
- 264 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
About this book
Nmap, or Network Mapper, is a free, open source tool that is available under the GNU General Public License as published by the Free Software Foundation. It is most often used by network administrators and IT security professionals to scan corporate networks, looking for live hosts, specific services, or specific operating systems. Part of the beauty of Nmap is its ability to create IP packets from scratch and send them out utilizing unique methodologies to perform the above-mentioned types of scans and more. This book provides comprehensive coverage of all Nmap features, including detailed, real-world case studies.- Understand Network Scanning: Master networking and protocol fundamentals, network scanning techniques, common network scanning tools, along with network scanning and policies.- Get Inside Nmap: Use Nmap in the enterprise, secure Nmap, optimize Nmap, and master advanced Nmap scanning techniques.- Install, Configure, and Optimize Nmap: Deploy Nmap on Windows, Linux, Mac OS X, and install from source.- Take Control of Nmap with the Zenmap GUI: Run Zenmap, manage Zenmap scans, build commands with the Zenmap command wizard, manage Zenmap profiles, and manage Zenmap results.- Run Nmap in the Enterprise: Start Nmap scanning, discover hosts, port scan, detecting operating systems, and detect service and application versions- Raise those Fingerprints: Understand the mechanics of Nmap OS fingerprinting, Nmap OS fingerprint scan as an administrative tool, and detect and evade the OS fingerprint scan.- "Tool around with Nmap: Learn about Nmap add-on and helper tools: NDiff--Nmap diff, RNmap--Remote Nmap, Bilbo, Nmap-parser.- Analyze Real-World Nmap Scans: Follow along with the authors to analyze real-world Nmap scans.- Master Advanced Nmap Scanning Techniques: Torque Nmap for TCP scan flags customization, packet fragmentation, IP and MAC address spoofing, adding decoy scan source IP addresses, add random data to sent packets, manipulate time-to-live fields, and send packets with bogus TCP or UDP checksums.
Tools to learn more effectively

Saving Books

Keyword Search

Annotating Text

Listen to it instead
Information
Introducing Network Scanning
Introduction
What is Network Scanning?
Networking and Protocol Fundamentals
Explaining Ethernet
Understanding the Open Systems Interconnection Model
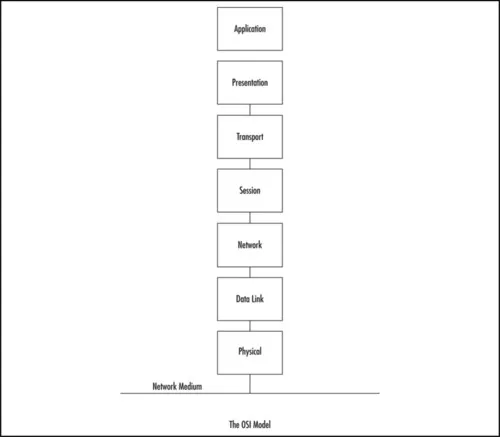
Table of contents
- Cover image
- Title page
- Table of Contents
- Copyright page
- Authors
- Technical Editor
- Chapter 1: Introducing Network Scanning
- Chapter 2: Introducing Nmap
- Chapter 3: Getting and Installing Nmap
- Chapter 4: Using Nmap
- Chapter 5: Using Zenmap
- Chapter 6: Nmap OS Fingerprinting
- Chapter 7: Tooling Around with Nmap
- Chapter 8: Nmap Scanning in the Real World
- Index
Frequently asked questions
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app