Alice and Bob Learn Application Security
Tanya Janca
- English
- ePUB (adapté aux mobiles)
- Disponible sur iOS et Android
Alice and Bob Learn Application Security
Tanya Janca
À propos de ce livre
Learn application security from the very start, with this comprehensive and approachable guide!
Alice and Bob Learn Application Security is an accessible and thorough resource for anyone seeking to incorporate, from the beginning of the System Development Life Cycle, best security practices in software development. This book covers all the basic subjects such as threat modeling and security testing, but also dives deep into more complex and advanced topics for securing modern software systems and architectures. Throughout, the book offers analogies, stories of the characters Alice and Bob, real-life examples, technical explanations and diagrams to ensure maximum clarity of the many abstract and complicated subjects.
Topics include:
- Secure requirements, design, coding, and deployment
- Security Testing (all forms)
- Common Pitfalls
- Application Security Programs
- Securing Modern Applications
- Software Developer Security Hygiene
Alice and Bob Learn Application Security is perfect for aspiring application security engineers and practicing software developers, as well as software project managers, penetration testers, and chief information security officers who seek to build or improve their application security programs.
Alice and Bob Learn Application Security illustrates all the included concepts with easy-to-understand examples and concrete practical applications, furthering the reader's ability to grasp and retain the foundational and advanced topics contained within.
Foire aux questions
Informations
Part I
What You Must Know to Write Code Safe Enough to Put on the Internet
In This Part
- Chapter 1: Security Fundamentals
- Chapter 2: Security Requirements
- Chapter 3: Secure Design
- Chapter 4: Secure Code
- Chapter 5: Common Pitfalls
CHAPTER 1
Security Fundamentals
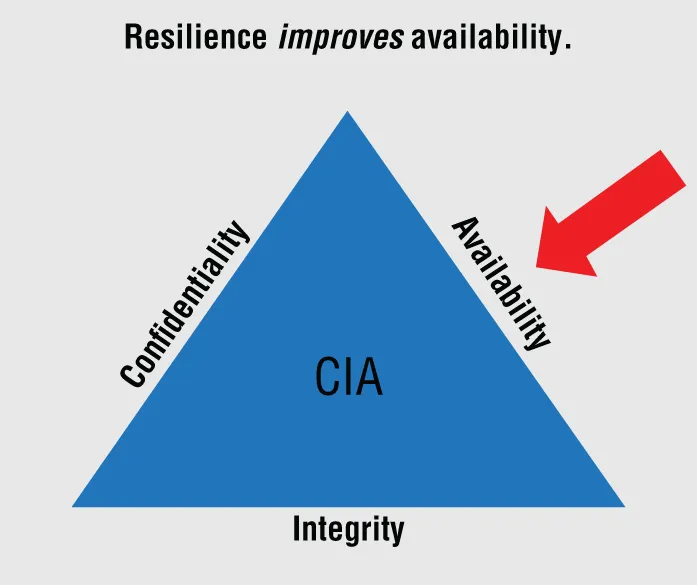
The Security Mandate: CIA
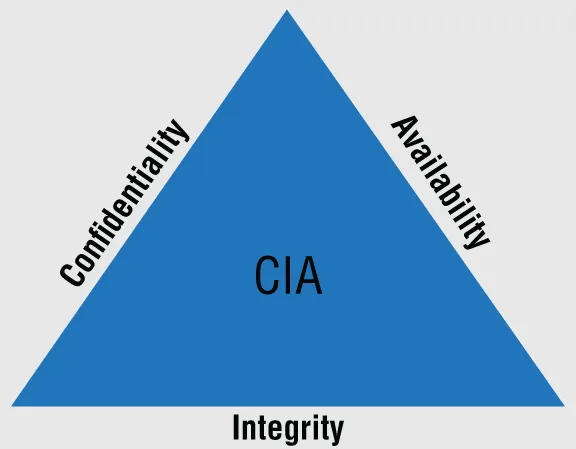
Confidentiality

Integrity
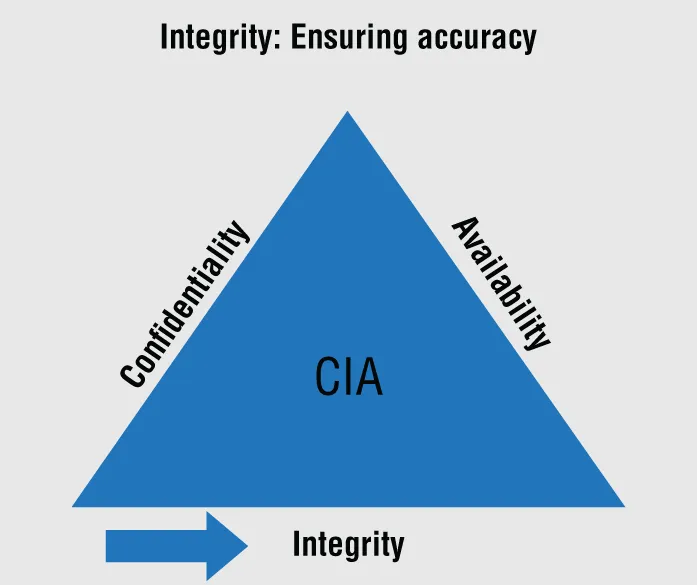
Availability