Pervasive Computing
Next Generation Platforms for Intelligent Data Collection
Ciprian Dobre, Fatos Xhafa, Ciprian Dobre, Fatos Xhafa
- 548 Seiten
- English
- ePUB (handyfreundlich)
- Über iOS und Android verfügbar
Pervasive Computing
Next Generation Platforms for Intelligent Data Collection
Ciprian Dobre, Fatos Xhafa, Ciprian Dobre, Fatos Xhafa
Über dieses Buch
Pervasive Computing: Next Generation Platforms for Intelligent Data Collection presents current advances and state-of-the-art work on methods, techniques, and algorithms designed to support pervasive collection of data under ubiquitous networks of devices able to intelligently collaborate towards common goals.
Using numerous illustrative examples and following both theoretical and practical results the authors discuss: a coherent and realistic image of today's architectures, techniques, protocols, components, orchestration, choreography, and developments related to pervasive computing components for intelligently collecting data, resource, and data management issues; the importance of data security and privacy in the era of big data; the benefits of pervasive computing and the development process for scientific and commercial applications and platforms to support them in this field.
Pervasive computing has developed technology that allows sensing, computing, and wireless communication to be embedded in everyday objects, from cell phones to running shoes, enabling a range of context-aware applications. Pervasive computing is supported by technology able to acquire and make use of the ubiquitous data sensed or produced by many sensors blended into our environment, designed to make available a wide range of new context-aware applications and systems. While such applications and systems are useful, the time has come to develop the next generation of pervasive computing systems. Future systems will be data oriented and need to support quality data, in terms of accuracy, latency and availability.
Pervasive Computing is intended as a platform for the dissemination of research efforts and presentation of advances in the pervasive computing area, and constitutes a flagship driver towards presenting and supporting advanced research in this area.
Indexing: The books of this series are submitted to EI-Compendex and SCOPUS
- Offers a coherent and realistic image of today's architectures, techniques, protocols, components, orchestration, choreography, and development related to pervasive computing
- Explains the state-of-the-art technological solutions necessary for the development of next-generation pervasive data systems, including: components for intelligently collecting data, resource and data management issues, fault tolerance, data security, monitoring and controlling big data, and applications for pervasive context-aware processing
- Presents the benefits of pervasive computing, and the development process of scientific and commercial applications and platforms to support them in this field
- Provides numerous illustrative examples and follows both theoretical and practical results to serve as a platform for the dissemination of research advances in the pervasive computing area
Häufig gestellte Fragen
Information
On preserving privacy in cloud computing using ToR
b Macquarie University, Sydney, NSW, Australia
Abstract
Keywords
1 Introduction
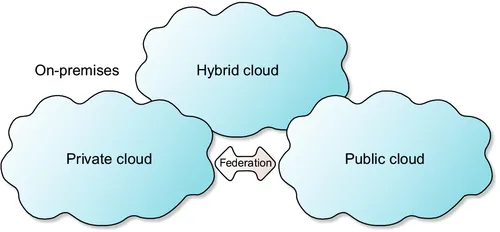
2 Overview of cloud computing