
eBook - ePub
Nmap in the Enterprise
Your Guide to Network Scanning
Angela Orebaugh, Becky Pinkard
This is a test
Condividi libro
- 264 pagine
- English
- ePUB (disponibile sull'app)
- Disponibile su iOS e Android
eBook - ePub
Nmap in the Enterprise
Your Guide to Network Scanning
Angela Orebaugh, Becky Pinkard
Dettagli del libro
Anteprima del libro
Indice dei contenuti
Citazioni
Informazioni sul libro
Nmap, or Network Mapper, is a free, open source tool that is available under the GNU General Public License as published by the Free Software Foundation. It is most often used by network administrators and IT security professionals to scan corporate networks, looking for live hosts, specific services, or specific operating systems. Part of the beauty of Nmap is its ability to create IP packets from scratch and send them out utilizing unique methodologies to perform the above-mentioned types of scans and more. This book provides comprehensive coverage of all Nmap features, including detailed, real-world case studies.
- Understand Network Scanning: Master networking and protocol fundamentals, network scanning techniques, common network scanning tools, along with network scanning and policies.
- Get Inside Nmap: Use Nmap in the enterprise, secure Nmap, optimize Nmap, and master advanced Nmap scanning techniques.
- Install, Configure, and Optimize Nmap: Deploy Nmap on Windows, Linux, Mac OS X, and install from source.
- Take Control of Nmap with the Zenmap GUI: Run Zenmap, manage Zenmap scans, build commands with the Zenmap command wizard, manage Zenmap profiles, and manage Zenmap results.
- Run Nmap in the Enterprise: Start Nmap scanning, discover hosts, port scan, detecting operating systems, and detect service and application versions
- Raise those Fingerprints: Understand the mechanics of Nmap OS fingerprinting, Nmap OS fingerprint scan as an administrative tool, and detect and evade the OS fingerprint scan.
- "Tool" around with Nmap: Learn about Nmap add-on and helper tools: NDiff--Nmap diff, RNmap--Remote Nmap, Bilbo, Nmap-parser.
- Analyze Real-World Nmap Scans: Follow along with the authors to analyze real-world Nmap scans.
- Master Advanced Nmap Scanning Techniques: Torque Nmap for TCP scan flags customization, packet fragmentation, IP and MAC address spoofing, adding decoy scan source IP addresses, add random data to sent packets, manipulate time-to-live fields, and send packets with bogus TCP or UDP checksums.
Domande frequenti
Come faccio ad annullare l'abbonamento?
È semplicissimo: basta accedere alla sezione Account nelle Impostazioni e cliccare su "Annulla abbonamento". Dopo la cancellazione, l'abbonamento rimarrà attivo per il periodo rimanente già pagato. Per maggiori informazioni, clicca qui
È possibile scaricare libri? Se sì, come?
Al momento è possibile scaricare tramite l'app tutti i nostri libri ePub mobile-friendly. Anche la maggior parte dei nostri PDF è scaricabile e stiamo lavorando per rendere disponibile quanto prima il download di tutti gli altri file. Per maggiori informazioni, clicca qui
Che differenza c'è tra i piani?
Entrambi i piani ti danno accesso illimitato alla libreria e a tutte le funzionalità di Perlego. Le uniche differenze sono il prezzo e il periodo di abbonamento: con il piano annuale risparmierai circa il 30% rispetto a 12 rate con quello mensile.
Cos'è Perlego?
Perlego è un servizio di abbonamento a testi accademici, che ti permette di accedere a un'intera libreria online a un prezzo inferiore rispetto a quello che pagheresti per acquistare un singolo libro al mese. Con oltre 1 milione di testi suddivisi in più di 1.000 categorie, troverai sicuramente ciò che fa per te! Per maggiori informazioni, clicca qui.
Perlego supporta la sintesi vocale?
Cerca l'icona Sintesi vocale nel prossimo libro che leggerai per verificare se è possibile riprodurre l'audio. Questo strumento permette di leggere il testo a voce alta, evidenziandolo man mano che la lettura procede. Puoi aumentare o diminuire la velocità della sintesi vocale, oppure sospendere la riproduzione. Per maggiori informazioni, clicca qui.
Nmap in the Enterprise è disponibile online in formato PDF/ePub?
Sì, puoi accedere a Nmap in the Enterprise di Angela Orebaugh, Becky Pinkard in formato PDF e/o ePub, così come ad altri libri molto apprezzati nelle sezioni relative a Computer Science e Cyber Security. Scopri oltre 1 milione di libri disponibili nel nostro catalogo.
Informazioni
Argomento
Computer ScienceCategoria
Cyber SecurityChapter 1
Introducing Network Scanning
Introduction
About ten years ago I was working as a Network Administrator managing a medium size network. One of my first tasks in this position was to create a network asset database for all network devices. We already had a high-priced, although functionally deficient, network management tool that just wasn’t making the cut. Using the output from the management tool as a starting point I began painstakingly connecting to each network device, and documenting them to inventory the network. This also involved a lot of hours physically traversing buildings, basements, and wiring closets. Finally, it seemed that I had visited every nook and cranny and identified every router, bridge, switch, hub, and archaic telecommunications device retrofitted to the network. For security, I wrote a UNIX script to connect to the known devices and disable physical ports that weren’t being used and enable security features on the devices. This is when things started to get complicated. Suddenly the help desk phones started ringing and people were complaining of lost network connectivity. Alas, there were even more devices out there that we didn’t know about! Luckily the UNIX script was easily reversible. After hearing my woes that evening a “hacker” friend of mine pointed out a new tool for scanning networks that he read about in Phrack magazine. It was a bit controversial, but it was free and it looked like it could do the job. The next day became my first experience with Nmap, a network scanner, and since that day it has been making my life a whole lot easier.
