
Chapter 1: Structured Query Language for SQL Injection
- An overview of SQL – a relational query language: A preliminary overview of SQL, our main language of reference that SQL injection is traditionally based on, and the relational model versus other DBMS models.
- Syntax and logic of SQL: An explanation of the main concepts and constructs behind SQL, some of which could be exploited by malicious attackers.
- Security implications of SQL: A brief introduction to the concept of security in SQL and its use in applications.
- Weakness in the use of SQL: An explanation of the main pitfalls an application relying on SQL can have, highlighting some general advice in secure development.
Technical requirements
- https://dev.mysql.com/doc/refman/8.0/en/
- https://docs.oracle.com/en/database/oracle/oracle-database/index.html
- https://docs.microsoft.com/en-us/sql/sql-server/?view=sql-server-ver15
An overview of SQL – a relational query language
Database management systems and relational databases
Relational databases
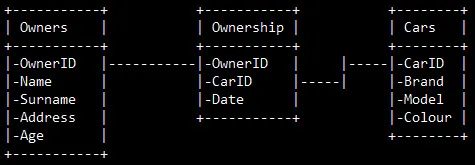
Non-relational databases
- Network databases model the data as connected nodes in a network:

- Graph-based databases highlight the connections among data using a graph-like navigable structure:
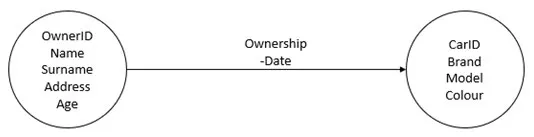
- Object-oriented databases model data as objects, in a similar fashion as in programming languages such as Java:

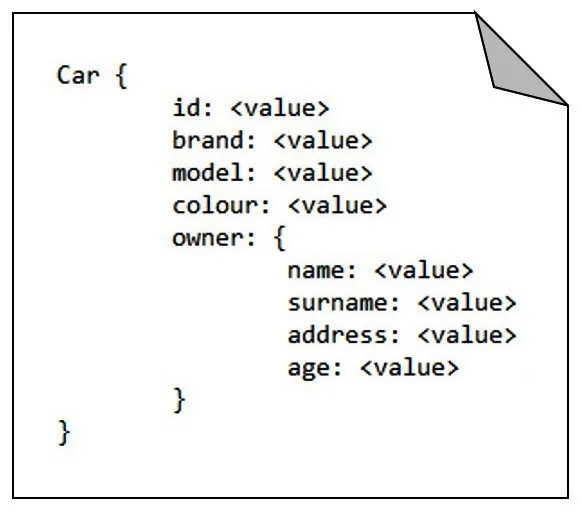
- Document-based databases describe data within documents containing key-value pairs, specify the way in which data is memorized and managed, and provide a flexible approach that does not rely on a defined schema. Document-based models can usually include embedded objects as collections within a single key, as shown in the following image: