Cybersecurity Essentials
Charles J. Brooks, Christopher Grow, Philip A. Craig, Donald Short
- English
- ePUB (adapté aux mobiles)
- Disponible sur iOS et Android
Cybersecurity Essentials
Charles J. Brooks, Christopher Grow, Philip A. Craig, Donald Short
À propos de ce livre
An accessible introduction to cybersecurity concepts and practices
Cybersecurity Essentials provides a comprehensive introduction to the field, with expert coverage of essential topics required for entry-level cybersecurity certifications. An effective defense consists of four distinct challenges: securing the infrastructure, securing devices, securing local networks, and securing the perimeter. Overcoming these challenges requires a detailed understanding of the concepts and practices within each realm. This book covers each challenge individually for greater depth of information, with real-world scenarios that show what vulnerabilities look like in everyday computing scenarios. Each part concludes with a summary of key concepts, review questions, and hands-on exercises, allowing you to test your understanding while exercising your new critical skills.
Cybersecurity jobs range from basic configuration to advanced systems analysis and defense assessment. This book provides the foundational information you need to understand the basics of the field, identify your place within it, and start down the security certification path.
- Learn security and surveillance fundamentals
- Secure and protect remote access and devices
- Understand network topologies, protocols, and strategies
- Identify threats and mount an effective defense
Cybersecurity Essentials gives you the building blocks for an entry level security certification and provides a foundation of cybersecurity knowledge
Foire aux questions
Informations
PART I
Securing the Infrastructure
| Chapter 1 | Infrastructure Security in the Real World |
| Chapter 2 | Understanding Access Control and Monitoring Systems |
| Chapter 3 | Understanding Video Surveillance Systems |
| Chapter 4 | Understanding Intrusion Detection and Reporting Systems |
| Chapter 5 | Infrastructure Security: Review Questions & Hands-On Exercises |
CHAPTER 1
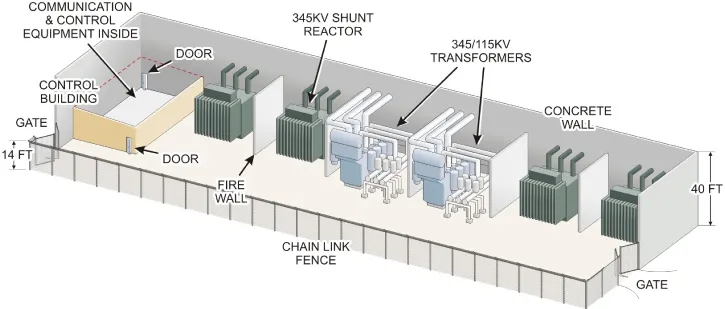
Infrastructure Security in the Real World
- Understand the relevance of infrastructure security
- Describe the functions, categories, subcategories, and reference structure of the NIST Cybersecurity Framework
- Apply the NIST Framework references to specific cybersecurity scenarios
Security Challenges
Infrastructure Security Scenario 1