
eBook - ePub
Pervasive Computing
Next Generation Platforms for Intelligent Data Collection
- 548 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
eBook - ePub
Pervasive Computing
Next Generation Platforms for Intelligent Data Collection
About this book
Pervasive Computing: Next Generation Platforms for Intelligent Data Collection presents current advances and state-of-the-art work on methods, techniques, and algorithms designed to support pervasive collection of data under ubiquitous networks of devices able to intelligently collaborate towards common goals.
Using numerous illustrative examples and following both theoretical and practical results the authors discuss: a coherent and realistic image of today's architectures, techniques, protocols, components, orchestration, choreography, and developments related to pervasive computing components for intelligently collecting data, resource, and data management issues; the importance of data security and privacy in the era of big data; the benefits of pervasive computing and the development process for scientific and commercial applications and platforms to support them in this field.
Pervasive computing has developed technology that allows sensing, computing, and wireless communication to be embedded in everyday objects, from cell phones to running shoes, enabling a range of context-aware applications. Pervasive computing is supported by technology able to acquire and make use of the ubiquitous data sensed or produced by many sensors blended into our environment, designed to make available a wide range of new context-aware applications and systems. While such applications and systems are useful, the time has come to develop the next generation of pervasive computing systems. Future systems will be data oriented and need to support quality data, in terms of accuracy, latency and availability.
Pervasive Computing is intended as a platform for the dissemination of research efforts and presentation of advances in the pervasive computing area, and constitutes a flagship driver towards presenting and supporting advanced research in this area.
Indexing: The books of this series are submitted to EI-Compendex and SCOPUS
- Offers a coherent and realistic image of today's architectures, techniques, protocols, components, orchestration, choreography, and development related to pervasive computing
- Explains the state-of-the-art technological solutions necessary for the development of next-generation pervasive data systems, including: components for intelligently collecting data, resource and data management issues, fault tolerance, data security, monitoring and controlling big data, and applications for pervasive context-aware processing
- Presents the benefits of pervasive computing, and the development process of scientific and commercial applications and platforms to support them in this field
- Provides numerous illustrative examples and follows both theoretical and practical results to serve as a platform for the dissemination of research advances in the pervasive computing area
Tools to learn more effectively

