Hands-On Cybersecurity with Blockchain
Implement DDoS protection, PKI-based identity, 2FA, and DNS security using Blockchain
Rajneesh Gupta
- 236 pages
- English
- ePUB (adapté aux mobiles)
- Disponible sur iOS et Android
Hands-On Cybersecurity with Blockchain
Implement DDoS protection, PKI-based identity, 2FA, and DNS security using Blockchain
Rajneesh Gupta
À propos de ce livre
Develop blockchain application with step-by-step instructions, working example and helpful recommendationsAbout This Book• Understanding the blockchain technology from the cybersecurity perspective• Developing cyber security solutions with Ethereum blockchain technology• Understanding real-world deployment of blockchain based applicationsWho This Book Is ForThe book is targeted towards security professionals, or any stakeholder dealing with cybersecurity who wants to understand the next-level of securing infrastructure using Blockchain. Basic understanding of Blockchain can be an added advantage.What You Will Learn• Understand the cyberthreat landscape• Learn about Ethereum and Hyperledger Blockchain• Program Blockchain solutions• Build Blockchain-based apps for 2FA, and DDoS protection• Develop Blockchain-based PKI solutions and apps for storing DNS entries• Challenges and the future of cybersecurity and BlockchainIn DetailBlockchain technology is being welcomed as one of the most revolutionary and impactful innovations of today. Blockchain technology was first identified in the world's most popular digital currency, Bitcoin, but has now changed the outlook of several organizations and empowered them to use it even for storage and transfer of value.This book will start by introducing you to the common cyberthreat landscape and common attacks such as malware, phishing, insider threats, and DDoS. The next set of chapters will help you to understand the workings of Blockchain technology, Ethereum and Hyperledger architecture and how they fit into the cybersecurity ecosystem. These chapters will also help you to write your first distributed application on Ethereum Blockchain and the Hyperledger Fabric framework. Later, you will learn about the security triad and its adaptation with Blockchain. The last set of chapters will take you through the core concepts of cybersecurity, such as DDoS protection, PKI-based identity, 2FA, and DNS security. You will learn how Blockchain plays a crucial role in transforming cybersecurity solutions.Toward the end of the book, you will also encounter some real-world deployment examples of Blockchain in security cases, and also understand the short-term challenges and future of cybersecurity with Blockchain.Style and approachThis book will follow a practical approach to help understand blockchain technology to transform cybersecurity solutions
Foire aux questions
Informations
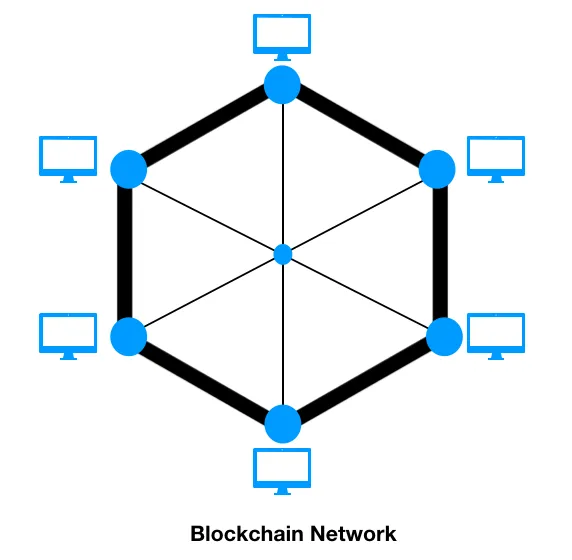
Introducing Blockchain and Ethereum
- What blockchain is
- Internet versus blockchain
- How blockchain works
- The building blocks of blockchain
- Ethereum blockchain
- Private versus public blockchains
- Business adaptation
What is blockchain?
- Detect who looks at a person's account and changes it
- Ensure that data concerning the person is not misused
A brief history
Fundamentals of the blockchain