Cryptanalysis of Number Theoretic Ciphers
Samuel S. Wagstaff, Jr.
- 336 Seiten
- English
- ePUB (handyfreundlich)
- Über iOS und Android verfügbar
Cryptanalysis of Number Theoretic Ciphers
Samuel S. Wagstaff, Jr.
Über dieses Buch
At the heart of modern cryptographic algorithms lies computational number theory. Whether you're encrypting or decrypting ciphers, a solid background in number theory is essential for success. Written by a number theorist and practicing cryptographer, Cryptanalysis of Number Theoretic Ciphers takes you from basic number theory to the inner workings of ciphers and protocols.First, the book provides the mathematical background needed in cryptography as well as definitions and simple examples from cryptography. It includes summaries of elementary number theory and group theory, as well as common methods of finding or constructing large random primes, factoring large integers, and computing discrete logarithms. Next, it describes a selection of cryptographic algorithms, most of which use number theory. Finally, the book presents methods of attack on the cryptographic algorithms and assesses their effectiveness. For each attack method the author lists the systems it applies to and tells how they may be broken with it.Computational number theorists are some of the most successful cryptanalysts against public key systems. Cryptanalysis of Number Theoretic Ciphers builds a solid foundation in number theory and shows you how to apply it not only when breaking ciphers, but also when designing ones that are difficult to break.
Häufig gestellte Fragen
Information
Part I
Mathematical Foundations of Cryptanalysis
Chapter 1
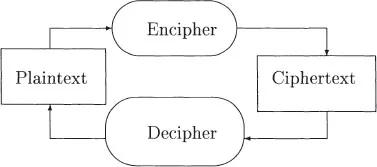
Terminology of Cryptography
1.1 Notation