What is Network Scanning?
Network scanning is the process of discovering active hosts on the network and information about the hosts, such as operating system, active ports, services, and applications. Network scanning is comprised of the following four basic techniques:
■ Network Mapping Sending messages to a host that will generate a response if the host is active
■ Port Scanning Sending messages to a specified port to determine if it is active
■ Service and Version Detection Sending specially crafted messages to active ports to generate responses that will indicate the type and version of service running
■ OS Detection Sending specially crafted messages to an active host to generate certain responses that will indicate the type of operating system running on the host
In addition to these basic techniques, advanced network scanners can perform other techniques such as masking the origin of the scanning, enabling timing features for stealthy scans, evading perimeter defenses such as firewalls, and providing reporting options.
The following is an example of the type of output you would expect from a network scan:
■ Host 192.168.100.1 is responding
■ Open ports include:
■ 135/tcp open msrpc
■ 139/tcp open netbios-ssn
■ 445/tcp open microsoft-ds
■ 3389/tcp open ms-term-serv
■ 8081/tcp open blackice-icecap
■ The operating system is Windows XP SP2
Networking and Protocol Fundamentals
This section provides background information on how networks and protocols work. However, there are many other excellent resources available, including the most popular and undoubtedly one of the best written, Richard Stevens’ “TCP/IP Illustrated, Vol. 1–3.”
Explaining Ethernet
Ethernet is the most popular protocol standard used to enable computers to communicate. A protocol is like speaking a particular language. Ethernet was built around the principle of a shared medium where all computers on the local network segment share the same cable. It is known as a broadcast protocol because it sends that data to all other computers on the same network segment. This information is divided up into manageable chunks called packets, and each packet has a header containing the addresses of both the destination and source computers. Even though this information is sent out to all computers on a segment, only the computer with the matching destination address responds. All of the other computers on the network still see the packet, but if they are not the intended receiver they disregard it.
Ethernet addresses are also known as Media Access Control (MAC) addresses and hardware addresses. Because many computers may share a single Ethernet segment, each one must have an individual identifier hard-coded onto the network interface card (NIC). A MAC address is a 48-bit number, which is also stated as a 12-digit hexadecimal number. This number is broken down into two halves; the first 24 bits identify the vendor of the Ethernet card, and the second 24 bits comprise a serial number assigned by the vendor.
The following steps allow you to view your NIC’s MAC address:
■ Windows 9x/ME Access Start | Run and type winipcfg.exe. The MAC address will be listed as the “Adapter Address.”
■ Windows NT, 2000, XP, and 2003 Access the command line and type ipconfig /all. The MAC address will be listed as the “Physical Address.”
■ Linux and Solaris Type ifconfig –a at the command line. The MAC address will be listed as the “HWaddr” on Linux and as “ether” on Solaris.
■ Macintosh OS X Type ifconfig –a at the Terminal application. The MAC address will be listed as the “Ether” label.
You can also view the MAC addresses of other computers that you have recently communicated with, by typing the command arp –a. The Address Resolution Protocol (ARP) is responsible for mapping IP addresses to MAC addresses.
MAC addresses are unique, and no two computers should have the same one. However, occasionally a manufacturing error may occur that causes more than one NIC to have the same MAC address. Thus, people may choose to change their MAC addresses intentionally, which can be done with a program (e.g., ifconfig) that allows you to fake your MAC address. Faking your MAC address (and other types of addresses) is also known as spoofing. Also, some adapters allow you to use a program to reconfigure the runtime MAC address. And lastly, with the right tools and skill you can physically re-burn the address into the NIC.
Understanding the Open Systems Interconnection Model
The International Standards Organization (ISO) developed the Open Systems Interconnection (OSI) model in the early 1980s to describe how network protocols and components work together. It divides network functions into seven layers, each layer representing a group of related specifications, functions, and activities (see Figure 1.1). Although complicated at first, the terminology is used extensively in networking, systems, and development communities. Understanding what these layers represent and how they work together will facilitate your comprehension of network scanning.
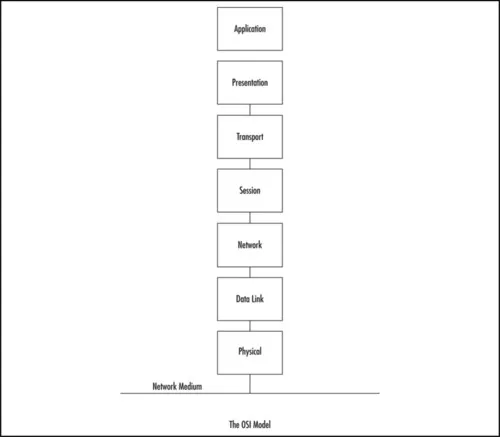
Figure 1.1 Seven Boxes Corresponding to the OSI Model