Saving Books

Keyword Search

Annotating Text

Listen to it instead
Information
Part I
Automated Capture of Experiences with Easy Access
Chapter 1
On preserving privacy in cloud computing using ToR
A. Carniellia; M. Aiasha; M. Alazabb a Middlesex University, London, United Kingdom
b Macquarie University, Sydney, NSW, Australia
b Macquarie University, Sydney, NSW, Australia
Abstract
The Internet allows for an efficient, inexpensive collection of information without surfers’ consents. This includes surfers’ preferences, interests or even credit card information. Furthermore, it is well known that some oppressive governments filter the information that can digitally reach their countries. Also, there are evidences that certain governments spy on citizens and organizations through intercepting phone calls, activities on social media and blogs. For Internet browsing, several methods of privacy-preserving and anonymizers have been developed. An example of such a technology is The Onion Router (ToR) network, which has been proven to guarantee users’ anonymity and privacy while they are browsing the Internet. However, with the wide deployment of virtualization solutions and the tremendous migration to cloud-based services, many online services have moved onto the cloud. This situation complicates the issue of preserving a client’s privacy and anonymity and raises a “question mark” as to the efficiency of current anonymizers in this new environment. To the best of our knowledge, few studies have been conducted to analyze the compatibility between the ToR network and this new emerging infrastructure. This paper presents a qualitative analysis of the feasibility and efficiency of the ToR in cloud infrastructure and the possibility of integrating these technologies.
Keywords
Privacy; Cloud computing; ToR; Anonymity; Compatibility analysis
1 Introduction
Over the past two decades, threats to users’ privacy and identities have been of rising concern for Internet surfers. According to a report on anonymity, privacy, and security online (Dingledine et al., 2004), most Internet users would like to be anonymous online, at least occasionally, but many think it is not possible to be completely anonymous. The reasons behind such a belief vary from the increasing number of data leakage scandals, to the increasing demands by surfers to not be observed by specific people, organizations, or governments. The report in Dingledine et al. (2004) shows that 55% of Internet users have taken steps online to remove or mask their digital footprints and to avoid their activities being monitored and traced. Such steps range from clearing cookies to encrypting their email and using virtual networks that mask their Internet Protocol (IP) address. Such an attitude is ascribed to the fact that certain authoritative bodies and governments tend to misuse their power and spy on their own people. Several governments also filter specific websites through their border gateways in order to prevent flows of information from reaching their countries (as is the case for People’s Republic of China, North Korea, Bahrain, Iran, Vietnam (Rininsland, 2012), or, most recently, Venezuela (Bajak, 2014)).
Obviously, governments justify these activities of wire-tapping and interception as measures to ensure the “National Security.” Nevertheless, because of the invasive nature of such methods, Internet dwellers began to design and develop software in the forms of browsing anonymizers and communication obfuscation techniques to maintain their privacy and anonymity in the cyber world. Furthermore, considering the situation and events in some parts of the world such as “The Arab Spring” in the Middle East, hiding one’s identity while browsing the Internet might be crucial for personnel safety in these oppressive countries.
This situation highlights the huge demand placed on security mechanisms for protecting users’ privacy and anonymity on the Internet. An example of such a mechanism that has been made freely available to users is called The Onion Router (ToR) (Fang et al., 2000; Danezis et al., 2010; Michael et al., 2010). ToR has been designed to make it possible for users to surf the Internet anonymously, so that their activities and locations cannot be discovered by government agencies, corporations, or anyone else. Compared with other anonymizers such as Invisible Internet Project (I2P) (Wang et al., 2011), ToR is more popular; has more visibility in the academic and hacker communities; and benefits from formal studies of anonymity, resistance, and performance.
ToR and other anonymizers were initially conceived to run over the traditional Internet. However, the emergence and wide adoption of cloud-based services raises huge doubts about the efficiency of these anonymizers if used with these new technologies. Furthermore, customers of cloud computing have more concerns about the secrecy of their data, due to the fact that such data are being moved from the client’s local devices to third party online storage. The purpose of this research is to analyze the feasibility of running the ToR network on top of an infrastructure embracing both the traditional and the cloud computing models.
The rest of the paper is organized as follows. Section 2 gives an overview of cloud computing architecture and sheds light on issues such as privacy and anonymity in cloud computing. Section 3 describes the ToR network. Our experiments to deploy ToR with cloud-based services are described in Section 4.
2 Overview of cloud computing
Arguably, there is not a single, unified definition for cloud computing. Being a relatively new concept, different institutions and researchers define cloud computing in their own way; obviously, the key features of the cloud remain the same in each definition. Foster et al. (in Zhao et al., 2008) give a very deterministic and perhaps complicated delineation of this new technology. They define cloud computing as “A large-scale distributed computing paradigm that is driven by economies of scale, in which a pool of abstracted, virtualized, dynamically scalable, managed computing power, storage, platforms, and services are delivered on demand to external customers over the Internet.” In this research, when referring to cloud computing, we avail ourselves of the following simpler description, given by Danish et al. (in Wang et al., 2011): “Cloud Computing technology is a new concept of providing dramatically scalable and virtualized resources, bandwidth, software and hardware on demand to consumers. Consumers can typically requests Cloud services via a web browser or web service.”
The statement is self-explanatory. In simple terms, cloud computing is a revolutionary way of providing users (who may be a single person or even medium-size companies) with all the kinds of IT resources that they may need in order to fulfill their IT infrastructure requirements. In a cloud computing environment, there are two main players: the cloud provider (CP) (who owns a very huge data center and loans hardware and software resources) and the cloud consumer (who pays a fee to use such resources). Three main categories (models) exist for cloud deployment: public cloud, private cloud, and hybrid cloud as shown in Fig. 1.
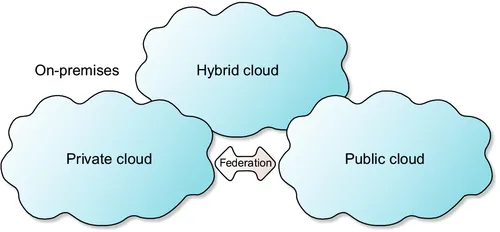
Fig. 1 Types of cloud computing. From Ribeiro, M., 2010. Thoughts on Information Technology. https://it...
Table of contents
- Cover image
- Title page
- Table of Contents
- Copyright
- Dedication
- Contributors
- About the Editors
- Foreword
- Preface
- Acknowledgments
- Part I: Automated Capture of Experiences with Easy Access
- Part II: Context-Aware/Sensitive Interactions and Applications
- Part III: Ubiquitous Services Independent of Devices/Platforms
- Part IV: Pervasive Computing and Applications
- Glossary
- Acronyms
- Index
Frequently asked questions
Yes, you can cancel anytime from the Subscription tab in your account settings on the Perlego website. Your subscription will stay active until the end of your current billing period. Learn how to cancel your subscription
No, books cannot be downloaded as external files, such as PDFs, for use outside of Perlego. However, you can download books within the Perlego app for offline reading on mobile or tablet. Learn how to download books offline
Perlego offers two plans: Essential and Complete
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
We are an online textbook subscription service, where you can get access to an entire online library for less than the price of a single book per month. With over 1 million books across 990+ topics, we’ve got you covered! Learn about our mission
Look out for the read-aloud symbol on your next book to see if you can listen to it. The read-aloud tool reads text aloud for you, highlighting the text as it is being read. You can pause it, speed it up and slow it down. Learn more about Read Aloud
Yes! You can use the Perlego app on both iOS and Android devices to read anytime, anywhere — even offline. Perfect for commutes or when you’re on the go.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app
Yes, you can access Pervasive Computing by Ciprian Dobre,Fatos Xhafa in PDF and/or ePUB format, as well as other popular books in Computer Science & Cyber Security. We have over one million books available in our catalogue for you to explore.